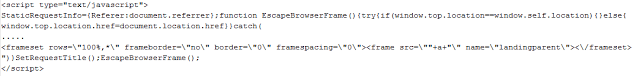
Today we have a perfect storm of basic attack vectors which inevitably lead victims to a variety of advertising scams including adware executables, parked domains, pay-per-click scams or phishing sites. First a small list of all of the websites seen to be hosting this threat.
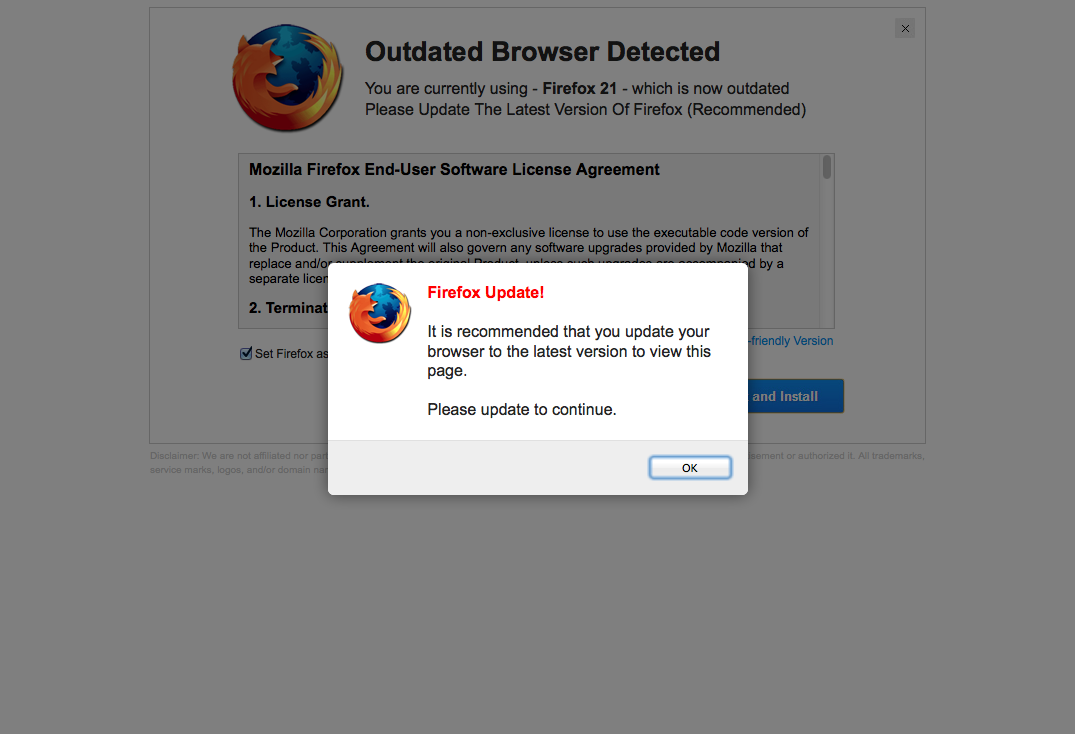
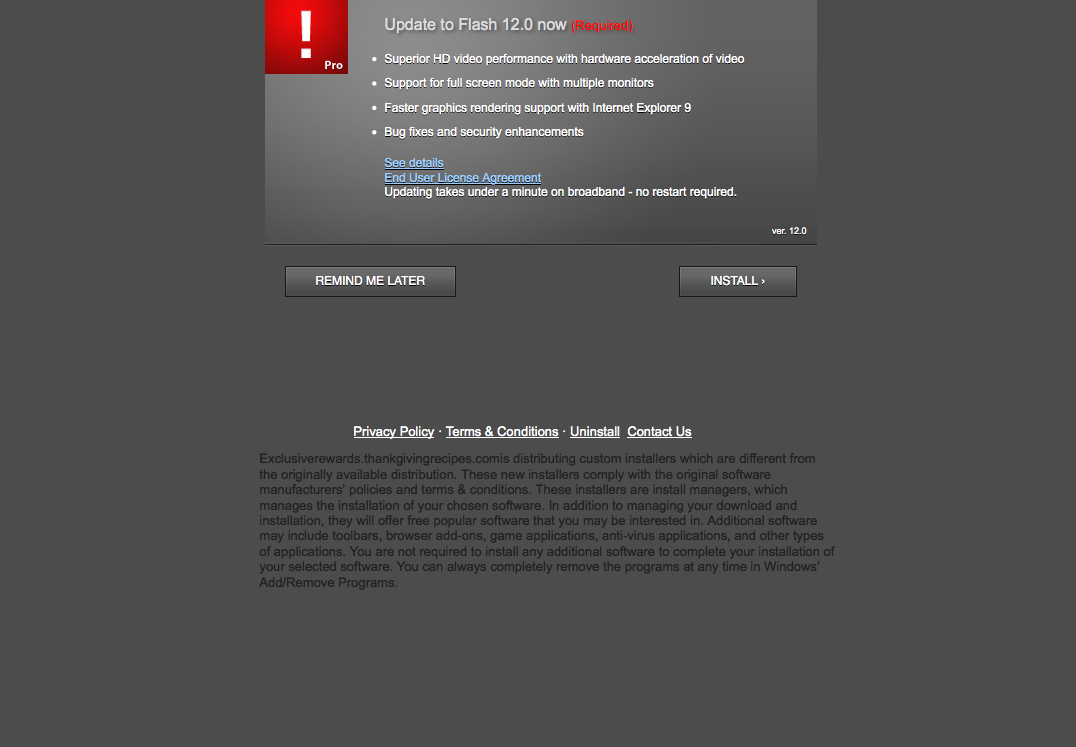
The above picture is the only visible addition to this page. After clicking on the link, the victim is immediately sent to a page that leads them to suspect their Browser/Flash version is not up to date.
