Overview
This is the eighth in a series of blogs by the Zscaler ThreatLabZ research team collecting and analyzing the recent activity of the top exploit kits. Exploit kits (EKs) are rapidly deployable software packages designed to leverage vulnerabilities in web browsers and deliver a malicious payload to a victim’s computer. Authors of EKs offer their services for a fee, distributing malware for other malicious actors. What follows are highlights from the EK activity we observed during the last quarter.
RIG Exploit Kit
RIG EK has been the most active exploit kit, but its activity has decreased in comparison with previous quarters. We can see minimal RIG EK activity in the month of January, but it picked up again in the second half of April. We are seeing different payloads delivered by RIG this quarter, and they varied from ransomware and banking Trojans to crypto mining software—as opposed to its more typical payload of Cerber ransomware. Below we can see the hits for RIG EK activity.
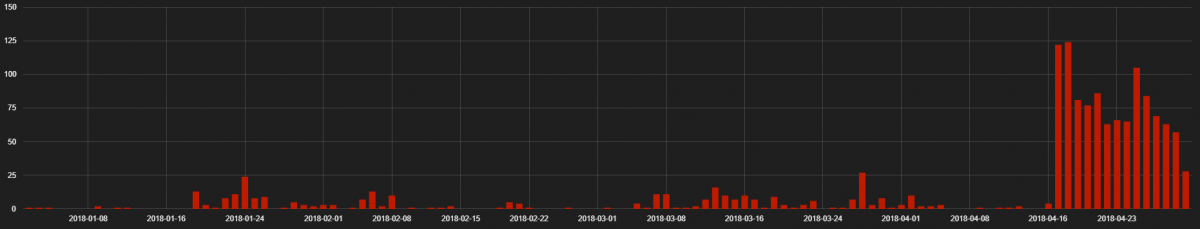
Fig 1: RIG EK Hits from 1st Jan 2018 to 30th April 2018.
The geographical distribution of the hits is shown below.
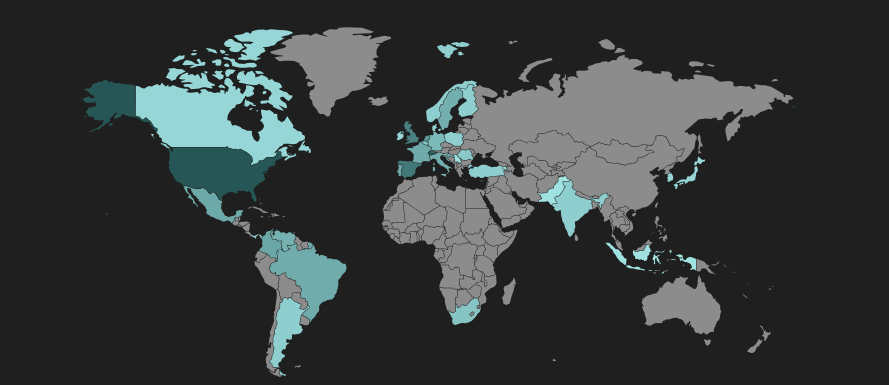
Fig 2: RIG EK Heat Map showing infected regions.
Most infection attempts are seen in the United States, Spain, and Switzerland this quarter, while last quarter, activity was only observed in the United States and Russia.
The most common RIG EK redirects were observed from illegal streaming websites, which provide users with free, live sports feeds. The malvertising on these websites fingerprints a user's machine, as per the attacker's configuration on the Traffic Distribution Systems; the most recently active one is Black TDS. An example of such a streaming domain is nba-stream[.]online, which sends users to malvertising domains like www.ligtv-izle[.]net/ads/ad2.html. The RIG EK cycle that follows is shown below.
Fig 3: RIG EK Infection cycle.
There were common patterns observed in the RIG EK landing page URLs, which would change on weekly basis, but the landing page content has remained mostly unchanged.
Fig 4: RIG EK landing page URLs with common parameters.
The obfuscated RIG EK landing page is shown below.
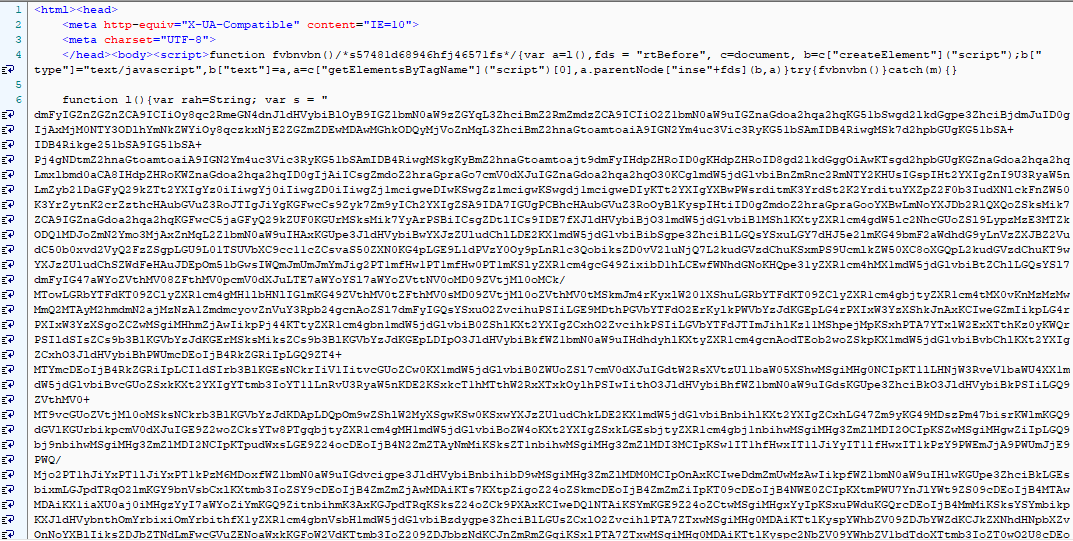
Fig 5: RIG EK Obfuscated landing page.
One significant change is the inclusion of the CVE-2018-4878 Adobe Flash vulnerability, which affects Adobe Flash Version 28.0.0.137 and earlier versions.
When we open the downloaded Flash file using a decompiler, we found the section of the pointer to the listener object, which is responsible for this vulnerability. This is highlighted in the image below.
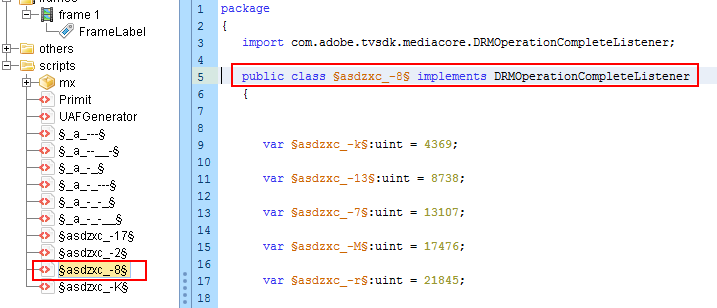
Fig 6: RIG EK Flash with CVE-2018-4878
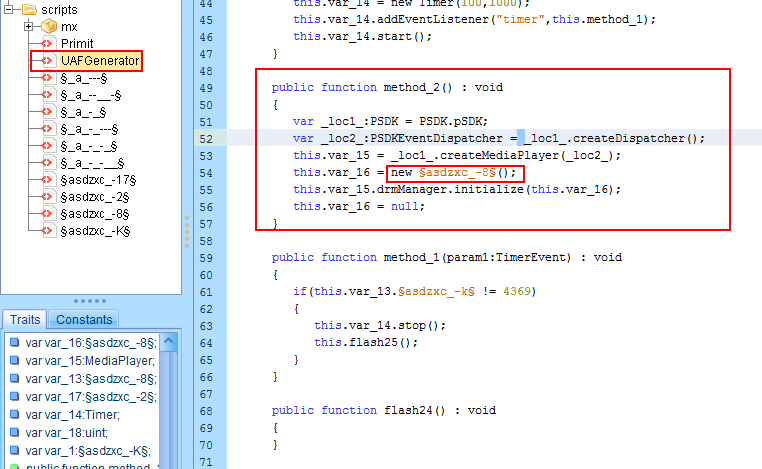
Fig 7: RIG EK Flash with CVE-2018-4878
We saw the RIG EK downloading GandCrab ransomware instead of the usual Cerber ransomware. Other payloads we saw included cryptocurrency miners, along with Trojans like Bunitu and Ramnit.
GrandSoft Exploit Kit
GrandSoft Exploit Kit is an old exploit kit that has become active again. This EK consists of simple JavaScript redirects without any obfuscation. The landing page was seen serving CVE-2016-0189, which is a scripting engine memory corruption vulnerability.
The GrandSoft EK activity hits are shown below.
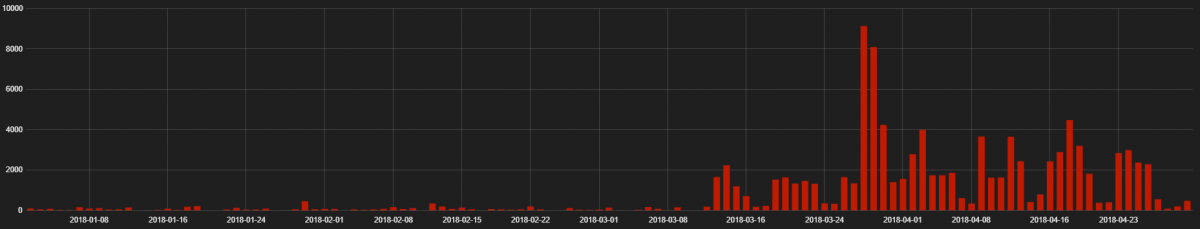
Fig 8: Grandsoft EK Hits from 1st Jan 2018 to 30th April 2018
The geographical distribution of the hits can be seen below.
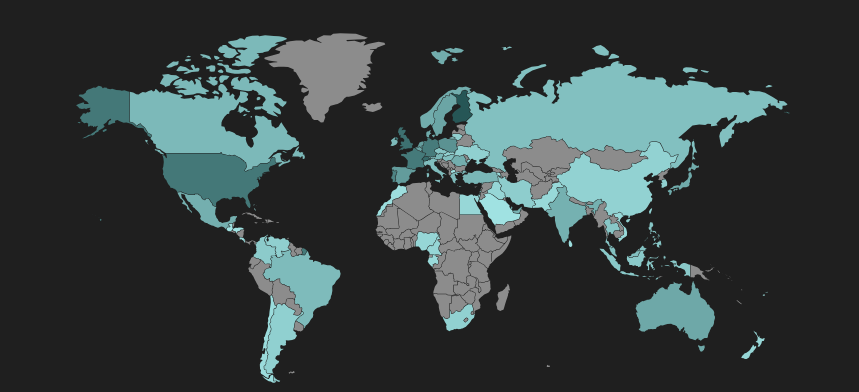
Fig 9: Grandsoft EK Heat map showing infected regions.
GrandSoft EK redirects were seen from malvertising chains and the hits are distributed globally. The EK does not seem to be targeting any specific geographic region.
The GrandSoft EK cycle can be seen below.
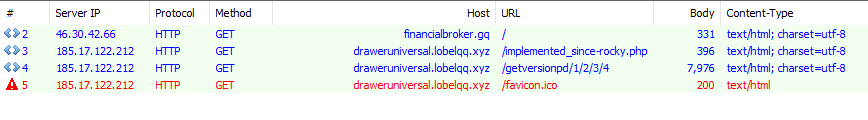
Fig 10: Grandsoft EK cycle
We see that the gate contains a simple JavaScript redirect, as shown below.
