Introduction
Malware authors use various means to make their malware look similar to legitimate software. One such approach involves signing a malware sample with a digital certificate. Recently we saw Dridex malware authors using this technique while reviewing the samples in our Cloud Sandbox. Dridex is a banking Trojan which typically arrives to a system via malicious spam email with a Microsoft Office file as an attachment. These files will have embedded macros that lead to the download and installation of the Dridex Trojan. Dridex then attempts to steal the victim's banking credentials and system information.
Signed Dridex campaign
Here we came across one malicious attachment with an encrypted macro that downloads signed Dridex samples from 81.17.28.101/bt/bt/sti[.]php. This Dridex sample is packed using a custom packer, which is is compiled with .NET. The current Dridex is signed with a certificate that is issued to
Private Person Parobii Yuri Romanovich. This certificate as been specially created for spreading the Dridex malware.
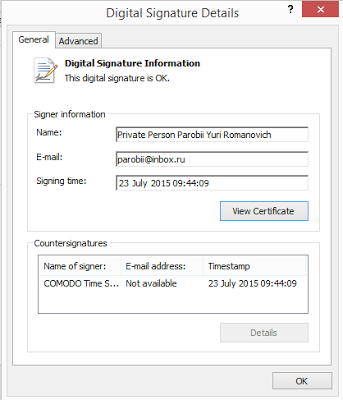 |
| Certificate |
We also saw the following signer information in the certificates used for signing the Dridex executables:
- PJSC "BIZNES AVTOMATYKA
- AVTOZVIT Scientific Production Private Company
- Private Person Parobii Yuri Romanovich
The certificates were all issued by COMODO and we observed the following URLs serving the signed Dridex malware:
- 185.14.29.214/bt/bt/sdp [.] php
- 81.17.28.101/bt/bt/sti [.] php
- 5.196.241.204/bt/bt/ched [.] php
- 217.12.203.171/bt/bt/freda [.] php
- 94.250.252.13/bt/bt/stata [.] php
- 149.202.146.176/bt/bt/chdid [.] php
- 93.170.105.60/bt/bt/grtes [.] php
Below are the Dridex samples served from the aformentioned URLs. All tof he samples are packed with the same .NET packer mentioned above:
- 5CA1DBA1C72AC999E221DE98BBC584C4
- 9E73E0C4B92253C5F8B6648F29B28B5B
- CD243B30B9BBD682C082CFEFDBF79ACD
- E578618F2D38FC251D52D1366144404F
- 5F907702CE229937955B4DCE92EC4575
- DC443FBB5FB6125EBEEEBEC2E4BAA372
- 0BBC8CD08E9958ACDE0519A2B2840CD7
- 9D1D0632329F04D8B1EC21AFF4CE6493
- 32230D747829DCF77841F594AA54915A
- 8F1A9A9830FF02C5C2BA4C17DFE8B09D
- 00DCA835BB93708797A053A3B540DB16
- 393E2145F4C3E9B5697A2AAEB25AA8D3
- 1992170FDC642D4A99A7BC82BA82FA31
- 9261B8EAF1DA3D9CFF522875A7198667
- FB67C85F3F42D3E48B9E7B7637D30858
- E578618F2D38FC251D52D1366144404F
Dridex Packer:
The Dridex sample is embedded in the resource section of the packer. After unpacking, it drops a Borland Delphi executable file. The following is the snapshot of encrypted resource section:
 |
| Encrypted Resource Section |
Dridex Activity:
The current Dridex sample tries to connect to different IPs included in the config file. The config file for the sample is embedded in the sample itself. In the config file we observed a botnet ID and list of C&C servers. Below is a snapshot of config file:
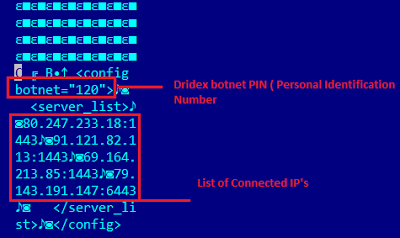 |
| Configuration file | |
Dridex collects and sends the following system information to one of the C&C mentioned in the config file:
- Computer Name
- User Name
- Windows Version
- Botnet ID
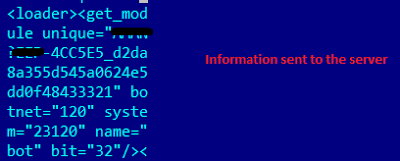 |
| Information sent to the server |
Below is the complete list of C&Cs it tries to connect.
- 80.247.233.18
- 91.121.82.113
- 69.164.213.85
- 79.143.191.147
- 199.241.30.233
- 162.243.12.14
- 188.93.73.90
- 195.154.184.240
Conclusion
The use of a legitimate certificate in signing malware executables to evade security detection is not new but is still very effective. The malware author aims to exploit the Code-Signing Certificate based allowlist approach by signing their samples. Zscaler ThreatlabZ is actively monitoring these signed malware campaigns and ensuring coverage for our customers.
Analysis by Tarun Dewan and Nirmal Singh










