The term “viral” is most commonly associated with consumer-related content, apps, etc., that rapidly grow in popularity as they spread from one person to the next. But pioneering enterprise software companies have also been able to leverage virality to achieve high growth. One of the earliest successful examples was when Dropbox offered free storage space in exchange for referrals. Then came Slack, growing via word of mouth with no particular incentive other than the ability to communicate with colleagues in a compelling new way.
More recently, cloud platforms, such as AWS, GCP, and Azure, have enjoyed similar “viral” effects inside organizations. Sure, many enterprises have progressive leaders who have embraced a “cloud-first” model, but for others, the growth of cloud has been organic and user-led, much like Dropbox and Slack's early days. While cloud platforms bring a range of benefits to organizations and users alike, they can also introduce challenges to networking and security teams. Let's review the seven reasons why securing rapidly expanding cloud activity has become overly complex and ineffective.
1. It starts with a relatively simple deployment in a single AWS region, spun up for a new project by an application development team. Unfortunately, well-intentioned developers often miss basic security configurations, leaving this environment susceptible to breach.
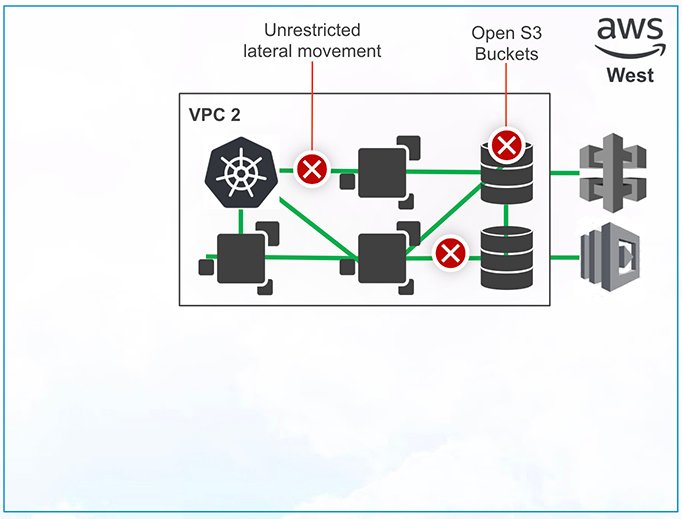
2. A new developer joins the team from a cloud-first startup that had widely adopted AWS but hadn’t done much to enforce security. Because the environment is user-controlled, this developer spins up a new, previously unknown VPC with no security policies applied to it.
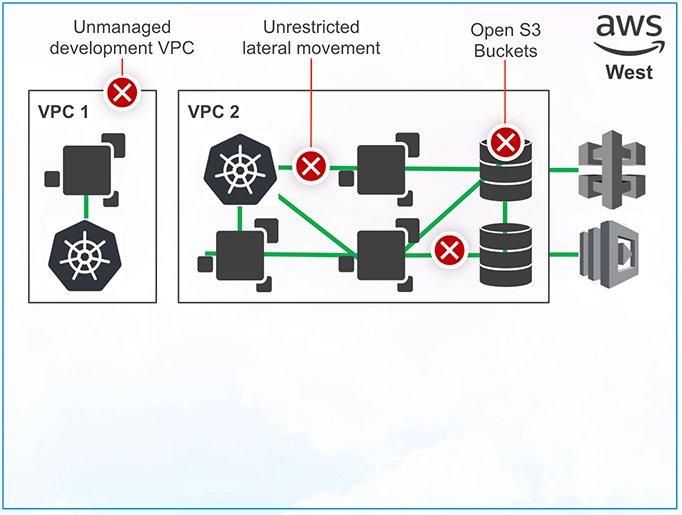
3. New security components get added to manage the traffic between these VPCs. Everything is in the same region and has no external connectivity so, despite a bumpy start, this deployment is still relatively simple.
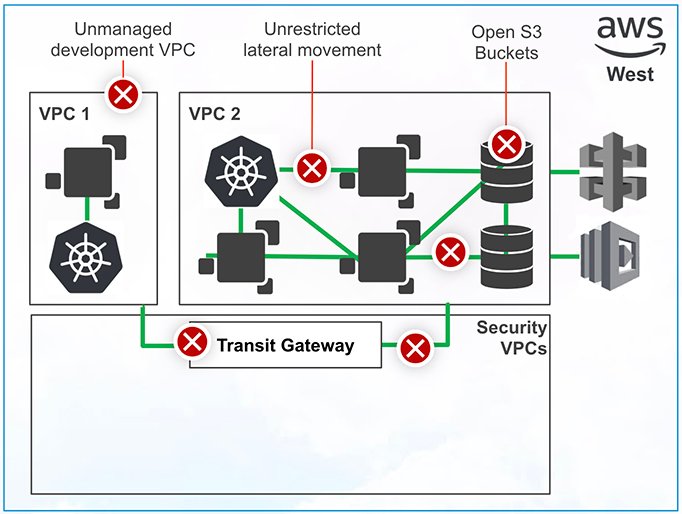
4. The organization decides to make the applications and the environment accessible to a broader range of users, which means the addition of several security appliances to the environment, including multiple virtual firewalls and VPNs. This is where things really start to get complicated—managing static, network-based policies and dealing with the scaling limitations of IPSec VPNs.
