Zertsecurity is a well known banking Trojan based on phishing schemes targeting German Android users. Lets see how it works.
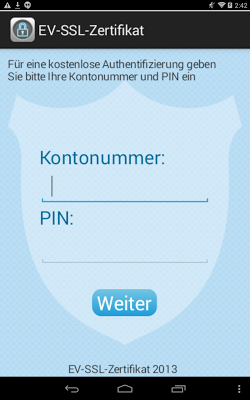
After installing the application, it prompts the user for account and PIN numbers.
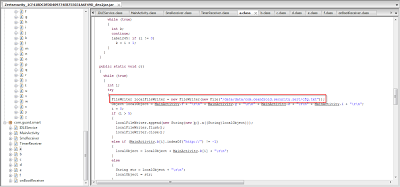
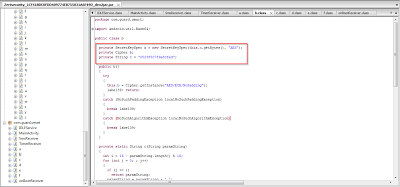
The application takes the values of the account and PIN numbers via input boxes and saves them to the cfg.txt file. It then sends this file to a remote command and control (C&C) server master.
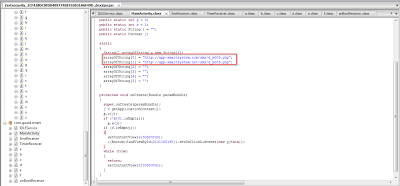
You can see the hardcoded C&C server in the application.
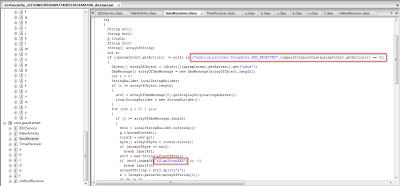
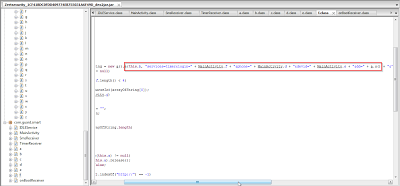
Also here you can see that the application is also asking for SMS receive permissions. It receives SMS messages from it's C&C server for commands to perform malicious activities. It also checks for the string “&Sign28tepXXX” in order to identify commands from the C&C server.
Here you can see that the application is using AES and BASE64 encoding techniques for encryption.
In this screenshot you can see the C&C messages being assembled.
Zertsecurity is a simple banking Trojan which was constructed for targeting phishing attacks against German Android users. It prompts for an account number and PIN, stores them in the cfg.txt file after encrypting the information using AES and base64 encoding algorithms. It also receives SMS from a hard coded C&C server for additional instructions.
References: