ユニバーサルZTNAを検討する主な理由
今、多くの組織がユニバーサルZTNAモデルのメリットに気付き始めています。企業がユニバーサルZTNAへの移行を進める主な理由は次のとおりです。
- 従来のアプライアンスからの脱却:UZTNAを採用することで、VPNなどの従来型のリモート アクセス アプライアンスを廃止し、完全にソフトウェアベースのアクセス制御ソリューションを活用できるようになります
- シームレスなユーザー エクスペリエンスの提供:UZTNAでは、ユーザーのトラフィックをデータ センター経由でバックホールしないため、ユーザーは必要なアプリケーションにダイレクトに高速アクセスできます。
- 一貫したセキュリティの確保:UZTNAは、オフィス勤務の従業員に対しても、それ以外の従業員に対しても、同一のゼロトラスト セキュリティ ポリシーを適用します。
- 簡単な拡張:クラウドZTNAサービスでは、ライセンスを追加するだけで簡単にキャパシティーを拡張できます。
- 迅速な展開:展開に数週間から数か月かかる他のソリューションとは異なり、UZTNAはどこからでもほんの数日で展開できます。
ZTNAとユニバーサルZTNAの違い
昨今、ITやセキュリティの業界では、多くのベンダーが「ゼロトラスト ネットワーク アクセス」を謳うソリューションを提供しています。しかし、その大半は従来のネットワーク マイクロセグメンテーションを用いて、柔軟性に欠けるオンプレミスのネットワーク セキュリティを展開するものです。こうしたテクノロジーでも、大まかに統合されたゼロトラスト ネットワーク アクセス制御に基づいてオフィス勤務のユーザーを保護できる可能性はありますが、適切なユニバーサルZTNAソリューションは、よりセキュリティ ファブリックに近いため、場所を問わずすべてのユーザーにゼロトラスト セキュリティを提供できます。
これは、ユニバーサルZTNAがクラウドネイティブなソリューションであり、一般的にセキュア アクセス サービス エッジ(SASE)またはセキュリティ サービス エッジ(SSE)フレームワーク上に構築されるためです。ユニバーサルZTNAでは、ユーザーの働く場所を問わず、最小権限の原則に基づいてアクセス許可を行います。オフィス、自宅、カフェなど、インターネットに接続できる環境であれば、あらゆる場所に対応します。
ネットワーク、SaaS、アプリケーションへのあらゆる場所からの安全な接続は、万能性に欠けるオンプレミスのフレームワークでは実現できません。ファイアウォールなどのオンプレミス アプライアンスを通じてゼロトラスト セキュリティを提供すると謳うソリューションがあるとすれば、それは真のゼロトラストではなく、決してユニバーサルZTNAとは言えません。こうした従来型のテクノロジーの多くは、コンテキスト、デバイス ポスチャー、場所ではなく、認証のみに基づいてアクセスを許可するためです。
また、こうしたテクノロジーの多くはパススルー アーキテクチャーを採用しており、インスペクションを行う前にトラフィックをネットワーク内に入れてしまいます。これは、本質的にゼロトラストの原則に反するものです。ユニバーサルZTNAは、暗黙の信頼を付与することなく、あらゆる場所のユーザーが、ネットワーク、SaaS、アプリケーションに安全にアクセスすること可能にします。これはクラウド ネイティブなZTNAならではの特長です。
ユニバーサルZTNAとVPNの違い
現在最も一般的に用いられている従来型セキュリティ ソリューションの1つであるVPNは、エンド ユーザーにネットワークへの安全なアクセスを許可して、指定されたトンネルを使用して(多くの場合SSOを通じて)会社のリソースにアクセスできるようにすることでアクセス管理を簡素化します。
1~2日のリモート ワークが必要な従業員に対しては、VPNは長年にわたり十分に機能してきました。しかし、より長期にわたるリモート ワークが広がり、やがて場所を問わない働き方が浸透するにつれ、拡張性に欠けコストやメンテナンスの負担が大きいVPNは、効果的なソリューションではなくなっていきました。さらに、パブリック クラウドの採用が急速に進んだことで、リモート ワーカーへのセキュリティ ポリシーの適用は従来以上に困難になり、ユーザー エクスペリエンスも損なわれていきました。
