It's quite depressing to see that Google still contains numerous links to spam pages which lead to fake AV sites. While there are fewer of them, they are still there. This, despite the fact that attackers have not significantly changed their techniques in many months. They still hijack vulnerable sites and create spam pages with similar URL patterns. The fake AV pages are mostly the same, using the same CSS and Javascript code and antivirus engines continually fail to detect the majority of the malicious executables.
Here is a typical example of what users will still encounter. The site casino-jugendclub.de has been hijacked to host thousands of pages like http://www.casino-jugendclub.de/lnsqo.php?page=jennifer-nettles-husband.
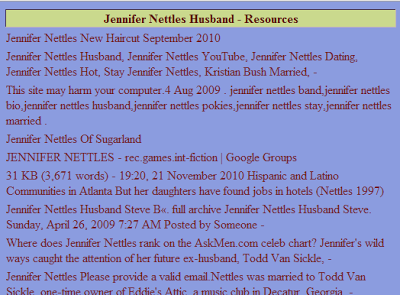 |
| Primitive, but effective, SEO spam page |
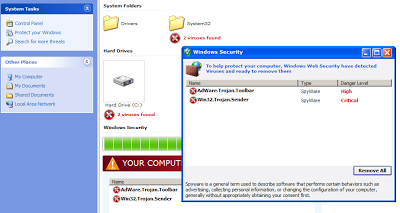 |
| Fake AV page |
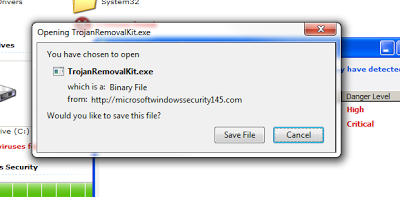 |
| Malicious executable disguised as an antivirus |
Not much has changed in the past 6+ months in the world of malicious spam SEO. While Google has made efforts to combat the fake AV sites and the number of malicious spam links in popular Google searches has gone down somewhat, more needs to be done.
-- Julien





