The Koobface worm is not new to Internet users, but remains very active and continues spreading through different mediums using a variety of techniques. Last year, we have blogged about Koobface worm activity. We are still seeing this worm spreading via social engineering attacks. Attackers are creating fake malicious websites, which look like legitimate sites such as YouTube. Then, they lure the victim by posting fake content such as videos which actually lead to the downloading of malicious binary files. Look at the one of the site used to spread this worm using video content:
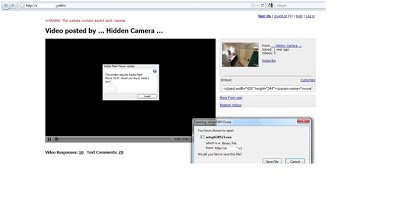 If you look at the image above, you will see the site is designed like a YouTube. The website shows a fake warning for adult material. The video displays a message saying “it requires Adobe Flash Player 10.37” and then forces a malicious file to download. In fact the latest version of genuine Adobe Flash Player is 10.2 but this video says 10.37 which is not a valid version. Once this file gets executed, it communicates with different servers. Here is the list,
If you look at the image above, you will see the site is designed like a YouTube. The website shows a fake warning for adult material. The video displays a message saying “it requires Adobe Flash Player 10.37” and then forces a malicious file to download. In fact the latest version of genuine Adobe Flash Player is 10.2 but this video says 10.37 which is not a valid version. Once this file gets executed, it communicates with different servers. Here is the list,- http://www.powertreecorp.com/.tqe1/?action=fbgen&v=120&crc=669
- http://www.bruleursdeloups.com/.gd1nlpq/?action=fbgen&v=120&crc=669
- http://www.waypoint-center.org/.vye770/?action=fbgen&v=120&crc=669
- http://sphusa.com/.wiqp6j2/?action=fbgen&v=120&crc=669
- http://reishus.de/.zfg35n/?action=fbgen&v=120&crc=669
- http://leonardandself.com/.uozs/?action=fbgen&v=120&crc=669
- http://iq-tech.biz/.8cww/?action=fbgen&v=120&crc=669
- http://careyadkinsdesign.com/.uzb62/?action=fbgen&v=120&crc=669
- http://top-friends.co.za/.zsm4/?action=fbgen&v=120&crc=669
- http://i-dare-you.co.za/.d38o8/?action=fbgen&v=120&crc=669
- http://fatucci.it/.hkly/?action=fbgen&v=120&crc=669
- http://www.flohr.tuknet.dk/.fav3bas/?action=fbgen&v=120&crc=669
- http://www.mx2.jellingnet.dk/.n9u39y5/?action=fbgen&v=120&crc=669
- http://www.neweed.org/.f8sh/?action=fbgen&v=120&crc=669
- http://hillsdemocrat.com/.uit970q/?action=fbgen&v=120&crc=669
- http://rentsatoday.com/.flyx4m/?action=fbgen&v=120&crc=669
- http://www.aicis.it/.zm1jpub/?action=fbgen&v=120&crc=669
- http://plymouth-tuc.org.uk/.eix02/?action=fbgen&v=120&crc=669
- http://lode-willems.be/.xokpra/?action=fbgen&v=120&crc=669
- http://www.cerclewalloncouillet.be/.s6ta/?action=fbgen&v=120&crc=669
- http://www.ilfrutteto.net/.8tsple/?action=fbgen&v=120&crc=669
Umesh





