/ クラウド暗号化とは
クラウド暗号化とは
クラウド暗号化とは、プレーンテキストのデータを読み取り不可能な暗号文に変換し、クラウド環境内またはクラウド環境でのセキュリティを確保するデータ セキュリティのプロセスを指します。データ プライバシーを維持し、転送中または保存中のクラウド データをサイバー攻撃から保護する最も効果的な方法の一つです。場所や時間を問わずアプリケーションやデータにアクセスできるという性質はクラウドの大きなメリットですが、こうした広範なアクセスは特に機密データの漏洩リスクを大幅に高めるため、強固なデータ保護が欠かせません。その中でも、クラウド暗号化は極めて重要な要素となっています。
クラウド暗号化の仕組み
クラウド暗号化は、インターネット上を移動するデータやクラウド内に保存されている機密情報を保護する技術です。暗号化アルゴリズムは、あらゆる種類のデータを復号キーなしでは読み取れない形式に変換します。そのため、攻撃者がデータを傍受または流出させたとしても、復号できなければ意味のない情報となります。
クラウド暗号化は、主に以下の2つの状態にあるデータを保護します。
- 転送中データ:安全でないネットワーク外を移動することが多く、特に脆弱になりやすいデータ
- 保存データ:クラウド ストレージやデータ センターのサーバーなどに保存されていて、使用中でも移動中でもないデータ
現在、標準的なHTTPSのWebトラフィック暗号化には、Transport Layer Security (TLS、旧称SSL)プロトコルが使用されており、各データ パケットの安全性が確保されています。信頼できるユーザーやエンティティー(多要素認証などで確立)が暗号化されたデータへのアクセスを要求すると、そのデータは暗号化された状態で送信され、復号キーを使用して初めて利用可能な状態になります。
データ暗号化の基本的な2種類の方式
すべてのクラウド暗号化サービスとプロトコルは、対称暗号化と非対称暗号化の2種類に大別されます。
対称暗号化
対称暗号化では、平文の暗号化と暗号文の復号に同じ鍵を使用します。簡単な例として、「cat」という単語の各文字をアルファベット順で4文字先にずらして「gex」に変換した場合、逆に4文字戻せば元の「cat」に復号できます。
Advanced Encryption Standard (AES)やTLS (後述のとおり非対称暗号化でも使用可能)といった対称プロトコルは、以下の理由から広く使用されています。
- 十分に複雑で高い安全性:AESを総当たり攻撃で破るには数十億年かかると言われている
- 十分にシンプルで高速:大規模なデータセットや大量のトラフィックに適している
ただし、この単一キー方式は、漏洩のリスクが高くなります。たとえば、暗号化キーをインターネット経由で送信する必要がある場合、攻撃者に傍受されて暗号化データが露見するおそれがあります。
非対称暗号化
非対称暗号では、公開鍵と秘密鍵のペアを使ってデータの暗号化と復号を行います。これは暗号付きの南京錠のようなもので、だれでも施錠(公開鍵での暗号化)できますが、コードを知っている人(秘密鍵の所有者)しか開錠できません。
楕円曲線暗号(ECC)やデジタル署名アルゴリズム(DSA)、TLSなどの非対称暗号方式が現在使用されている理由は、以下のとおりです。
- 低い漏洩リスク:公開鍵が漏れても秘密鍵は守られ、秘密鍵を送信する必要もないためリスクが低い
- 認証手段としても機能:送信者が秘密鍵でファイルに署名することで、受信者に正当な送信元であることを証明できる
ただし、対称暗号化に比べると、非対称暗号化は一般的に処理速度が遅いという欠点があります。
クラウド暗号化のメリット
クラウド暗号化は形式を問わず、以下のような重要なメリットを提供します。
- 強化されたサイバーセキュリティ:データの保存場所や状態(転送中、保存中、クラウド上、またはエンド ユーザーのデバイス上)にかかわらず、データ漏洩を防ぎ、機密情報を保護します。
- 厳格なコンプライアンス対応:HIPAA、PCI DSS、FIPSなどの規制基準の暗号化要件を満たします。
- リスクの低減:すべてのデータが暗号化されていた場合、一部の情報漏洩は報告義務の対象外となる可能性があります。
- 信頼性とプライバシーの強化:データの取り扱いにおいてプライバシーを最優先し、効果的な暗号化を実装することで、組織やブランド、製品への信頼を強化できます。
Google Transparency Reportによると、2024年1月時点で、米国におけるChromeのページの96%がHTTPS経由で読み込まれています。
クラウド暗号化が必要なシナリオ
何を、いつ暗号化するかは、データの性質とセキュリティ要件によって異なります。たとえば、医療保険の相互運用性と説明責任に関する法律(HIPAA)や、クレジット/デビットカードの取引を扱う事業者に適用されるペイメント カード業界データ セキュリティ基準(PCI DSS)は、それぞれの分野でデータ暗号化を義務付けています。これらの規制に違反すると、罰金や法的責任が発生する可能性があります。さらに、米国の連邦情報処理標準(FIPS)など、世界各国においてさまざまな政府規制が存在しています。
