Stop me if you’ve heard this one before. I’m telling a new acquaintance that I work in IT, particularly the security sector.
“Neat…so my computer has been running slow recently…”
I want to make a good impression so I schedule some time and roll up my sleeves for however long it may take. Given that this is someone else’s PC, I’m not going to risk plugging in any of my personal equipment to their network. Instead I’ll be using only free tools that I tend to use when cleaning a PC I don’t own. Wireshark, Bintext, Proexp are good enough starters and will help me diagnose anything I’ll need to without digging in too deep.
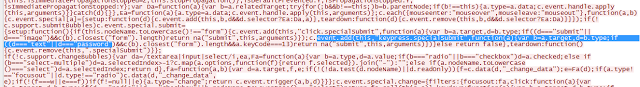
First thing you want to do when looking for something malicious on a friend’s PC is check if it is actively communicating. I fired up Wireshark and started sniffing for common things which might be getting leaked out. Sure enough…There is a worm actively looking for new computers on the network. From a glance you can tell that it would like nothing better than to hook itself into explorer for the purposes of keylogging.
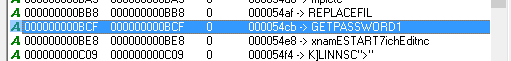
Once you have a good idea about where this malicious file is hooked into, it’s a relatively simple to go to that process using ProExp and dump the malicious thread from memory. Sure enough attached to IEEXPLORE.EXE is something called “Postcards.exe”. One memory dump later and I think we may have found our culprit.
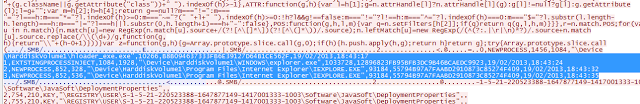
Prior to beginning this exercise, I had set the Windows Firewall to essentially block all communication from going out aside from SMB. It’s a good thing I did that too because this bad guy was interested in much more than just passwords. It is also looking to profile my computer for insertion into a botnet. A leading suspicion of this activity is due to the high volume of POST requests being made to .ru sites.
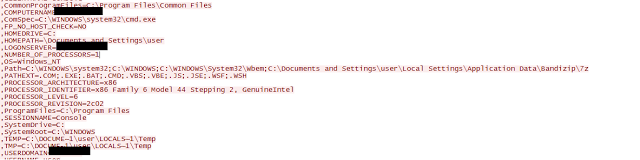
Once it has spec-ed out my PC, it’s time to tell the mother ship that we have another zombie ready for the herd. In the time I let it run, it attempted to send out information to the different sites using the same format:
hxxp://www.xxxxxxxxxxxx.ru/enabling/update.jsp?password=xxxxxx&version=1.0
Eventually, I just installed a few different Anti-spyware cleaning products on the PC to clean it up. When dealing with a worm this feisty, it’s a good idea to separate the nodes and clean them up one at a time if this ever happens to your personal network.