These cases both resolve to one of two adware binaries being installed on the customer's system.
https://www.virustotal.com/en/file/a157438070a712bbd3c26ff9de26eb8013af7b18d63d6d707553e45e3369c2f2/analysis/1374266431/
https://www.virustotal.com/en/file/56eebb8067af1febd1ecb35b4ece27fab83200ba6d4e1815749decdcdad9eb1b/analysis/1374266466/
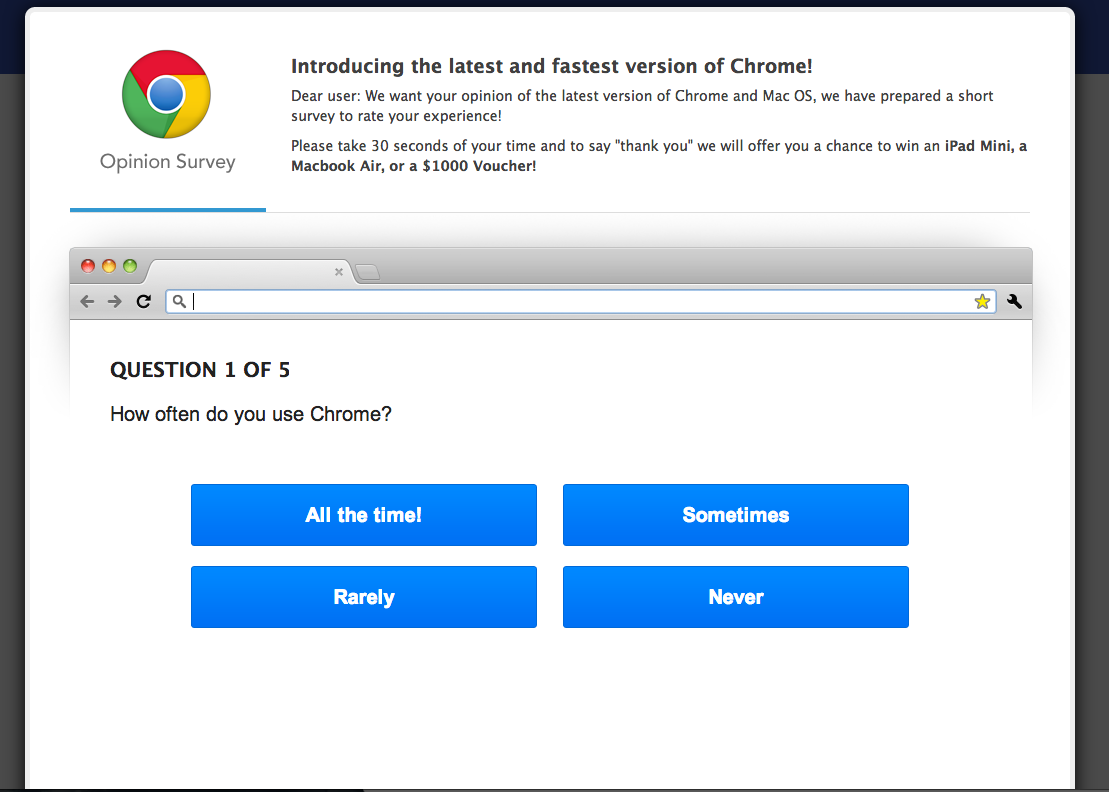
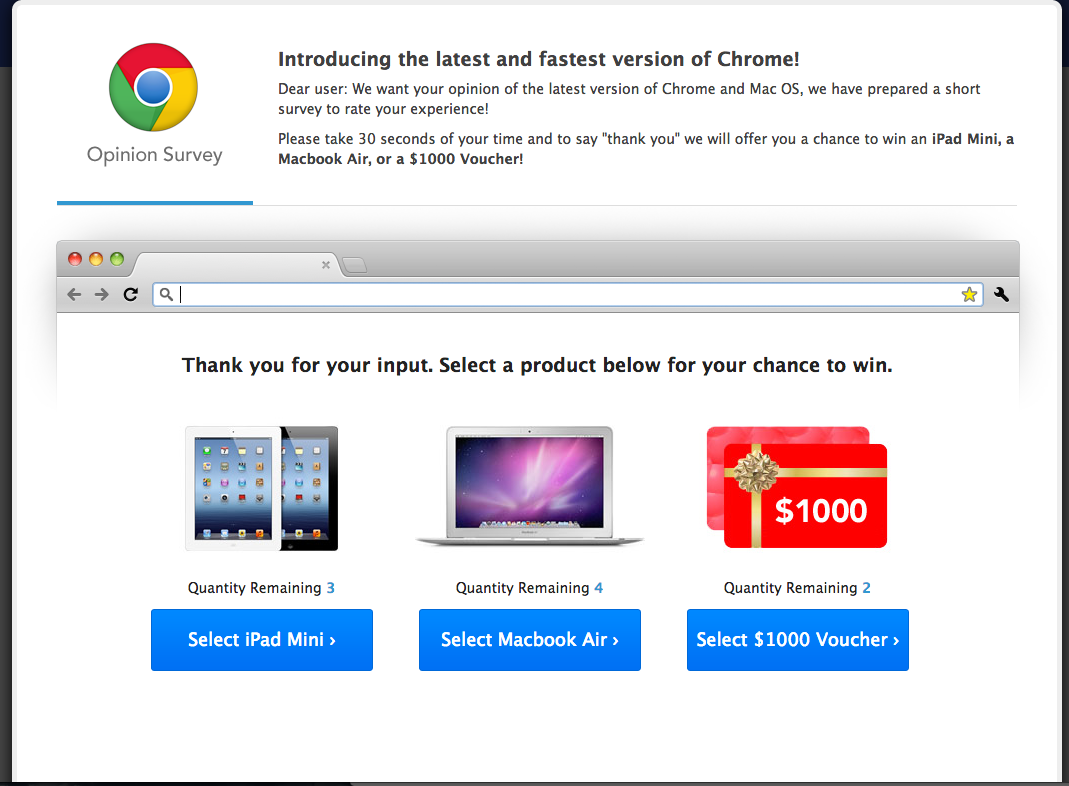
In other cases, the victim is only redirected to a pay-per-click scam that promises "Free Vouchers" and free Apple products, but fails to deliver.
Revisiting one such domain in the list will only lead the victim back to a parked domain page. This is done to discourage researchers from dissecting their threat to avoid meaningful detection from security vendors. The best idea to avoid misdirection from such phishing attempts would be to tighten up your browser security.
- 1yahoo.com/
- testflightapps.com/
- www.find-your-date.org/
- www.conmdirect.de/
- www.chanuteinsurancepool.net/
- translateitonline.com/
- compartel.gov.cofacebook.com/
- www.autobypass.com/
- rerbox.com/
- ravelrey.com/
- www.corall.com/
- accountservices.wiipro.com/
- losangeles.craigslst.org/
- www.styel.com/
- spritnpcs.com/
- www.nbarumors.com/
- www.eetime.com/
- bleacherrepot.com/
- www.elmundoe.es/
- iflswa.com/
- debshop.com/
- www.cnnis.com/
- myfintesspal.com/
- televisaeportes.com/
- www.testflightapps.com/
