Recently, I found several legitimate sites, with bad coding practices, used to redirect users to spam sites with the help of URL shorteners. Here is how the scam works:
fmcsa.dot.gov
One example of such redirection pages is http://www.fmcsa.dot.gov/redirect.asp?page=https://www.zscaler.com/. Change https://www.zscaler.com/ to any URL. I've seen this page used to redirect to the rogue pharmacy canadapharm.org.
The redirection is not done by the standard Meta refresh tag (meta http-equiv="refresh" content="6;url=https://www.zscaler.com/"), but by custom JavaScript. Even if the URL shortener was looking at the HTML content to figure out the final destination, it would very likely not haven seen the redirection to an external domain.
XSS
In addition to being used by spammers, fmcsa.dot.gov includes a cross-site scripting vulnerability: the link can be used to execute any JavaScript. The screen shot below was taken for the URL http://www.fmcsa.dot.gov/redirect.asp?page=javascript:alert%28document.cookie%29;
Unchecked redirections is yet another security flaw that developers need to keep in mind when developing a website. Having a website widely used for spam will likely get it blocked by Google Browsing and other security and spam denylists, preventing users to access any page on the website unless they dare ignore the scary warning message from their browser.
-- Julien
- The legitimate sites have a warning page for all links to external sites (i.e. http://good.com/redirect?url=http://example.com/)
- The warning page can be used to redirect users to any domain, including spam sites and malicious pages (i.e. http://good.com/redirect?url=http://spam.com/)
- Spammers use a URL shortener like bit.ly to hide the long URL (i.e. http://bit.ly/aaaa redirects to http://good.com/redirect?url=http://spam.com/ which redirects users to http://spam.com/)
fmcsa.dot.gov
One example of such redirection pages is http://www.fmcsa.dot.gov/redirect.asp?page=https://www.zscaler.com/. Change https://www.zscaler.com/ to any URL. I've seen this page used to redirect to the rogue pharmacy canadapharm.org.
The redirection is not done by the standard Meta refresh tag (meta http-equiv="refresh" content="6;url=https://www.zscaler.com/"), but by custom JavaScript. Even if the URL shortener was looking at the HTML content to figure out the final destination, it would very likely not haven seen the redirection to an external domain.
XSS
In addition to being used by spammers, fmcsa.dot.gov includes a cross-site scripting vulnerability: the link can be used to execute any JavaScript. The screen shot below was taken for the URL http://www.fmcsa.dot.gov/redirect.asp?page=javascript:alert%28document.cookie%29;
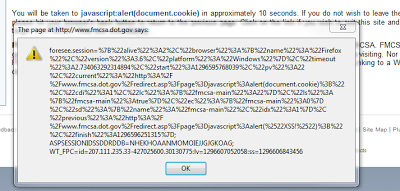 |
| Cross-Site scripting on fmcsa.dot.gov |
Unchecked redirections is yet another security flaw that developers need to keep in mind when developing a website. Having a website widely used for spam will likely get it blocked by Google Browsing and other security and spam denylists, preventing users to access any page on the website unless they dare ignore the scary warning message from their browser.
-- Julien





