Recently, I had the pleasure of presenting on malicious browser extensions at SOURCE Seattle. I showed, amongst other things, how a malicious browser extension can be added silently to any Firefox profile. I've reworked the demonstration, and want to make it available to a wider audience.
3rd-party installation
You have probably already have encountered applications, like the Flash player or some repackaged free software, that wants you to install a toolbar or some spyware/adware for your browser. This is a 3rd-party installation of an extensions. For Firefox, this installation consists of copying the browser extension into your Firefox profile (or a special folder that contains extensions shared by all profiles).
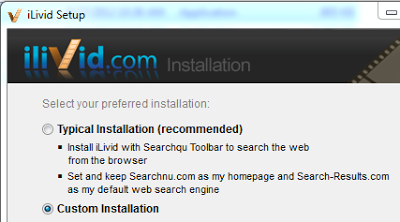 |
| Software installer contains a toolbar/adware/spyware extension |
Firefox protects against this type of external extension installation by prompting the user the next time the browser is started - the user has the option to disable (default action) or enable the new extension.
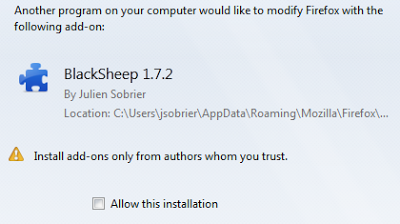 |
| Firefox warning for an extension installed outside of the browser |
Silent installation
It is actually very easy to bypass the warning from Firefox. Firefox stores information about all extensions in a Sqlite3 database named extensions.sqlite, located in each Firefox profile. It contains:
- name, version, description, etc.
- enabled or disabled
- active or not
- installed from official Mozilla extension site or not
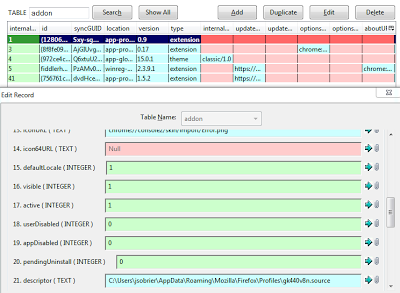 |
| extensions.sqlite |
When Firefox starts, it checks the list of extensions under /extensions/ against the content of extensions.sqlite. If an extension exists on disk, but is not listed in the database, a warning is shown. The trick to install an extension silently is to add a record into the database about the extension being installed and tell Firefox that the extension has actually already been approved by the user (active and enabled).
Demonstration
I've written a small program that installs an extension silently into any Firefox profile. You can download the program and the extension here, and the source code there.
The program was written in C# and can be compiled with the free Visual Studio Express for .Net from Microsoft.
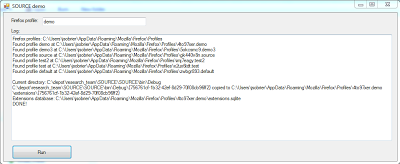 |
| Tool shows the steps to install the extension silently |
The "malicious" extension does not actually do anything. All the malicious code has been commented out, although it includes some of the things an attacker could do, such as:
- steal the list of logins and passwords saved
- send out all the URLs visited by the user
- disable security features
Do not worry about testing the "malicious" finctionality, the extension will not do anything - no information will be sent out.
I suggest that you create a custom profile to test the extension. To create a new profile named "demo", run the following command:
firefox -CreateProfile demo --no-remote
Then start Firefox with your new profile:
firefox -P demo --no-remote
I've included a video that shows the silent installation in case you're fearful of trying it for yourself:
Why it matters
Many free software packages push toolbars, adware and spyware into Firefox and other browsers, installed as part of their installation to earn some money for the extension creator (see previous PPI campaigns). Firefox gives users a chance to explicitly and clearly decide whether or not they want to enable these add-ons. Without this protection, many users can be tricked into running extensions they were are not aware of.
The second important point is that malicious browser extensions are much harder to detect once installed. Because extensions are part of the browser, their activity cannot be differentiated from the activity of the browser. Accessing the internet and accessing the file system are legitimate actions for the browser. The extension does not need to add itself to the startup scripts, or as a Windows service to be running after a computer reboot. The extension does not need to hook into Windows to intercept logins and passwords, etc. Finally, AV vendors struggle with detecting malicious JavaScript and any of the malicious Firefox extensions I've checked with VirusTotal were never flagged.
Going further
The silent installation could be even more sneaky. Instead of adding a new extension, it could also replace an existing extension, or append itself to an existing extension.