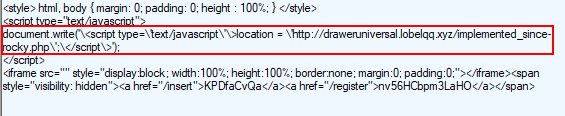
Fig 11: GrandSoft EK Javascript Redirect
This call loads another JavaScript-based redirect to the landing page.
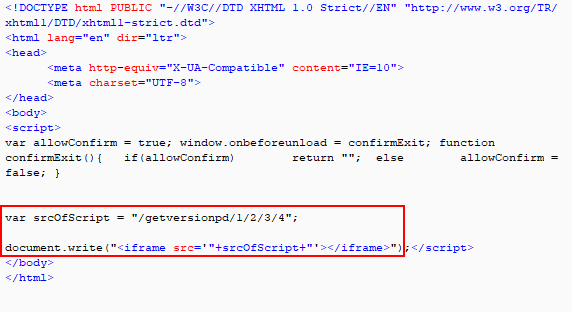
Fig 12: Grandsoft EK Landing page redirect
The landing page snippet with the CVE-2016-0189 code is shown below.
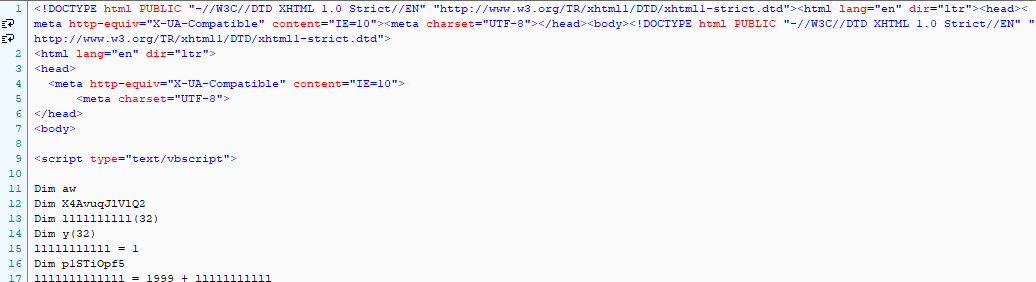
Fig 13: Grandsoft EK Landing page with CVE-2016-0189
The payload seen in this cycle was GandCrab ransomware; this can be seen in the temp directory of the infected machine.
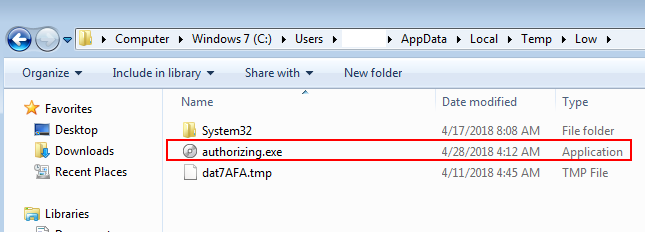
Fig 14: Grandsoft EK downloads GandCrab ransomware to the victim machine.
Other exploit kits
Magnitude EK activity was observed this quarter, but it was targeted in South Korea. The EKs that were showing reduced activity in the last quarter, such as Terror EK, Disdain EK, and Kaixin EK, are no longer showing any activity.
Conclusion
Exploit kits are effective, as they can infect a victim's machine during web browsing without the user's knowledge. The attackers monetize the successful infections by collecting a ransom for retrieving data encrypted by ransomware, mining cryptocurrencies using the victim's system resources, or installing banking Trojans to steal a victim's identity. Attackers frequently change their techniques by obfuscating the source code or integrating new exploit code into their EK, and security researchers analyze and block the new threats by tracking changes in the EK behavior.
To help avoid infections from exploit kits, users should always block untrusted third-party scripts and resources, and avoid clicking on suspicious advertisements. Keeping the browser plugins and web browsers up to date with latest patches helps to protect against common vulnerabilities targeted by exploit kits. The Zscaler ThreatLabZ research team has confirmed coverage for these top exploit kits and subsequent payloads, ensuring protection for organizations using the Zscaler cloud security platform.





