[UPDATE] After further analysis, this threat was identified as Asprox botnet and not Zbot
Asprox is an extremely venomous threat, which has strong persistent tactics to ensure that the victim remains infected despite removal attempts. We will get to the overabundance of methods used to keep the victim infected later on. First, I'll share some of the latest download locations for this threat, which researchers should take note of:
- hxxp://king-orbit[.]com/libs11.18/ajax/
- hxxp://message-tvit[.]com/libs17.19/ajax/
- hxxp://bidcos-fact[.]com/libs20.17/ajax/
- hxxp://vespula-grants[.]com/libs31.56/jquery/
- hxxp://bee-smoka[.]com/libs29.89/ajax/
The bulk of these threats are tied to a server found in Russia: 88[.]85[.]215[.]129.
Reminiscent of other malicious infections, the second the threat is run, it deletes itself in order to hinder researchers when conducting a reverse engineering analysis of the attack. The next step is to create a Security Center Task in Windows, to ensure that even if the threat is removed, it will reoccur.
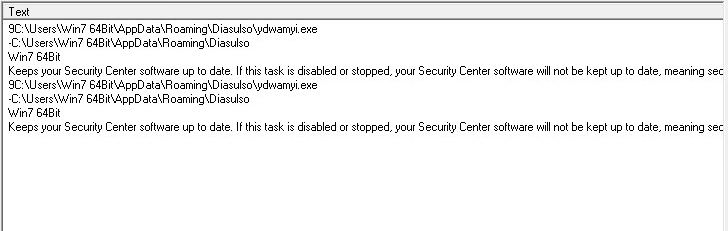 |
| The filename is randomly generated. |
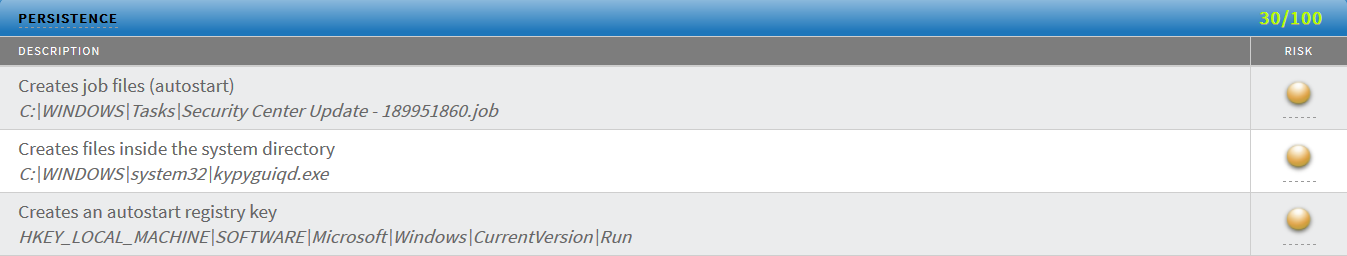 |
| Note the filename of the .job file, which is dropped on the victim's machine. This name is randomly generated. |
In addition to ensuring that the threat restarts if the victim were to reboot, it also disables key Windows processes to hinder removal of the threat. This includes disabling Safe Boot registry keys.
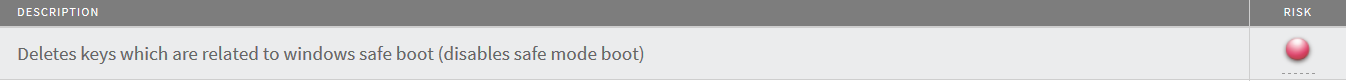 |
| This disables users access to boot into Safe Mode to run standard AV solutions. |
Once installed and hooked into the victim's environment, it begins the task of phoning home to its Command & Control (CnC) location for tasks to complete. Periodically, it will receive a GET request from the CnC to make sure that the victim is still listening.
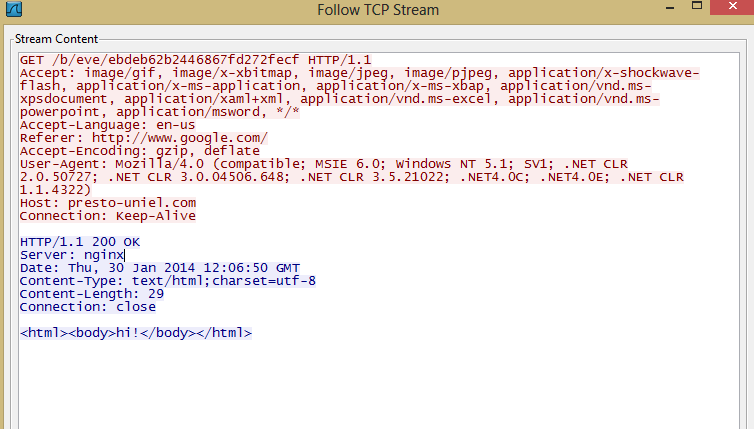 |
| Hi! to you too. |
Given the stealth tactics employed by this threat, you may not be aware of the infection straight away. You may however become suspicious when you start to feel the drag on your Internet connection. Behind the scenes, the threat is actively reaching out to several different ad servers as a means to promote ad revenue for the attacker. Below is only a portion of the servers that were contacted in the course of a few minutes.
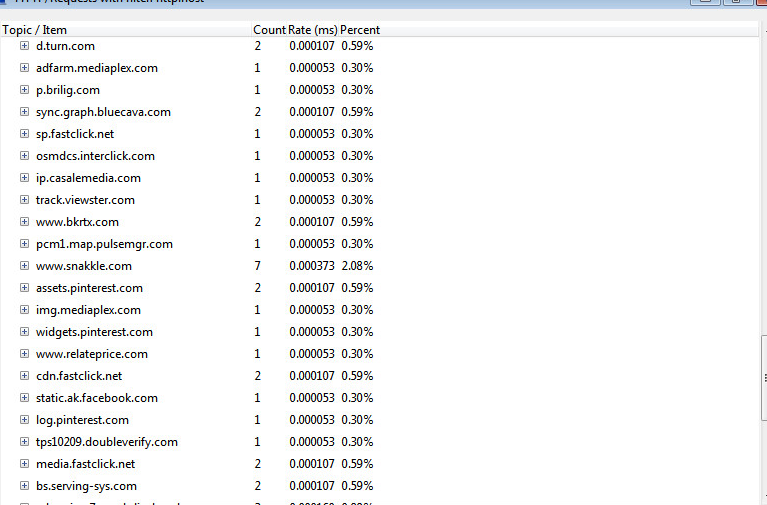 |
| All transactions do not take place in the browser, but behind the scenes. |
Administrators concerned for their user's safety should take note of usage patterns. It won't be difficult to spot a user sending out absurd amounts of ad traffic. You can either look through your logs for large amounts of advertisement traffic OR find HTTP POST requests with the string '/b/opt/' in the URI path.
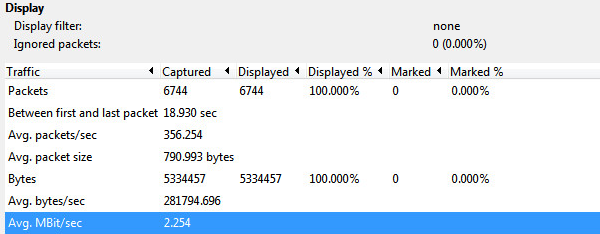 |
| 2.254 Mbps!!! |
While this threat is persistent, it is easy to spot from a Network Administrator's point of view. The information provided should be enough to find your infected users to take them off of the network until remediation of the threat can be completed.
Mind Your Clicks.