そして何より重大な問題が、VPNの使用によって生まれる攻撃対象領域です。SSOの認証情報さえあれば、あらゆるユーザーやエンティティーがVPNにログ オンし、ラテラル ムーブメントによってネットワーク内を自由に移動して、本来VPNが保護するはずのすべてのリソース、エンドポイント、データにアクセスできます。
ユニバーサルZTNAは、最小特権の原則に基づいて許可を行うことで、ユーザーによるアクセスを保護します。ゼロトラストでは、認証情報を基に信頼することなく、ユーザー、アイデンティティー、デバイス、場所といったすべての情報の整合性を確認し、コンテキストが適切な場合にのみアクセスを許可します。
また、ユニバーサルZTNAは、ネットワークへのアクセスではなく、リソースへのきめ細かいアクセスを提供します。ユーザーは、必要なアプリケーションやデータにダイレクトかつ安全に接続されるため、悪意のあるユーザーによるラテラル ムーブメントのリスクを排除できます。接続が直接行われることで、ユーザー エクスペリエンスも大幅に向上します。
ユニバーサルZTNA:ゼロトラスト原則の実装
ユニバーサルZTNAは、ユーザーのアイデンティティー、セグメンテーション、セキュア アクセス以外においても重要な意味を持っています。以下の3つの原則を核として、サイバーセキュリティ エコシステムを構築する基盤の戦略として機能します。
- すべての接続を終了:ファイアウォールなどのテクノロジーは、送信されてくるファイルを検査する「パススルー」アプローチを採用しています。悪意のあるファイルが検出されても、多くの場合警告は手遅れとなってしまいます。効果的なUZTNAソリューションはすべての接続を終了させ、暗号化されたトラフィックを含むすべてのトラフィックが送信先に届く前に、インライン プロキシ アーキテクチャーでリアルタイムに検査し、ランサムウェアやマルウェアなどの侵入を防止します。
- きめ細かなコンテキストベースのポリシーでデータを保護:ゼロトラスト ポリシーは、ユーザーのアイデンティティー、デバイス、場所、コンテンツの種類、要求されたアプリケーションなどのコンテキストに基づいて、アクセス要求と権利を検証します。ポリシーは適応性を備えているため、ユーザー アクセスはコンテキストが変化するたびに継続的に見直されます。
- 攻撃対象を排除することでリスクを低減:UZTNAでは、ユーザーは必要なアプリやリソースに直接接続され、ネットワークには接続されません。ユーザーとアプリ間またはアプリ間で直接接続が行われるため、ラテラル ムーブメントのリスクが排除され、侵害されたデバイスから他のリソースへの感染拡大を防ぎます。さらに、ユーザーやアプリはインターネットに対して不可視化されるため、発見および攻撃されることもありません。
ZscalerのユニバーサルZTNA
世界で最も導入されているZTNAプラットフォーム、Zscaler Private Access™は、Zscaler独自のゼロトラスト アーキテクチャー(ZTA)を基に構築されています。クラウドベースのZPAは最小特権の原則を適用し、ユーザーにプライベート アプリケーションへの安全な直接接続を提供しつつ、承認されていないアクセスやラテラル ムーブメントを排除します。クラウド ネイティブなサービスであるZPAは数時間で導入することができ、従来型のVPNとリモート アクセス ツールを総合的なゼロトラスト プラットフォームに置き換えます。
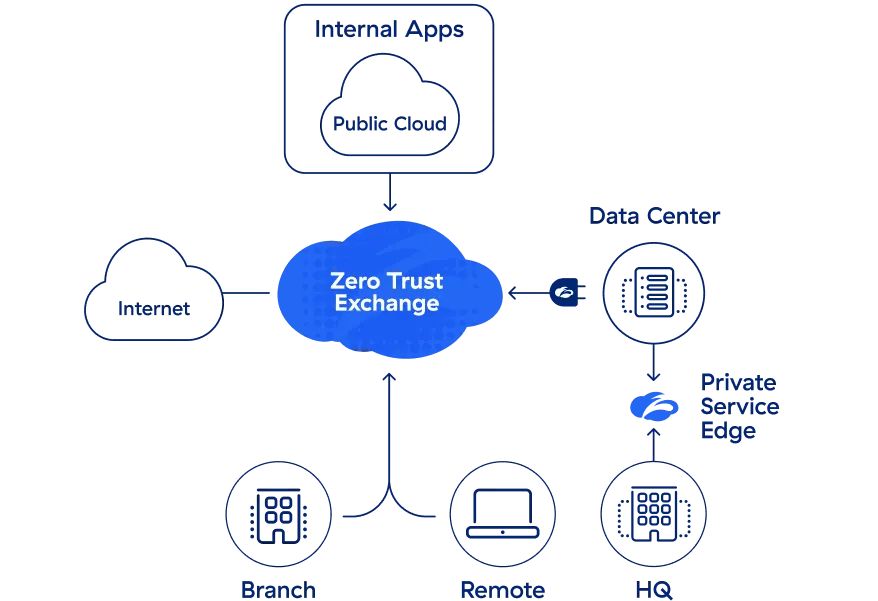
Zscaler Private Accessには、次のような特徴があります。
- 従来のVPNやファイアウォールを超える卓越したセキュリティ:ユーザーはネットワークではなくアプリに直接接続されるため、攻撃対象領域の最小化とラテラル ムーブメントの排除が可能になります。
- プライベート アプリの侵害を防止:インラインでのトラフィック検査と脅威対策、統合デセプション、脅威の分離の機能を備えた初のアプリ保護機能により、侵害されたユーザーによるリスクを最小限に抑えます。
- 現在のハイブリッド ワーカーに優れた生産性を提供:リモート ユーザーをはじめ、本社や支店、サード パーティーのパートナーに対し、プライベート アプリへの超高速アクセスをシームレスに提供します。
- ユーザー、ワークロード、デバイスに対応する一元的なユニバーサルZTNAを提供:最も総合的なZTNAプラットフォームを活用することで、従業員とパートナーはプライベート アプリ、サービス、OT/IoTデバイスに安全に接続できます。