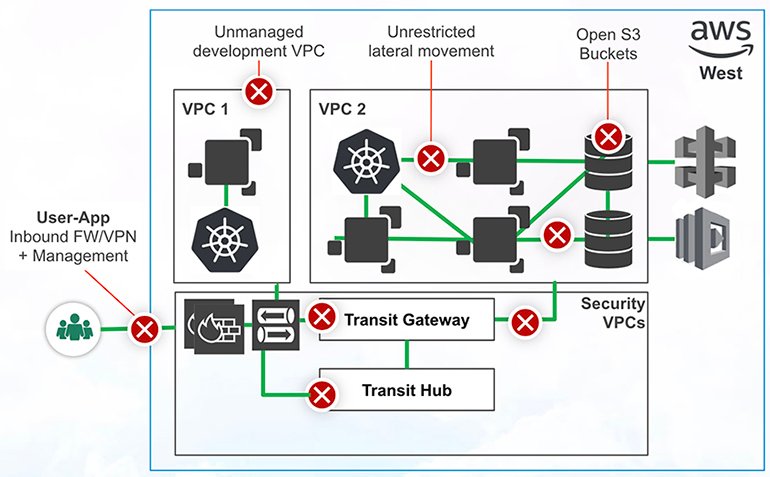
5. Several of your now-growing inventories of workloads need internet access for things like software updates and API connections to third-party services. Of course, you want to protect your environment from malicious software and other internet-based threats, so you put up more virtual firewalls, increasing management time and overhead.
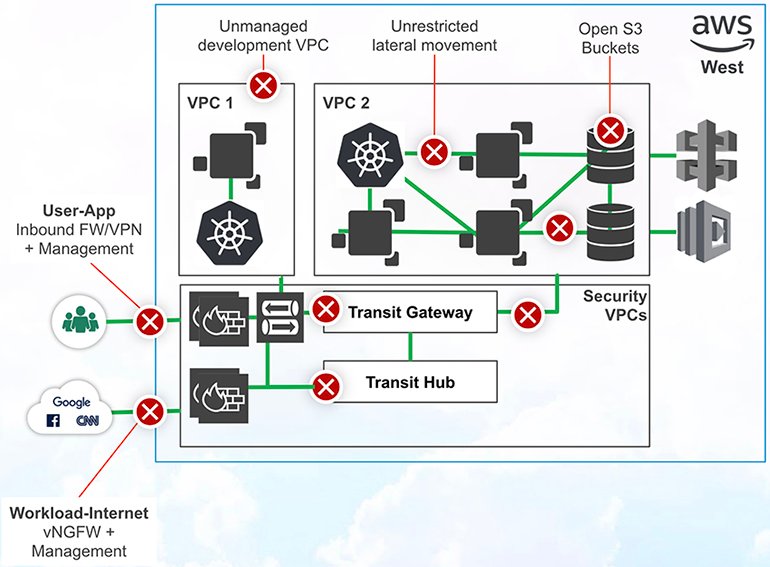
6. As your cloud environment grows further, you also add more regions and start to deploy to other cloud platforms. This expansion leads to more vFW policies, more IPSec VPNs, and even more complication, because now you’re dealing with not one, but multiple cloud platforms, each of which has its own way of dealing with connectivity and security services.