コンプライアンス フレームワークはデータ侵害のリスクを軽減するためのものですが、それでもデータ侵害の事例は後を絶ちません。これは、クラウドの導入形態やプロバイダーごとに適用される規制が異なり、ポリシーや脆弱性も異なるためです。つまり、強固なクラウド セキュリティを維持するには、データの具体的なセキュリティ要件にかかわらず、可能な限り多くのデータを暗号化することが最善策です。
実例:Equifaxの情報漏洩
2018年、信用情報機関Equifaxで発生した情報漏洩により、1億4,800万人以上の個人識別情報(PII)が流出しました。しかし、暗号化とトラフィック検査が適切に行われていれば、データ侵害のリスクと影響を大幅に低減できた可能性があります。
この漏洩は10か月もの間発見されませんでした。その理由は、サイト証明書の有効期限切れにより暗号化されたトラフィックが検査されずに通過していたためであり、攻撃者は暗号化接続を使って顧客データを外部に持ち出しても検知されなかったのです。さらに、データがアップロード前に暗号化されていれば、攻撃者が入手できたのは判読不可能な暗号文だけだったはずです。
暗号化トラフィックの検査が重要な理由
データの暗号化は非常に重要ですが、検査をしないと、セキュリティに盲点が生じるおそれがあります。
Google Transparency Reportによると、世界中でGoogleへの通信の90%以上が暗号化されています。これは機密データの保護に役立つ一方で、攻撃を隠す手段にもなり得ます。実際、Zscalerの調査では、現在、87%以上の攻撃が暗号化されたチャネルを通じて行われていることが明らかになっています。
技術的な制約と運用上の課題
リスクがあるにもかかわらず、多くの組織では暗号化されたトラフィックの大部分を復号、検査しておらず、セキュリティ上のリスクを抱えたままとなっています。その主な理由として、以下の3つが挙げられます。
- 完全な検査には莫大な処理能力が必要になる:クラウド コンピューティングの急速な普及により、インターネット上のトラフィックはこれまで以上に増加しており、この問題をさらに深刻化させています。多くの組織では、性能とセキュリティを同時に実現できるだけの処理能力を備えていない旧式のセキュリティ ハードウェアを使用しているのが現状です。
- 「信頼された」トラフィックを検査しない:GoogleやMicrosoft、AWSなどのサービス プロバイダーは独自の情報セキュリティ管理を実施しているため、多くの組織がそのトラフィックを信頼し、検査を省略してしまう場合があります。しかし攻撃者はこの傾向を巧みに利用し、こうしたプロバイダーからのトラフィックを悪用してターゲット環境に忍び込む手口が多く見られます。
- 一部のベンダーは限定的な復号をベスト プラクティスとしている:前述の両点に関連して、処理能力に制限のあるファイアウォール ハードウェアのベンダーは、「高リスク」なURLカテゴリーのトラフィックのみを復号し、それ以外は信頼するという手法を推奨しています。この手法がもたらすリスクについては、以下の図をご覧ください。
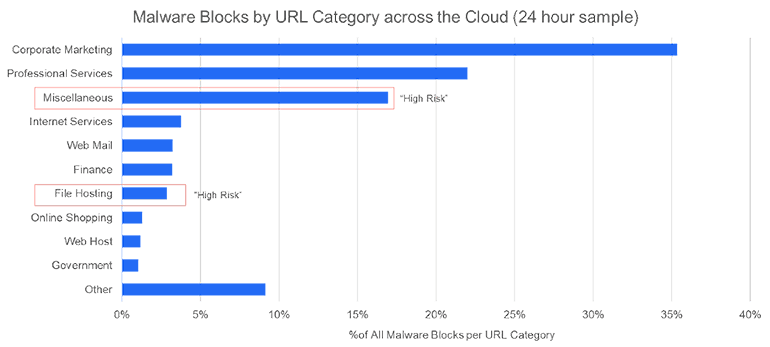
詳細については、SSLインスペクションには慎重な対応と責任が必要(英語)をご覧ください。
クラウド暗号化と検査の現状
近年、Webトラフィックの量が急激に増加しています。オンプレミスのセキュリティ ソリューションを適切にアップグレードしていない組織では、サイバー攻撃のリスクが高まり、SaaSやクラウド全体のパフォーマンスが低下する可能性があります。場合によっては、これらの課題が同時に発生することもあります。
同時に、クラウド ストレージ プロバイダーやクラウド サービスが急速に普及していますが、セキュリティ責任のバランスはサービスの種類によって大きく異なります。
さらに、多くの新しいクラウド プロバイダーやサービスが登場するにつれ、従来のプロバイダーは、当初想定されていなかったユース ケースでも自社サービスを「十分に安全に」利用できるようにするための推奨事項を提供しています。
しかし、問題はこの「十分に安全」という考え方にあります。攻撃が増加している今こそ、「可能な限り安全に」という姿勢を重視する必要があります。リスクを最小限に抑え、コストを削減するには、ソースに関係なくすべてのトラフィックを復号、検査、再暗号化できるスケーラブルな検査ソリューションが必要です。こういった機能がなければ、セキュリティ コストの負担が増えるだけでなく、安全性が確保されず、深刻なリスクにさらされるおそれがあります。
Zscalerとクラウド暗号化
Zscaler Internet Access™ (ZIA™)は、Zscaler Zero Trust Exchange™プラットフォームの一部として、パフォーマンスに影響を与えることなく、暗号化トラフィックを含むすべての通信をクラウドならではの規模で検査します。このクラウド ネイティブなサービスは、先進的なクラウド プロキシ アーキテクチャーを活用し、あらゆる宛先やユーザーとの通信を完全に復号、検査、再暗号化することで、暗号化チャネルに潜む脅威からユーザーと組織全体を保護します。