- wwwbunte.de/
- hiffingtonpost.com/
- bhestbuy.com/
- www.dbm.de/
- noobroom6.com/
- scripts.codingclick.com/
- eaterny.com/
- www.thatlantic.com/
- usnwwc.com/
- texasrangersmlb.com/
- idlebrian.com/
- laspass.com/
- spliwise.com/
- www.iflswa.com/
- www.usbankhomemortagage.com/
- www.linkdein.com/
- mdrudgereport.com/
- theeverywhereist.com/
- www.hiffingtonpost.com/
- redditt.com/
- www.saukaryam.com/
- malaimalar.com/
- www.bradypeople.com/
- bmohariss.com/
This immediately takes you to a seemingly random series of advertising scams. One of the scams presents a "Click Here To Enter"link.
 | |
| NO DON'T! |
These cases both resolve to one of two adware binaries being installed on the customer's system.
https://www.virustotal.com/en/file/a157438070a712bbd3c26ff9de26eb8013af7b18d63d6d707553e45e3369c2f2/analysis/1374266431/
https://www.virustotal.com/en/file/56eebb8067af1febd1ecb35b4ece27fab83200ba6d4e1815749decdcdad9eb1b/analysis/1374266466/
In other cases, the victim is only redirected to a pay-per-click scam that promises "Free Vouchers" and free Apple products, but fails to deliver.
Revisiting one such domain in the list will only lead the victim back to a parked domain page. This is done to discourage researchers from dissecting their threat to avoid meaningful detection from security vendors. The best idea to avoid misdirection from such phishing attempts would be to tighten up your browser security.