This post also appeared on LinkedIn.
When I worked in the area of network and security architectures in a previous life, we’d plan, assess, and make IT decisions right after the new year. Now that we are approaching the end of the global lockdown, I think most IT departments are asking a lot of questions: what have we done rightly, wrongly, and what can we take away when moving forward.
If I were still doing my old job, I would capitalize on the changes IT made that allowed people to successfully and securely work outside of the corporate office. Mass remote work made IT teams realize that legacy network security perimeters don’t scale well when rolling out work-from-home solutions—especially for traffic-heavy apps like Microsoft 365 (M365). Besides increased backhaul costs, tunneling all M365 traffic through branch or headquarter security perimeters drastically reduces performance and can cause M365 deployments to fail.
The legacy problem
Enterprise modernization is top of mind for CIOs. For many, M365 rollout and improved productivity in an increasingly geographically diverse environment are ongoing projects. Enterprise-wide adoption of M365 requires a serious review of how network architecture processes and secures traffic. Microsoft recommends breaking out M365 application traffic quickly and with no security (they promise that they are a secure source). But for most organizations this is a non-starter:
- They have a hub-and-spoke model that processes all branch traffic (including remote employees).
- They can’t use a split tunnel architecture or breakout locally (e.g., via SD-WAN).
- They have sacrosanct and legacy security policies.
In traditional hub-and-spoke models, all internet traffic travels from the user, over the corporate network, and out towards the internet. Adding M365 creates an overwhelming amount of application traffic—even with many corporate HQs boasting “large pipes.”
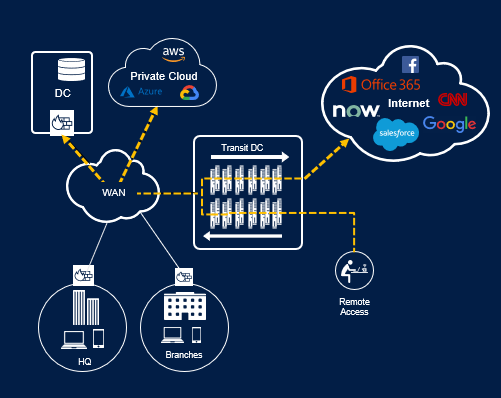
Figure 1. Perimeter security processing traffic before it heads to an internet destination.
Beyond day-to-day M365 usage traffic, application updates for hundreds if not thousands of users can easily overwhelm enterprise infrastructure’s capacity. IT teams’ frustration when fighting to maintain employee productivity when using “productivity” software is understandable—and not a particularly good look for an M365 rollout in general.
Simply scaling existing physical network capacity isn’t a good solution, either. Doubling the size of your physical network architecture capacity often means doubling the size of your WAN OPEX spend (not to mention the CAPEX cost of new equipment). It doesn’t solve the problem long-term (given Moore’s Law, you’ve put it off for a year, maybe), and you aren’t winning any executive friends or building executive team trust. It can cause M365 deployments to fail before they start.
Moving forward
I have a better answer: use the internet as your network. One of the (very few) upsides of the pandemic is proof that using the internet as the corporate network is a secure transport solution.
COVID-19 forced companies to send all employees to work from home. In essence, these home offices became “branches of one.” When remote traffic flooded legacy enterprise networks via these “branch” office connections (often over VPN), application and network performance took a hit. The better move is to let remote users access cloud applications directly from their local internet connections. But you need to secure those direct connections.
Many companies solved the problem by coupling direct internet access with inline cloud security. With direct internet access, it’s unnecessary to backhaul traffic through complex perimeter security stacks, no matter where the users or applications sit. Instead, it can use the internet to directly connect to applications. Traffic is sent directly and securely to its destination, eliminating the need for backhaul, reducing latency, and removing complex security stacks at the HQ or branch edge.
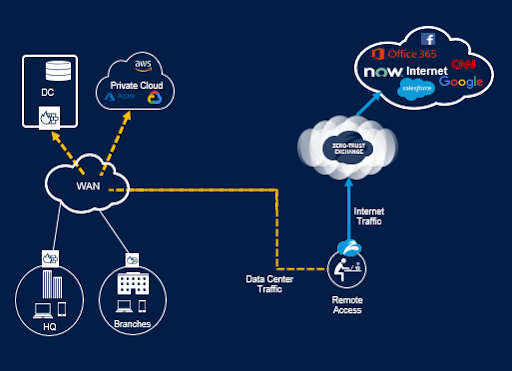
Figure 2. Direct internet connectivity for Internet and SaaS workloads
Using an inline security solution:
- Offloads internet traffic from the network (up to 60% of your traffic is bound for the internet) using local internet as your transport layer
- Reduces latency by sending cloud-application traffic directly to the cloud
- Reduces MPLS traffic and associated costs
- Provides corporate-perimeter-level security to remote users
- Increases visibility into user and workload activity for security and performance optimization.
The pandemic made remote workers an ideal test case for accelerating M365 rollouts by successfully showing that direct internet access can provide an “on-premises” experience no matter where users work. You can apply this test case to examine where direct internet connections could be a better solution than legacy architecture.
With most users working remotely and creating more traffic for your WAN/MPLS connections, an inline cloud security solution lets you adopt the internet as a critical element in your connectivity strategy.
It’s crucial to analyze your overall enterprise security strategy and work in conjunction with the various infrastructure teams to examine what guidelines, restrictions, and governance might limit immediate action. Determine if a cloud security solution that allows direct internet access to cloud applications allows for more local internet breakouts.
Gartner describes a “Thin Branch/Heavy Cloud” model based on a Secure Access Service Edge (SASE) architecture, where security is pushed out of the physical network and into the cloud. Keep this model as your guide, and don’t over-complicate your network with unnecessary products if you can simply forward traffic directly to the internet.
Zero trust eliminates legacy dependence
A zero trust cloud security solution can help you easily make the most out of productivity software investment and pandemic response solutions and help accelerate M365 adoption. You have to work closely with networking, end-user, and security teams to identify solutions that can simplify network and security architectures using SASE solutions.
By offloading traffic from your network to the internet securely, you can reduce dependence on legacy networking and security architectures. That means accelerated M365 adoption, greater productivity, and, ultimately, better business outcomes. The vast number of remote employees is an unprecedented opportunity—make them your test case that demonstrates a successful direct-to-internet M365 deployment. They can be the critical mass that highlights how the internet can be your your transport layer, and accelerate your secure digital transformation.





