hxxp://27glshegbslijels.ce.ms/main.php?page=66c6ce3c7bc4b20c
hxxp://hhhjjjjj111111.ce.ms/main.php?page=423b262d0a1a9f70
hxxp://00000000000000.ce.ms/main.php?page=423b262d0a1a9f70
hxxp://24sjegohmjosee.ce.ms/main.php?page=66c6ce3c7bc4b20c
hxxp://44444444444444444.ce.ms/main.php?page=423b262d0a1a9f70
The aforementioned domains suggest that random domain names are being registered to host these attacks. Once visited, the victim will be presented with obfuscated JavaScript code, formatted in such way to evade IDS, IPS and antivirus solutions. The numbers in the arrays used by the scripts are intentionally spread across separate lines. This way the size of HTML file becomes huge and the total code spans 29K lines. Here is the snapshot of the first part of the malicious code: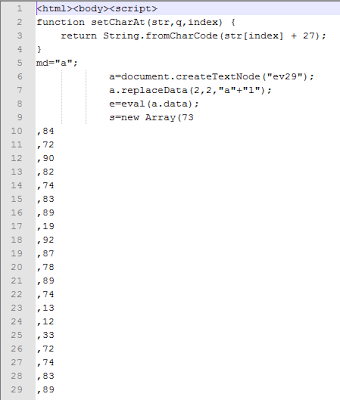
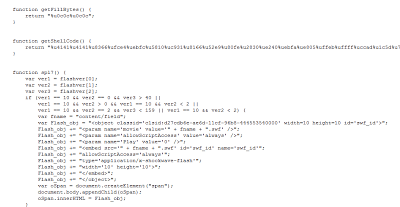 Attackers keep registering different random domains to spread their attacks, often targeting free registration services. Due to obfuscation used by the attackers, security solutions relying on regular expressions designed to match known patterns can often be evaded due to the code being spread of over numerous lines.
Attackers keep registering different random domains to spread their attacks, often targeting free registration services. Due to obfuscation used by the attackers, security solutions relying on regular expressions designed to match known patterns can often be evaded due to the code being spread of over numerous lines.Umesh