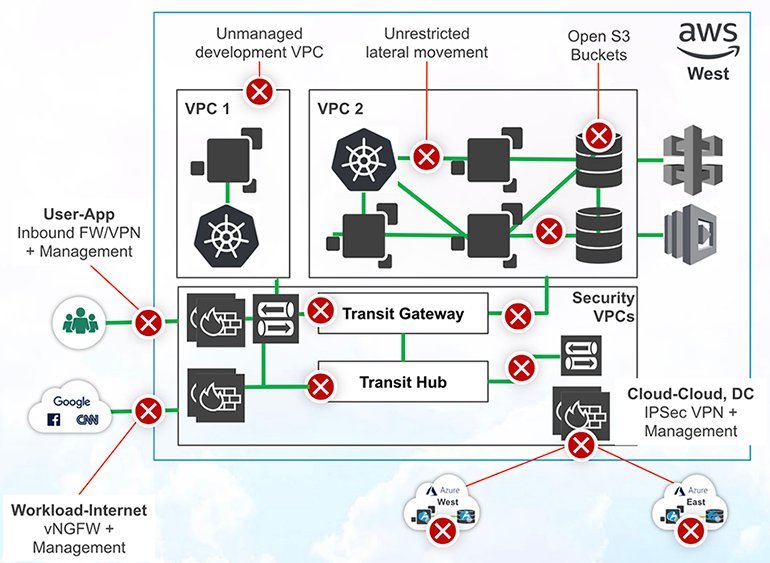
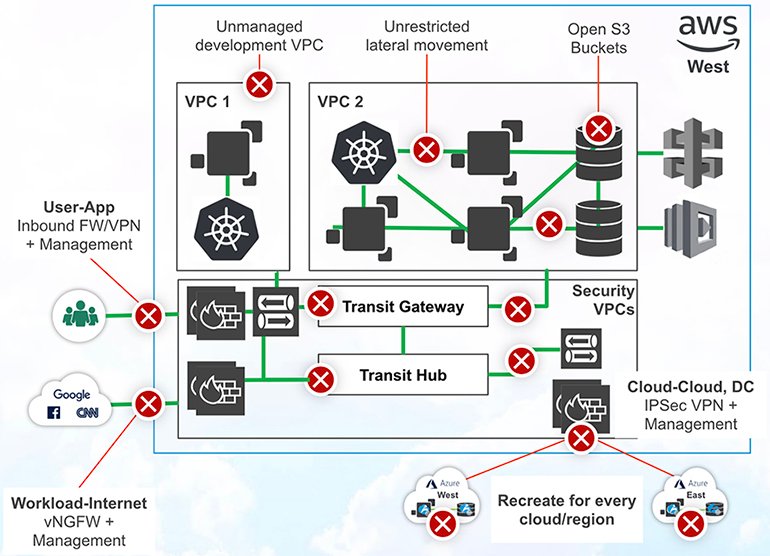
7. Now that you’ve deployed into other cloud platforms, you need to recreate your build-out of security from scratch, ensuring that your new environment is locked down just like your original deployment.
A better approach
Zscaler Cloud Protection (ZCP) was built to take the work out of securing cloud workloads. The solution is designed to deliver the same high performance, globally distributed reliability that you’ve come to trust from Zscaler. ZCP is deployed via easy-to-understand business-level policies and a simplified security stack, resulting in better security, a 90 percent reduction in policies, 90 percent fewer services to manage and maintain, and cost reductions of 30 percent or more.
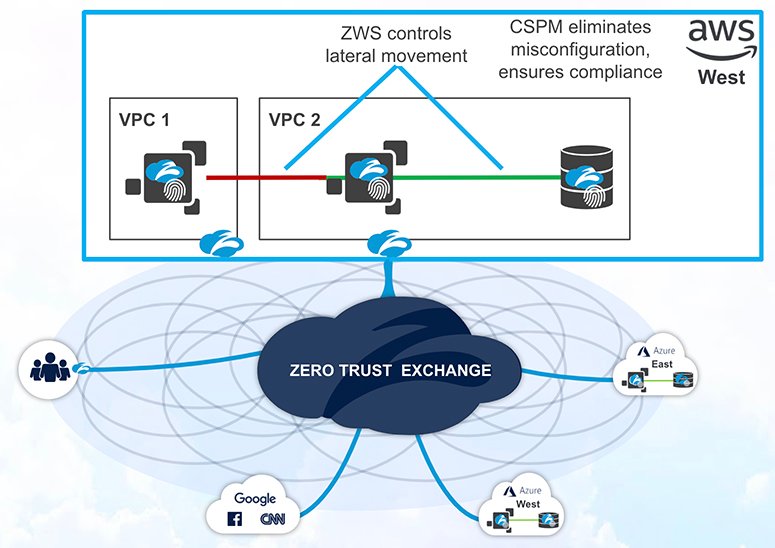
Complexity is the enemy of security
It’s long been said that complexity is the enemy of security, but most organizations have found it too difficult to unwind the complexity that has built up over time in their on-premises and data center environments. The move to the cloud is your once-in-a-career opportunity to eliminate complexity from your environments.
A cloud protection platform based on zero trust is the way to do that. Zscaler can help you get there.






