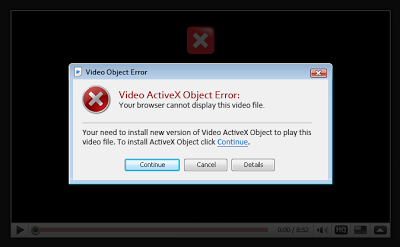
We've recently seen fake AV pages being replaced by fake video pages - malicious pages showing a Flash based video player, along with an error telling the user that he has to download a new codec to play the video. This is certainly not a new technique used by attackers, but it is interesting to see that these attacks are showing up on the same pages that were previously used to deliver a fake antivirus attacks.
Fake video page
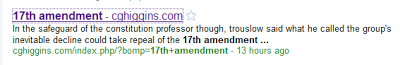
These malciious pages are accessed from spam SEO links on Google results. For example, hxxp://cghiggins.com/index.php/?bomp=17th+amendment appears on the first page for the search term "17th amendment", a popular search term on June 7th. This link redirects to the domain www2.realcleaner23p.co.cc. This domain name is typical of a fake AV page - it contains a term related to antivirus (clean) with a number, like virtually all such malicious domains that we've seen.
Spam link to the malicious domain
The title of the page is the same as the fake AV page: Security Threat Analysis. The source code is also similar - an HTML page with no content, and an external Javascript file that contains the visual elements as well as the malicious code. The user is prompted with an executable to download, which will install the "missing" codec in order to watch the video. This is of course a virus.
The malicious domain is not (yet?) blocked by Google SafeBrowsing, and no warning is displayed in the search results. The malicious executable is currently flagged by 10 antivirus vendors out of 41.
-- Julien